Automated security protection method based on association of camouflage agent and dynamic technology
A security protection and related technology, applied in the direction of electrical components, transmission systems, etc., can solve problems such as false interception, low accuracy, single protection method, etc., and achieve the effect of accurate real-time protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
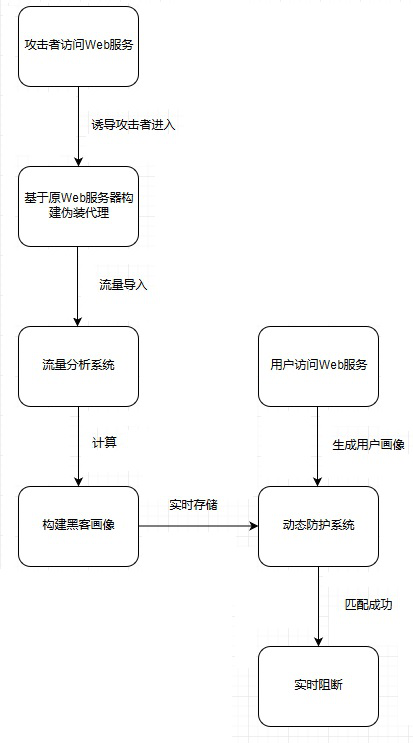
[0024] The core idea of the present invention is to set the following steps:
[0025] (1) Design a disguised agent;
[0026] (2) Design a traffic analysis system, and import the traffic in the disguised proxy into the traffic analysis system;
[0027] (3) According to the fingerprint information obtained by the traffic analysis system, design a "hacker portrait";
[0028] (4) Design a "Dynamic Protection System" and store hacker portraits in the "Dynamic Protection System"; the dynamic protection system is loaded with existing protection strategies, including: dynamic encapsulation, dynamic verification, dynamic confusion, and dynamic tokens, and will (3 ) The hacker portrait generated by ) is added to the dynamic protection system, and quickly spread to all protection nodes, and the programmable countermeasure module is started simultaneously to load the preset scene protection scheme.
[0029] (5) Design a "blocking mode" to block attackers in real time, use the dynamic ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com