Malicious software family classification avoidance method based on deep reinforcement learning
A reinforcement learning and malware technology, applied in neural learning methods, computer parts, instruments, etc., can solve problems such as large amount of calculation and complex model training process, and achieve the effect of low training cost, easy implementation, and easy implementation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
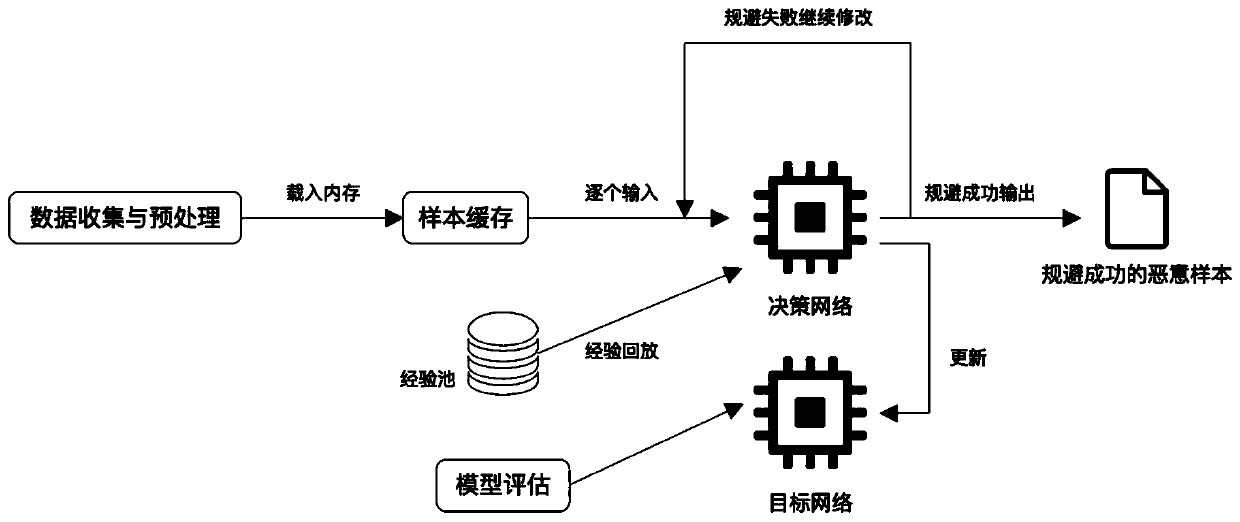
[0048] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. Such as figure 1 Shown, the present invention a kind of malicious software family classification avoidance method based on deep reinforcement learning, comprises the following steps:
