Firewall security policy automatic adaptation system and method
A firewall strategy and security strategy technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as non-compliance with security inspections, increased service life of firewall equipment, and impact on firewall operating efficiency and resource utilization. Less effort, less readability effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0023] Embodiment 1, this embodiment provides a firewall security policy automatic adaptation system;
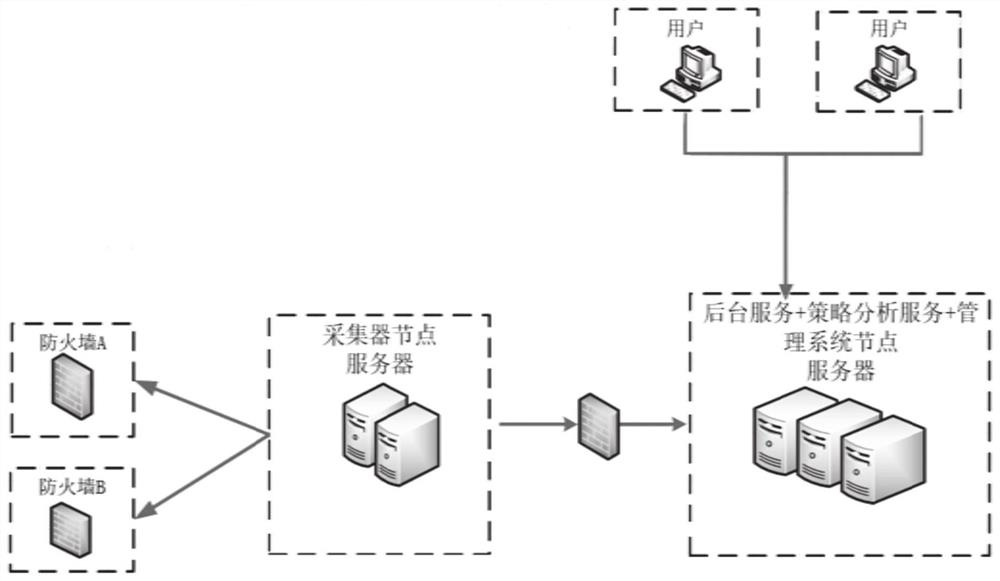
[0024] like figure 1 As shown, the firewall security policy automatically adapts to the system, including:
[0025] a collector, configured to collect policy configuration information of the firewall, and upload the collected policy configuration information of the firewall to the server;
[0026] The server is used to analyze the policy configuration information of the firewall uploaded by the collector, judge whether the policy configuration information of the current firewall has been updated, and output and display the judgment result.
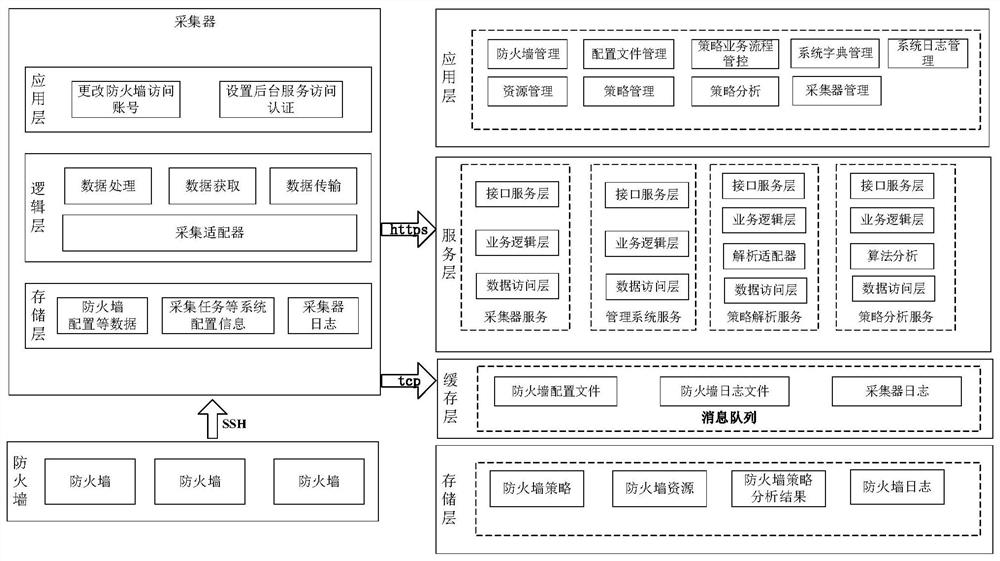
[0027] As one or more examples, such as figure 2 As shown, the collector includes:
[0028] The first storage layer is configured to: store policy configuration information of the firewall, configuration information of collection tasks and collection logs;
[0029] The first logical layer is configured as follows: the firewall polic...
