An automated mining method for binary security vulnerabilities
A binary and vulnerability technology, applied in computer security devices, instruments, calculations, etc., can solve the problems of unguaranteed code coverage and low efficiency of dynamic analysis implementation, and achieve fast speed, improved accuracy, and high code coverage Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
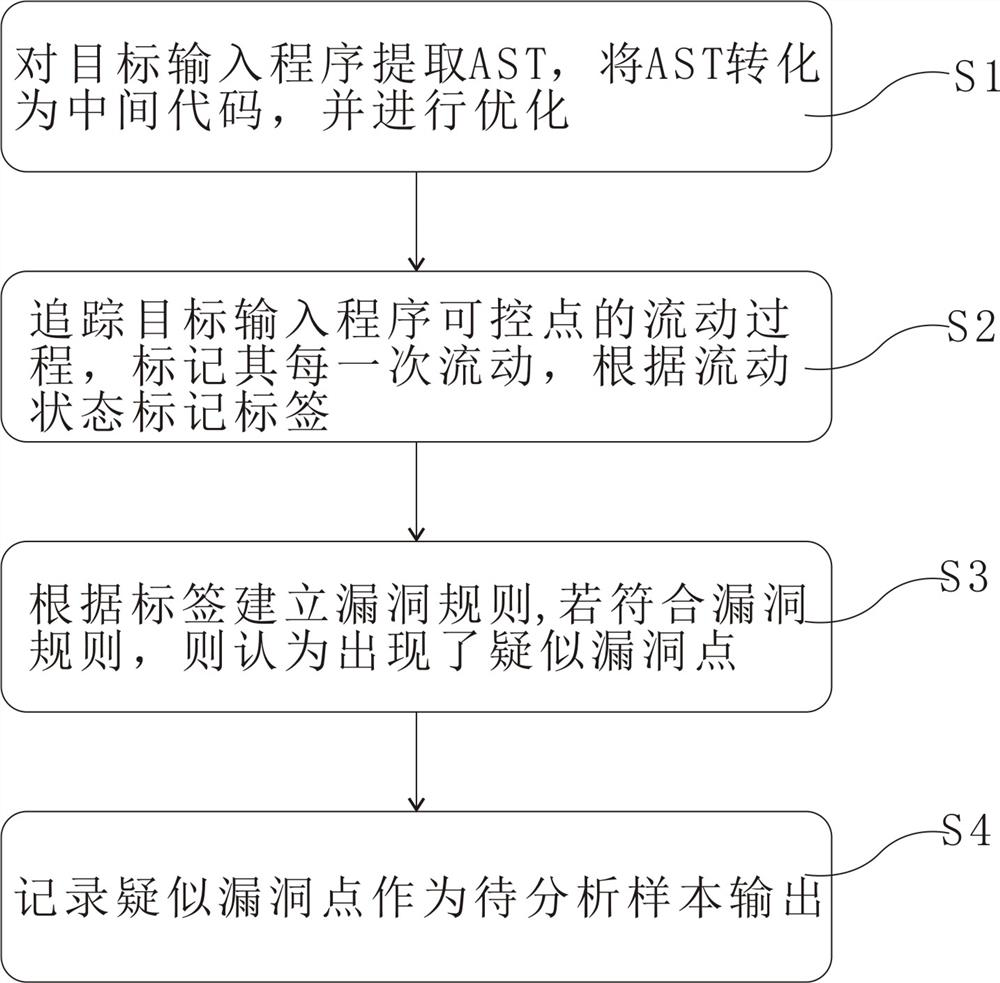
[0030] Such as figure 1 As shown, the present embodiment provides a binary security vulnerability automatic mining method, which includes the following steps:
[0031] S1. Extract AST from the target input program, convert AST into intermediate code, and optimize it. Specifically, the optimization is to make the intermediate code easier to analyze through optimization methods such as local register allocation optimization;
[0032] S2. Track the flow process of the control point of the target input program, mark each flow, and mark the label according to the flow state;
[0033] S3. Establish a vulnerability rule according to the label. If the vulnerability rule is met, it is considered that a suspected vulnerability point has occurred; the vulnerability rule described in this embodiment includes the order of the label, that is, the flow direction of the data can be judged by the order of the label;
[0034] S4. Record suspected vulnerability points as output samples to be an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com