On-chain digital asset management method and device
A technology of digital assets and management methods, applied in data processing applications, instruments, payment systems, etc., can solve problems such as key loss, digital asset loss, invalidation, etc., to maintain security, ensure security, and save storage and computing. The effect of resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
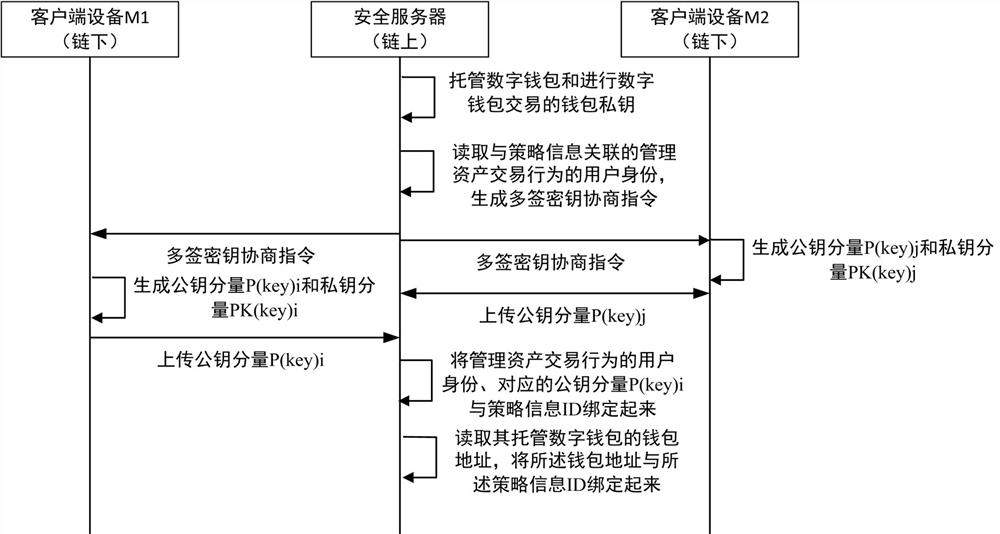
[0036] The present invention proposes an on-chain digital asset management method, which is applied to a digital wallet management system, and the digital wallet management system includes a security server and multiple client devices. Among them, the security server is implemented based on blockchain technology and can host multiple digital wallets. Users under the chain can log in to the security server through the client device to manage their own digital wallets. The communication method between the security server and the client device can be Wired or wireless, the present invention does not limit; for each digital wallet, multiple users can log in to the security server through multiple client devices to jointly participate in the management of the digital wallet.
[0037] Such as figure 1 As shown, a chain digital asset management method proposed by the present invention includes the following steps:
[0038] The security server hosts the user's digital wallet and wall...
Embodiment 2
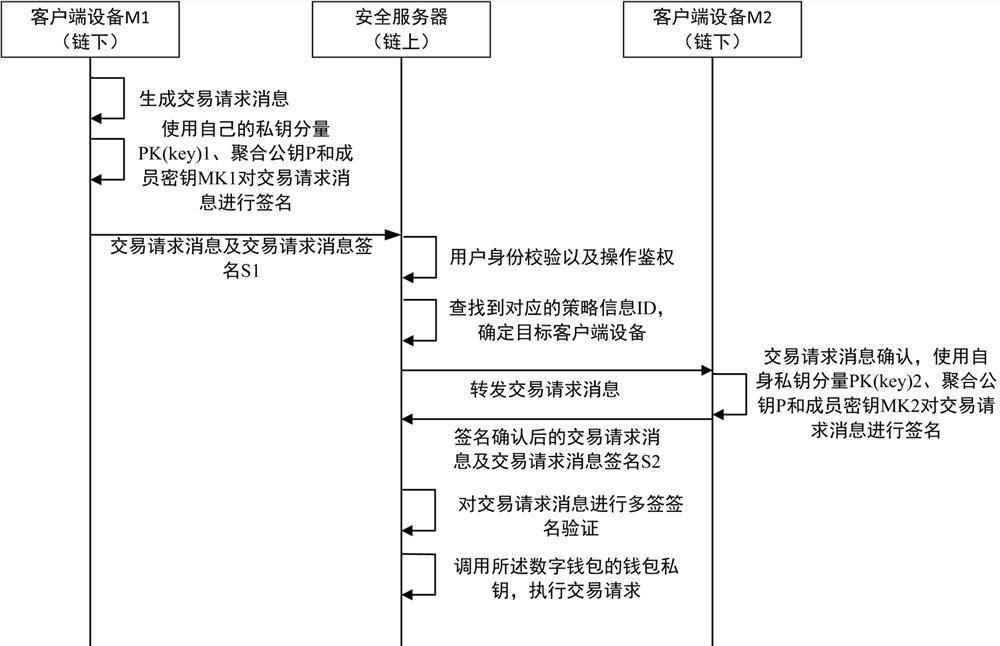
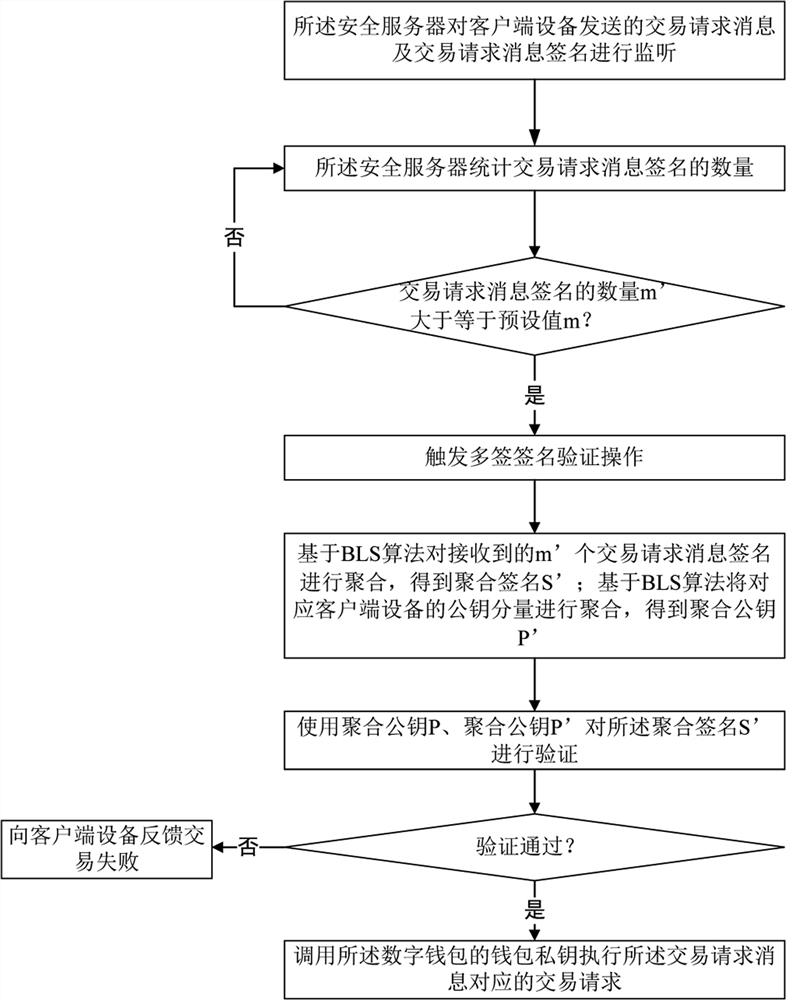
[0071] Such as Figure 4 As shown, the difference between this embodiment and Embodiment 1 is: when the private key component of a certain client device is lost, execute:
[0072] A client device generates a private key loss message, and sends the private key loss message to the security server;
[0073] The security server judges whether the identity of the user who sent the private key loss message has passed the verification and has the second operation authentication; after the corresponding user identity has passed the verification and has the second operation authentication, the security server passes the private key. The signature user identifier i corresponding to the user identity in the key loss message finds the corresponding policy information ID;
[0074] After the security server extracts the identity of the target user who manages the asset transaction behavior through the policy information ID, determines the target client device, and forwards the private key ...
Embodiment 3
[0080] The difference between this embodiment and the above-mentioned embodiments is that when the identity of the user who manages asset transaction behavior changes, execute:
[0081] A client device generates a multi-signature user change message, uses its own private key component PK(key)i, aggregation public key P, and member key MKi to sign the multi-signature user change message, and obtains the multi-signature user change message. message signature, and send the multi-signature user change message and its signature to the security server; wherein, the multi-signature user change message includes a multi-signature user addition message or a multi-signature user deletion message;
[0082] The security server judges whether the identity of the user who sent the multi-signed user change message has passed the verification and has the third operation authentication; after the corresponding user identity has passed the verification and has the third operation authentication, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com