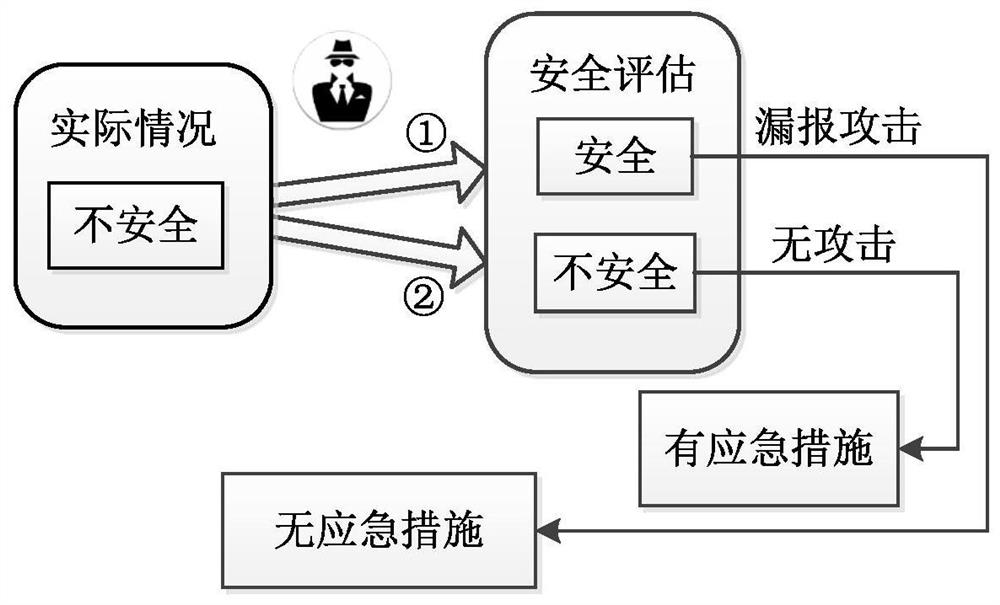
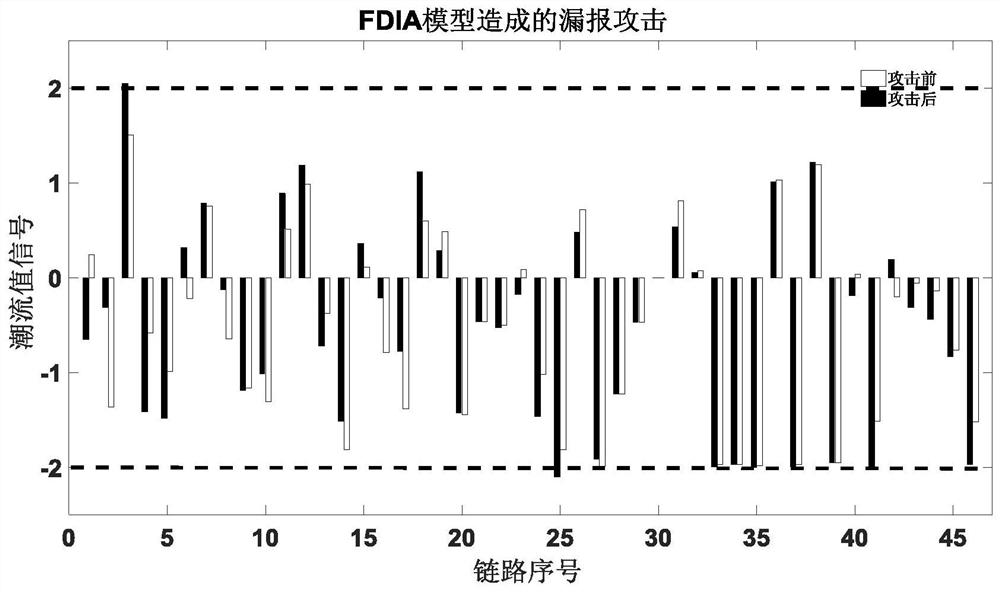
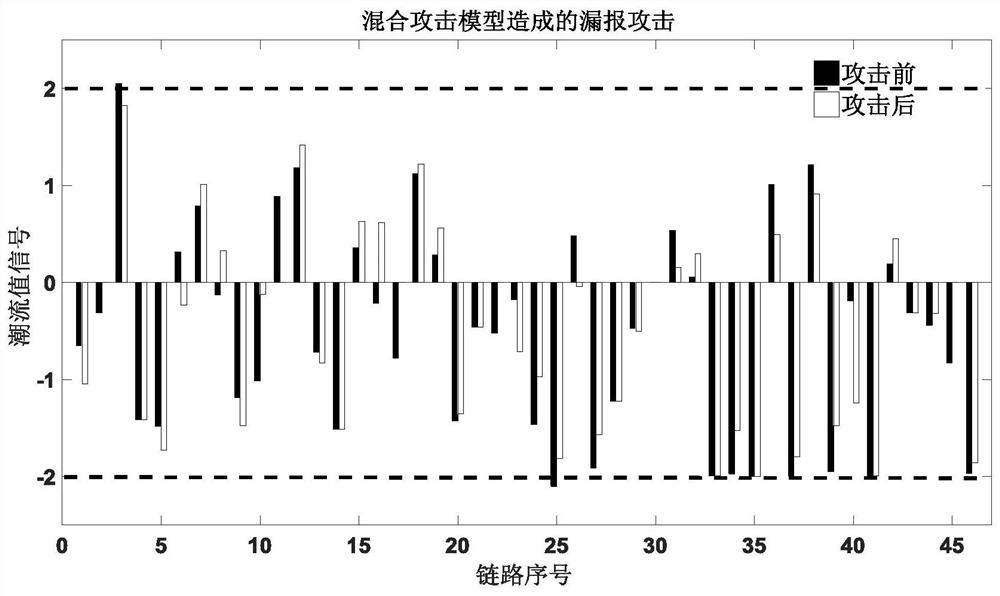
A method for evaluating the stability of power systems against network attacks using a false negative attack model
A power system and network attack technology, applied in the field of power system security research, can solve the problems of lack of network attack models and methods, lack of network attack models and attack methods, data integrity and availability, etc., to improve stability and the effect of robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] The present invention will be further described below with reference to the accompanying drawings and specific implementations.
[0062] The embodiment of the present invention and its implementation process are as follows:
[0063] step 1):
[0064] (1.1) The power system of the embodiment has n substations and m links, the substations are connected through links, and a smart meter is installed on each link to measure the power flow on the link, and the intelligent power of each link is Both the meter and the substation are connected to the server. The server receives the power flow signal from the smart meter and the status signal from the substation. The relationship between the power flow signal and the status signal is established as follows:
[0065] z=Hx+n
[0066] z=(z 1 ,z 2 ,...,z m ) T
[0067] x=(x 1 ,x 2 ,...,x n ) T
[0068] n=(n 1 ,n 2 ,...,n m ) T
[0069] (1.2) Establish the following optimization problem:
[0070]
[0071]
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com