Embodiment 2
[0073] Embodiment 2. This embodiment provides a method for automatically adapting a firewall security policy;
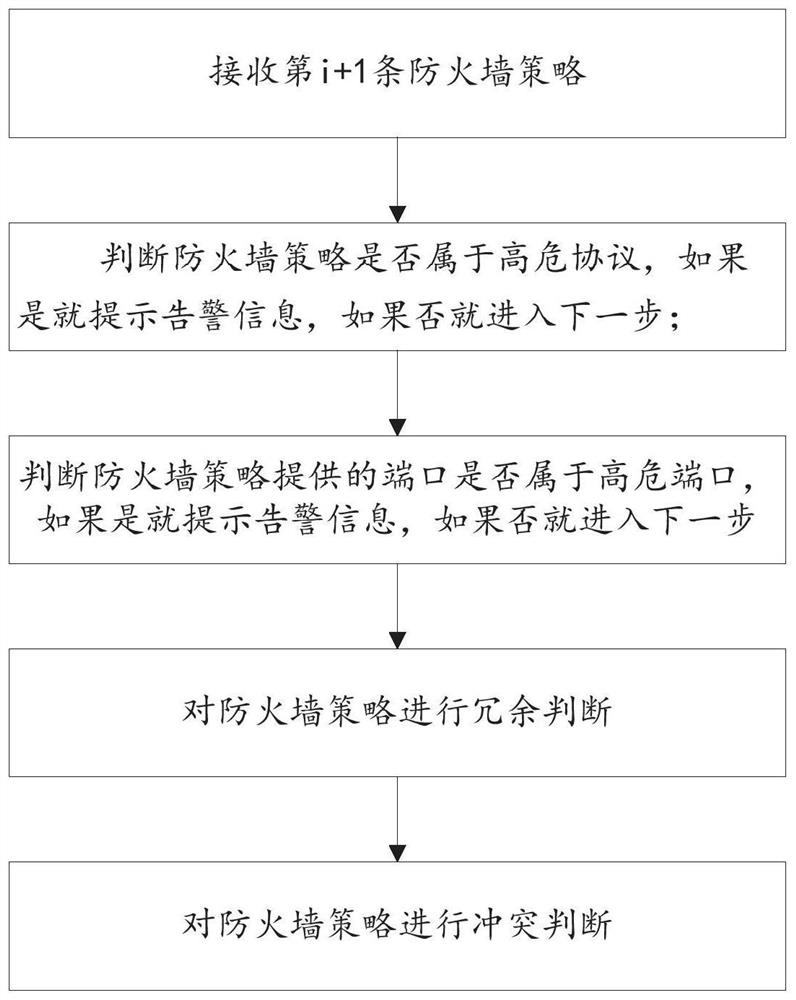
[0074] Firewall security policy automatic adaptation method, including:
[0075] S1: collecting policy configuration information of the firewall; the policy configuration information of the firewall includes: a security policy, a routing policy or a NAT policy of the firewall;
[0076] S2: Analyzing the collected firewall policy configuration information;
[0077] S3: Normalize, store and display the parsed data.
[0078] As one or more embodiments, in S1, the policy configuration information of the firewall is collected; the specific steps include:
[0079] S11: The collector matches the collection commands of various strategies from the command configuration library according to the brand, model and version number of the firewall;
[0080] S12: Remotely connect to the firewall through SSH, execute the collection commands of different strategies in the set order,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com