Cluster virtual user system implementation method based on sandbox mechanism
A technology of virtual user and sandbox mechanism, applied in computer security devices, instruments, platform integrity maintenance, etc., can solve problems such as data leakage, damage, system security threats, etc., to meet normal resource access, good closure and isolation, the effect of preventing information overreach
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be further described below in conjunction with drawings and embodiments.
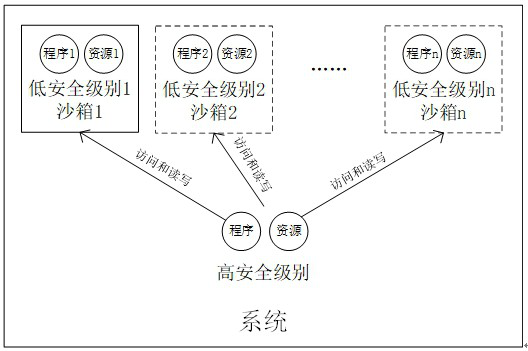
[0019] Such as figure 1 As shown, the system has several switchable modes, such as mode 1, mode 2, ..., mode n, and different modes belong to different security levels. At the same time, the system has two priority levels: high priority and low priority. The high priority permission belongs to the high security level, and the low priority permission belongs to the low security level. Program resources with a high security level of the system can access program resources with a low security level, while program resources with a low security level are enclosed in a sandbox and cannot access external resources.
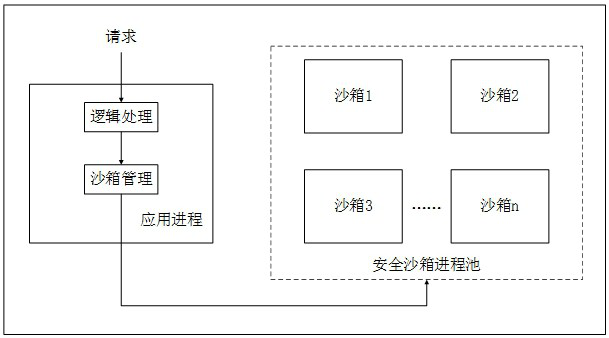
[0020] The system will make a high or low security judgment and judge whether to restart and load. The specific process is: when switching between different security levels, the system needs to be restarted to complete the destruction and establishment of the san...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com