A device authority authentication method based on web browser
A web browser, authority authentication technology, applied in the direction of digital data authentication, etc., can solve the problem of inability to judge the uniqueness of the device, and achieve the effect of strengthening specificity and diversity, and increasing security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
The authentication key is stored in the result and stored in the authentication server.
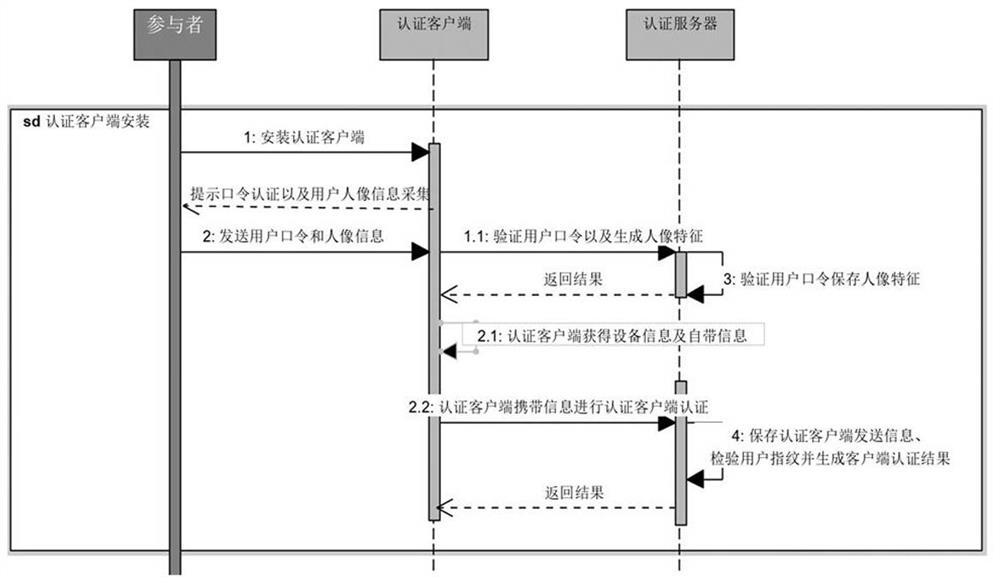
In the installation process, the authentication client prompts the user to perform user password authentication, which can prevent the authentication client from arbitrarily
Install to avoid unnecessary losses for users.
[0047] During the installation process of the authentication client, the number of authorized devices can be controlled, enabled or
Disable the use of the device and the effective time control of device use, verify changes in portrait information, etc.
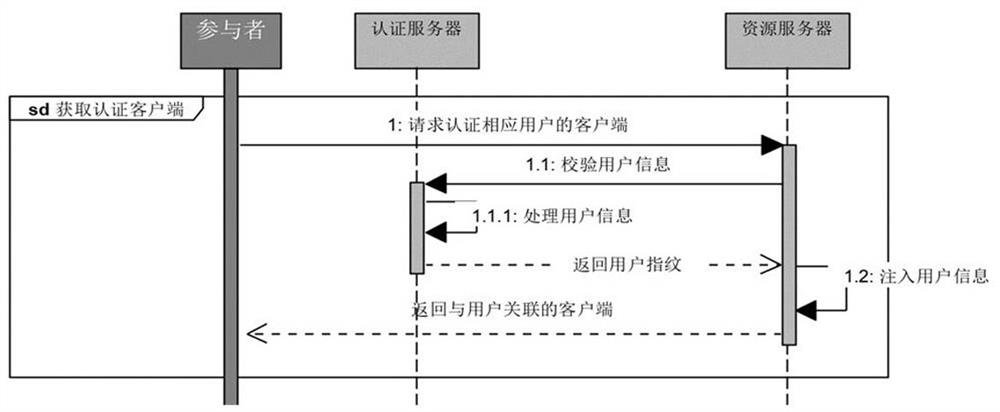
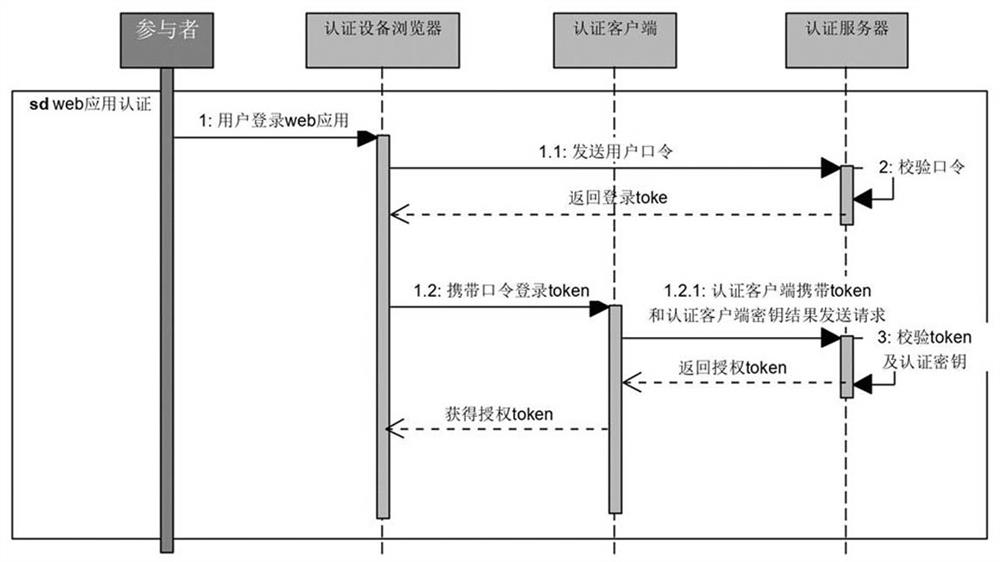
As shown in Figure 3, the concrete process that browser obtains authentication is:
S06), the user logs in the web application in the browser of the authentication device by using the password, and the authentication server checks
After the verification is passed, the user login information userToken is returned to complete the user password login;
[0050] S07), the authentication device browser carries a userToken t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com