[0049]Step 1: Collect virus samples. The samples are different PE format samples from Backdoor, Dos, Email, Exploit, Net-worm, Rootkit, Trojan, Virus, Worm and other malware families based on the Win32 platform. Use the Python-based lief analysis library to analyze the selected samples, delete the samples with errors in lief analysis, and complete the data cleaning work. In order to reduce disk IO operations and improve training speed, all samples are cached before training, and all the binary data of the samples are read into the memory. When obtaining the status of the file during training, it is directly read from the memory.
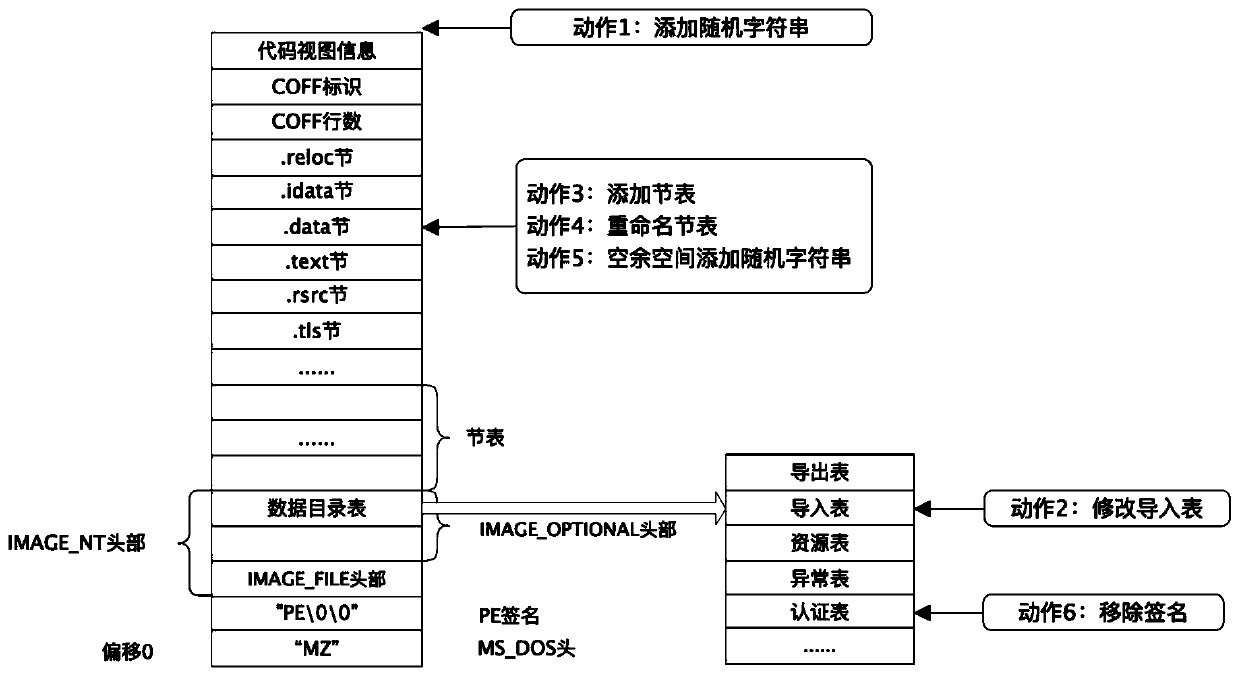
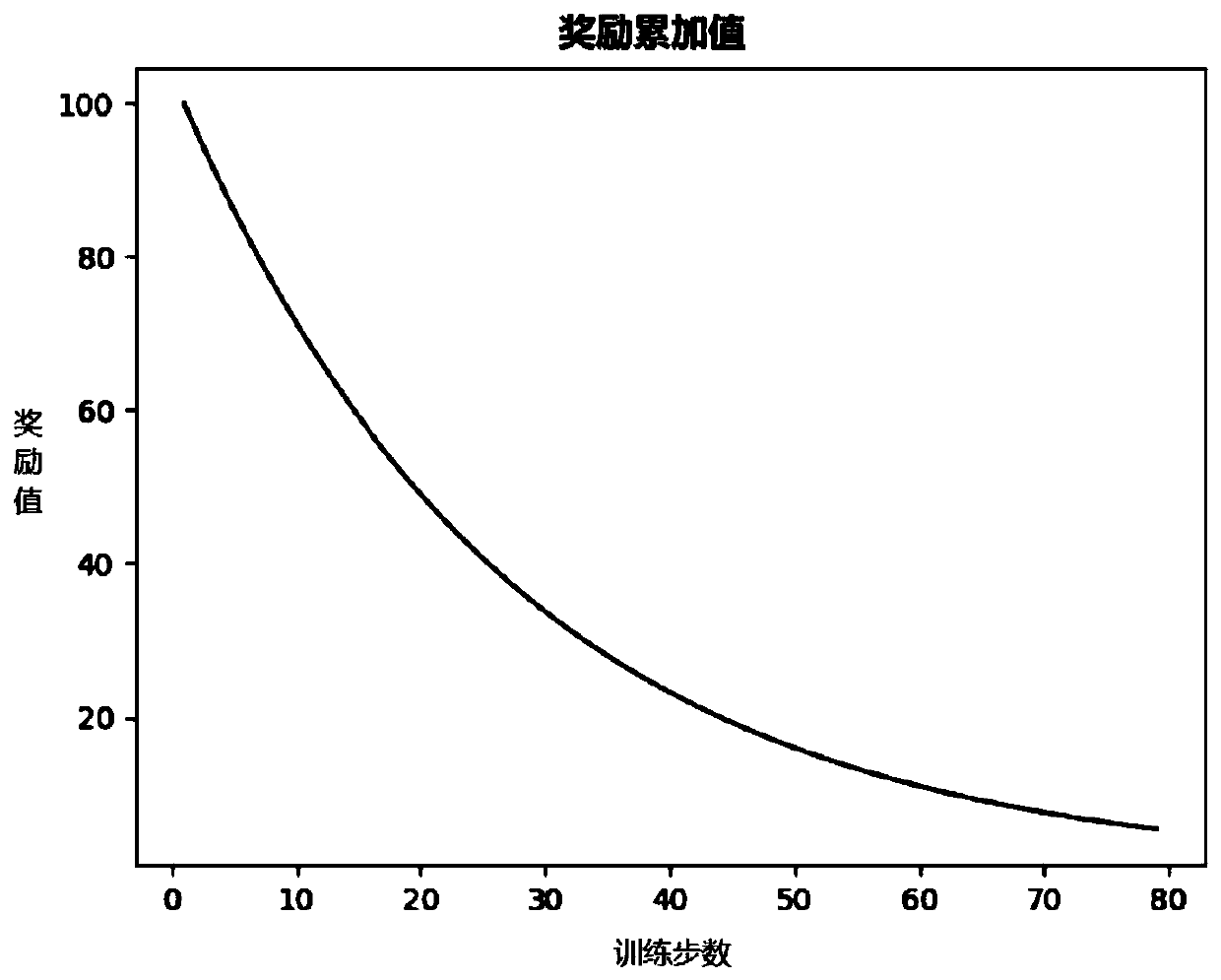
[0050] Step 2: Constru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com