Data transmission method and device
A data transmission and data technology, applied in the field of information security, can solve problems such as the inability to guarantee the integrity and security of data transmission, endangering the security of users' accounts and property, and reducing data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
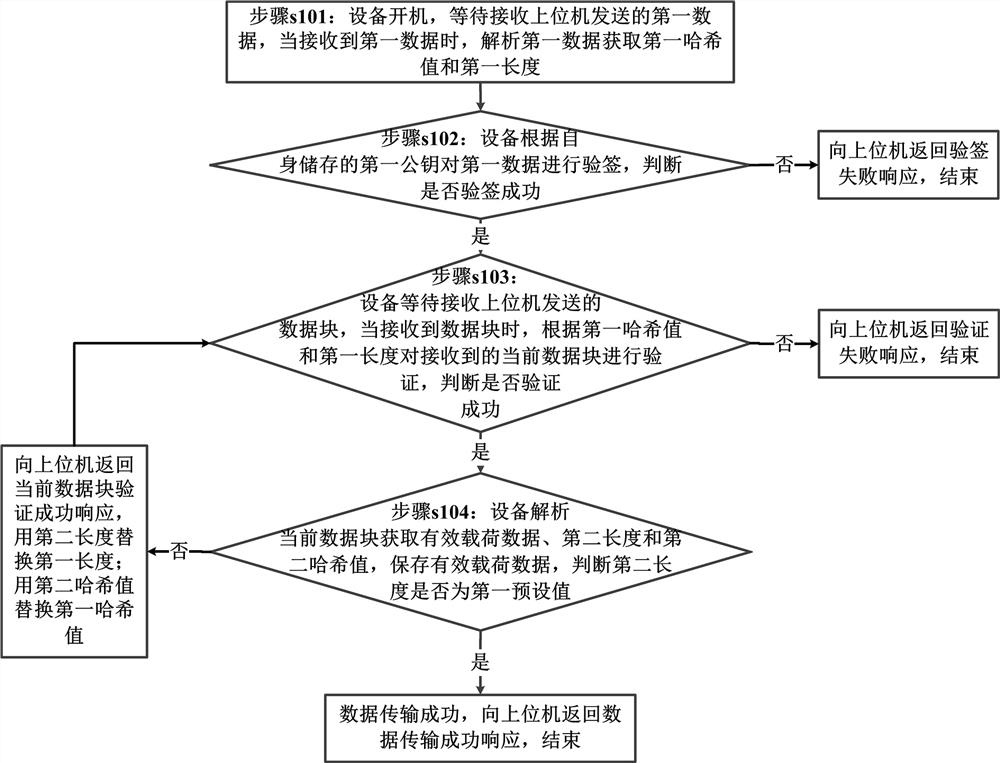
[0054] According to Embodiment 1 of the present invention, a data transmission method is provided, such as figure 1 shown, including:
[0055] Step s101: the device is powered on, waiting to receive the first data sent by the host computer, and when the first data is received, parse the first data to obtain the first hash value and the first length;
[0056] Optionally, step s101 is specifically: turn on the device, wait to receive the data header sent by the host computer, and when the data header is received, parse the received data header to obtain the first hash value, the first length, the first signature value, Initialization Vector (ICV) and First Content Hash;
[0057] Optionally, the first hash value is the hash value of the next data block in the data to be transmitted; the first length is the length of the next data block in the data to be transmitted; the first signature value is the private key for the upper computer The signature value obtained by signing all t...
