Malicious software open set family classification method and device based on adversarial training
A technology of malware and classification methods, applied in computer security devices, computer parts, character and pattern recognition, etc., to achieve high accuracy and stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
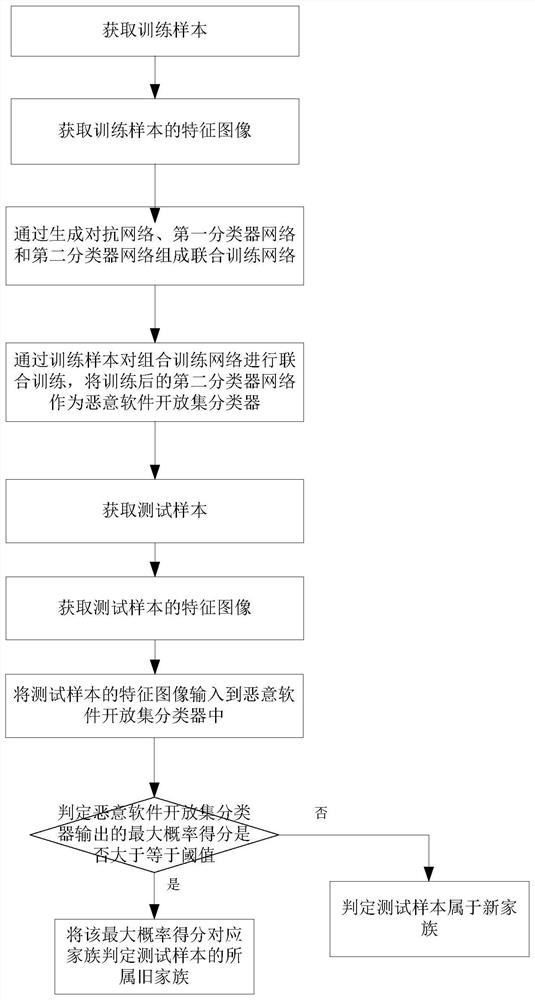
[0061] This embodiment discloses a malware open set family classification method based on adversarial training, by which a malware open set classifier can be trained, and the classifier can perform family classification on malware samples in an open environment, that is, not only Correctly classify the samples belonging to the old family of the training set, and can distinguish the old and new family samples; figure 1 Shown, the step of the inventive method comprises:
[0062] Step S101 , acquiring malware of known old families as training samples. In this embodiment, training samples can be obtained from the Big2015 dataset.
[0063] Step S102, extract the family feature of the training sample, and convert it into a feature image to obtain the feature image of the training sample; in this embodiment, when extracting the family feature for the training sample, use a feature extraction tool to extract the 623-dimensional feature of the sample , and expanded to 1024 bits by co...
