A wireless device authentication method and system thereof
A wireless device and authentication method technology, applied in wireless communication, electrical components, security devices, etc., can solve the problem that the MAC address is vulnerable to tampering, and achieve the effects of reducing the pressure of device authentication, improving security, and increasing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
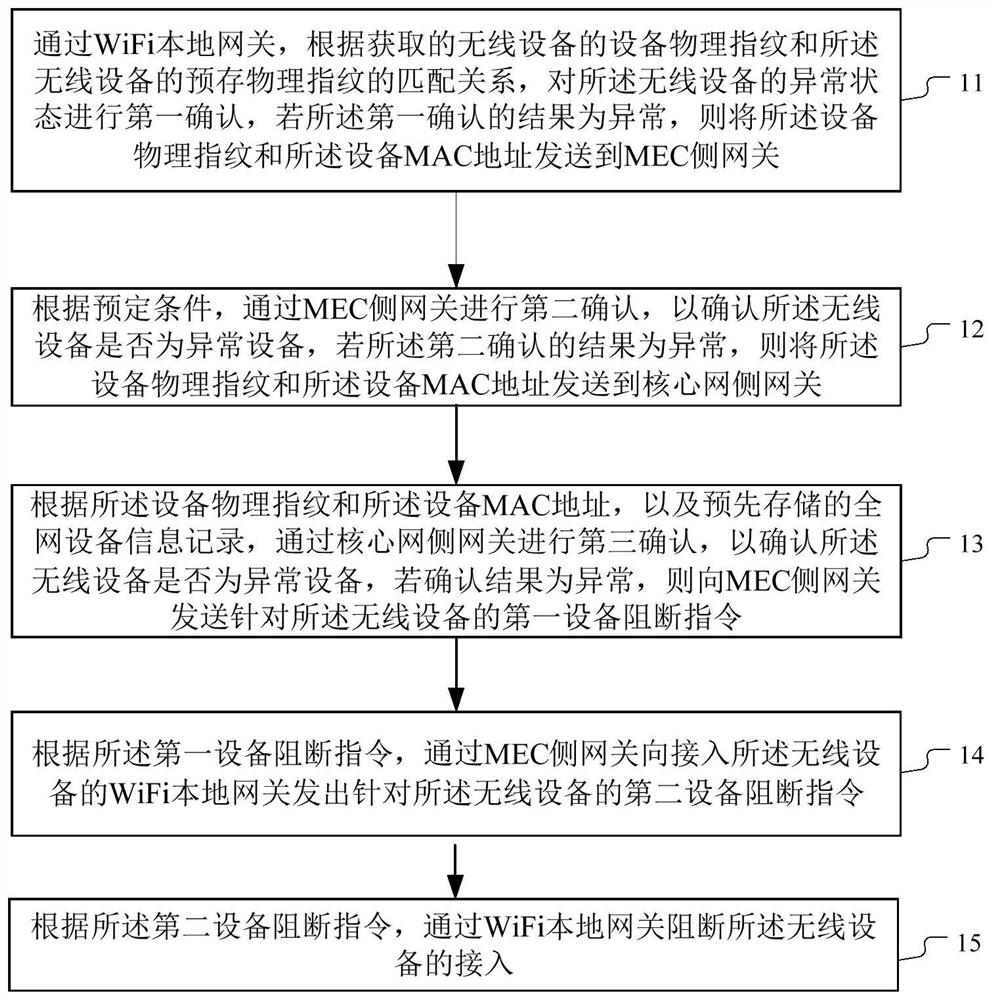
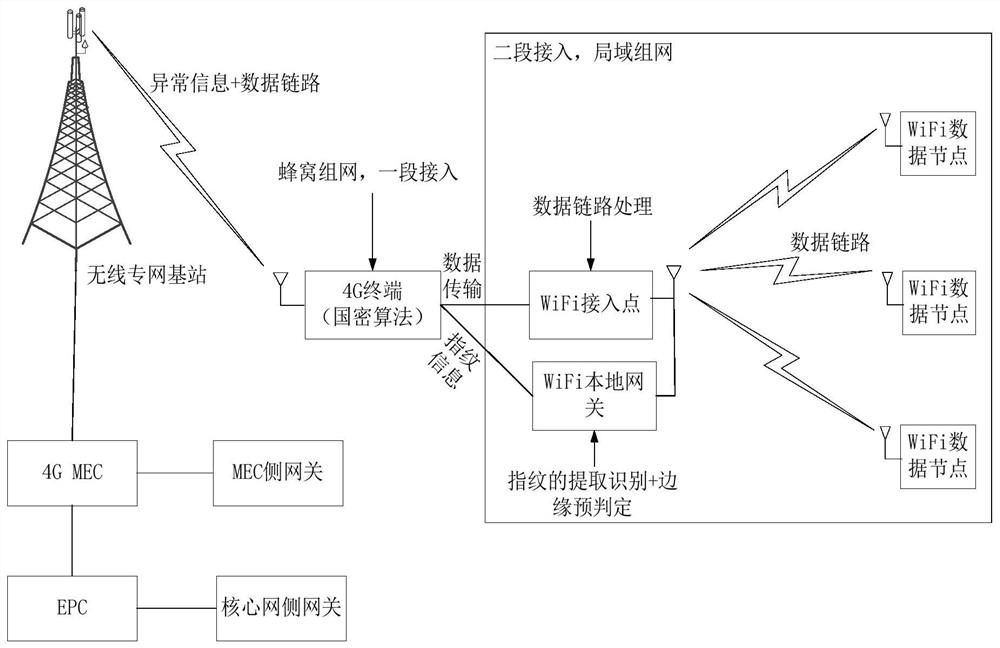
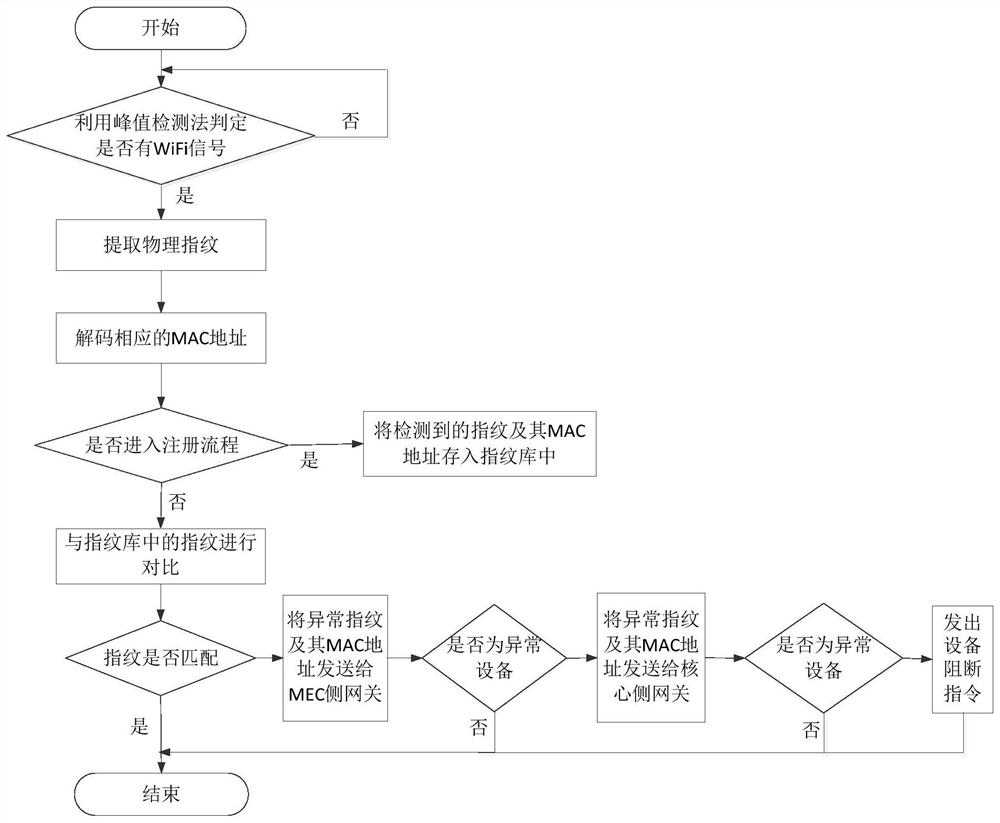
[0056] According to an embodiment, the MEC side gateway performs a second confirmation of whether the device is an abnormal device according to a predetermined condition; if the confirmation result is no abnormality, the device is allowed to access the network. In one example, if a device continuously sends out N abnormal device physical fingerprints within a predetermined time period, the device is confirmed as abnormal device; if more than N abnormal device physical fingerprints do not appear in the predetermined time period If the device is not abnormal, it is determined that the device is not an abnormal device.
[0057] In a specific example, the abnormal information transmitted by the WiFi local gateway can also be stored and comprehensively determined. If a device has more than N abnormal fingerprint samples continuously within a given period of time, the device is considered abnormal. The device then sends the stored abnormal fingerprint samples and their MAC addresses...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com