Embodiment 2
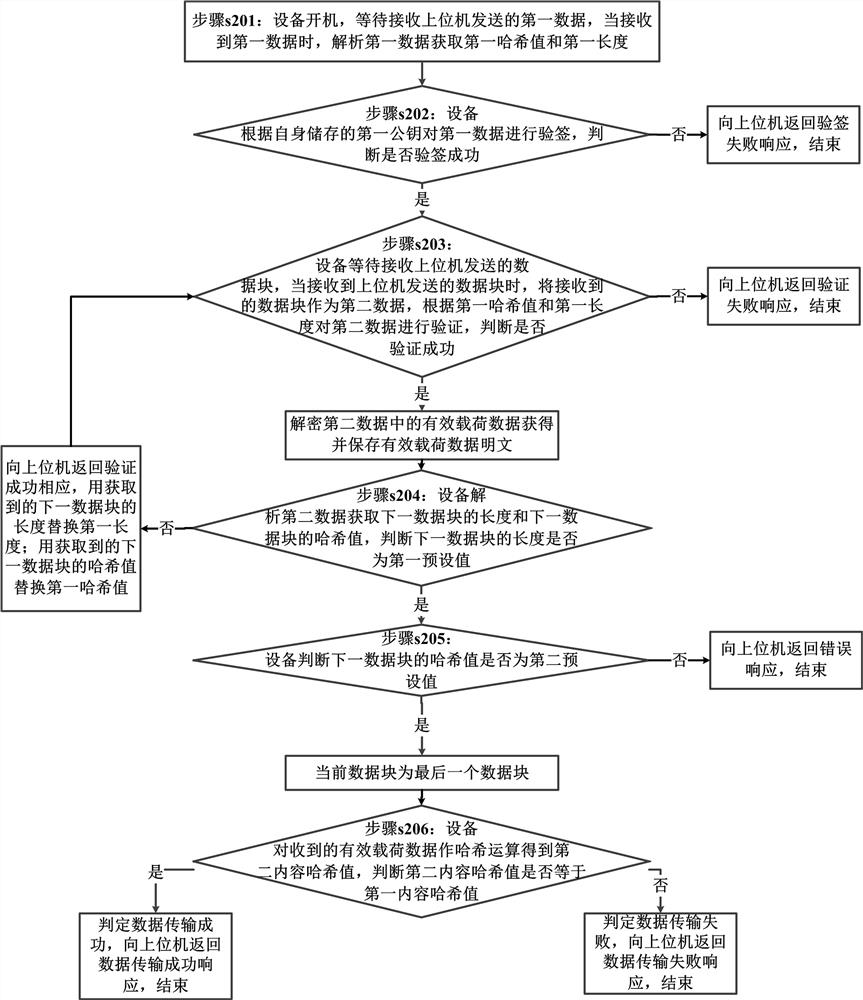
[0077] According to the second embodiment of the present invention, a data transmission method is provided, such as figure 2 shown, including:
[0078] Step s201: the device is turned on, waiting to receive the first data sent by the host computer, and when the first data is received, parse the first data to obtain the first hash value and the first length;
[0079] Optionally, step s201 is specifically: turn on the device, wait to receive the data header sent by the host computer, and when the data header is received, parse the data header to obtain the first signature value, and obtain the hash value of the next data block as the first hash value. Hash value, get the length of the next data block as the first length, get the ICV and the first content hash value (ContentHash);
[0080] Among them, the first signature value is the signature value obtained by signing all the data after the first signature value stored in the data header with the private key of the upper compu...
Embodiment 3
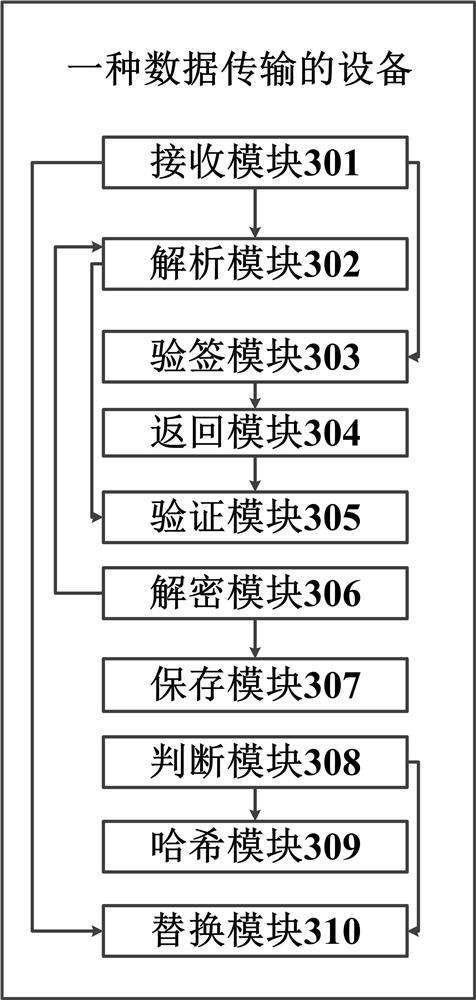
[0100] According to Embodiment 3 of the present invention, a device for data transmission is provided, such as image 3 shown, including:
[0101] The receiving module 301 is used to receive the first data sent by the host computer after the device is turned on;
[0102] A parsing module 302, configured to parse the first data to obtain a first content hash value, a first hash value, and a first length when the receiving module 301 receives the first data;
[0103] The signature verification module 303 is used to verify the first data received by the receiving module 301 according to the first public key stored in the device itself, determine whether the signature verification is successful, and trigger the return module 304;
[0104] The return module 304 is used to return the signature verification success response to the host computer when the signature verification module 303 judges that the first data signature verification is successful; Return signature verification f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com