Embodiment 2
[0089] This embodiment discloses a malware open set family classification device based on confrontation training, including a first acquisition module, a first feature extraction module, a joint training network construction module, a training module, a second acquisition module, and a second feature extraction module and classification modules, the specific functions of each module are as follows:
[0090] The first obtaining module is used to obtain the malicious software of known old families as a training sample;
[0091] The first feature extraction module is used to extract the family feature of the training sample and convert it into a feature image to obtain the feature image of the training sample;
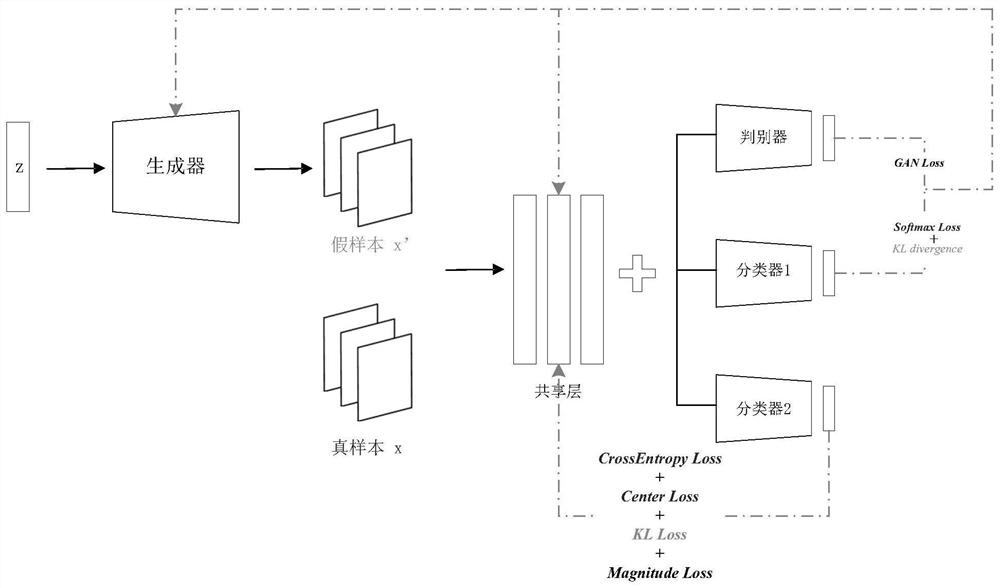
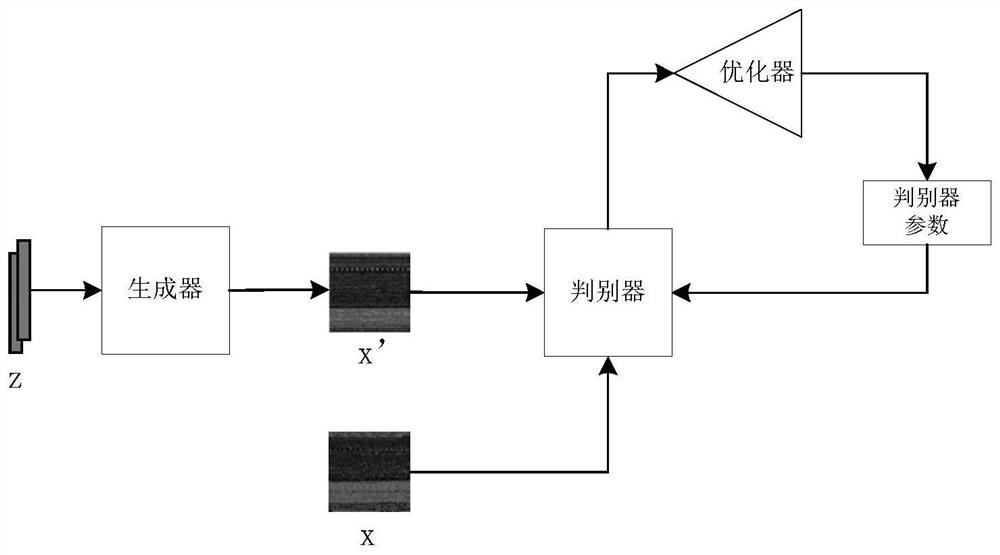
[0092] The joint training network building block is used to form the joint training network by generating the confrontation network, the first classifier network and the second classifier network, wherein the output of the generation confrontation network generator networ...
Embodiment 3
[0100] This embodiment discloses a computing device, which includes a processor and a memory for storing executable programs of the processor. When the processor executes the program stored in the memory, it realizes the malicious software opening for confrontation training described in Embodiment 1. The set family classification method is as follows:
[0101] Obtain malware from known old families as training samples;
[0102] Extract the family feature of the training sample and convert it into a feature image to obtain the feature image of the training sample;
[0103] A joint training network is formed by generating an adversarial network, a first classifier network and a second classifier network, where the outputs of the generator adversarial network generator network are respectively used as the generation adversarial network discriminator network, the first classifier network and the second classifier network input of;
[0104] Jointly training the generation confron...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com