Vehicle-mounted network flow anomaly detection defense method and defense system based on information entropy
A vehicle network and traffic anomaly technology, which is applied in the field of vehicle network traffic anomaly detection and defense methods and defense systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
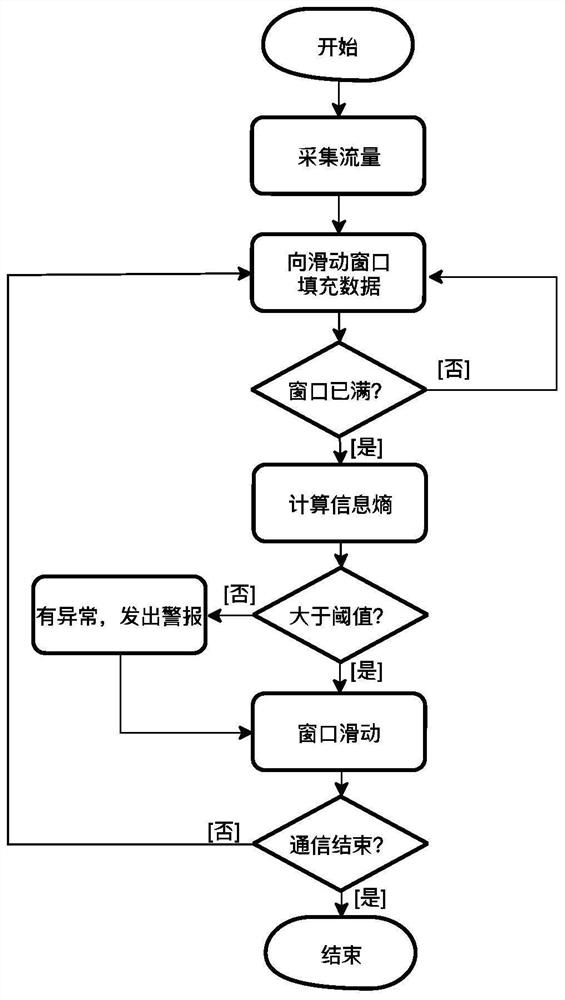
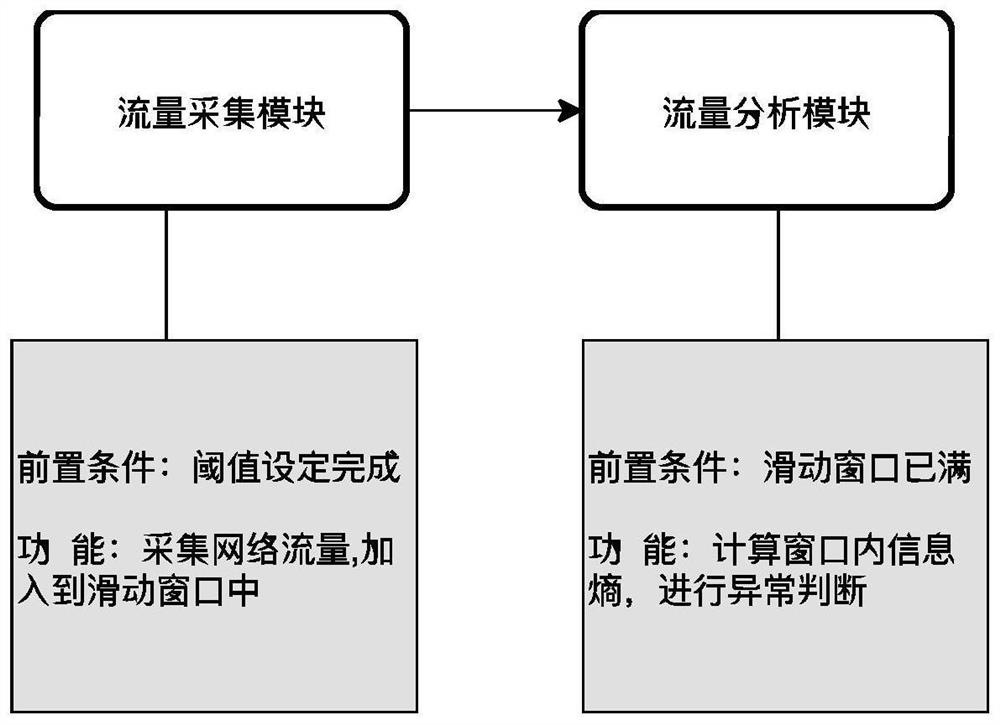
[0032] The CAN bus message and vehicle Ethernet traffic are collected separately through a fixed-size sliding window, the information entropy is calculated for the traffic data in the window, and the calculated entropy value is compared with the preset threshold to detect whether there is an abnormality. Raise an alert if an anomaly occurs, as described below:
[0033] Step 1: Set the sliding window, the setting rules are as follows:
[0034] Step 1.1: Set the maximum tolerable delay maxTime for anomaly detection, and calculate the flow rate v, then the size range of the sliding window is Set a sliding window with a larger capacity as much as possible within this range, and the fixed window size is W;
[0035] Step 1.2: Set the window sliding distance to W / 2.
[0036] Step 2: Set the threshold, the specific steps are as follows:
[0037] Step 2.1: For CAN messages, calculate the information entropy CANEntropy in the window under normal traffic multiple times 1 , CAN Entro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com