Computer implemented method and system for transferring access to a digital asset
A technology of digital assets and access rights, applied in the field of resource security, can solve problems such as dependence and high complexity of cryptographic primitives, and achieve the effect of enhancing security, improving security and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] System Overview
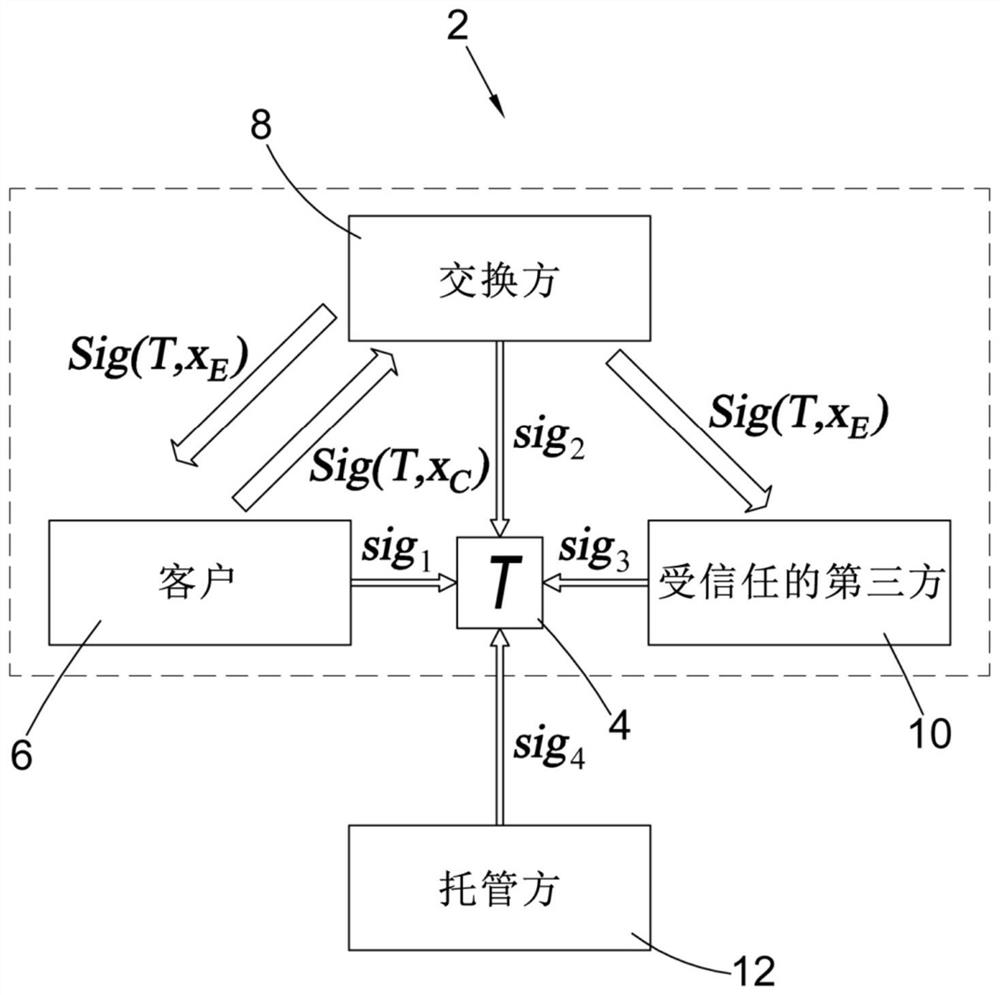
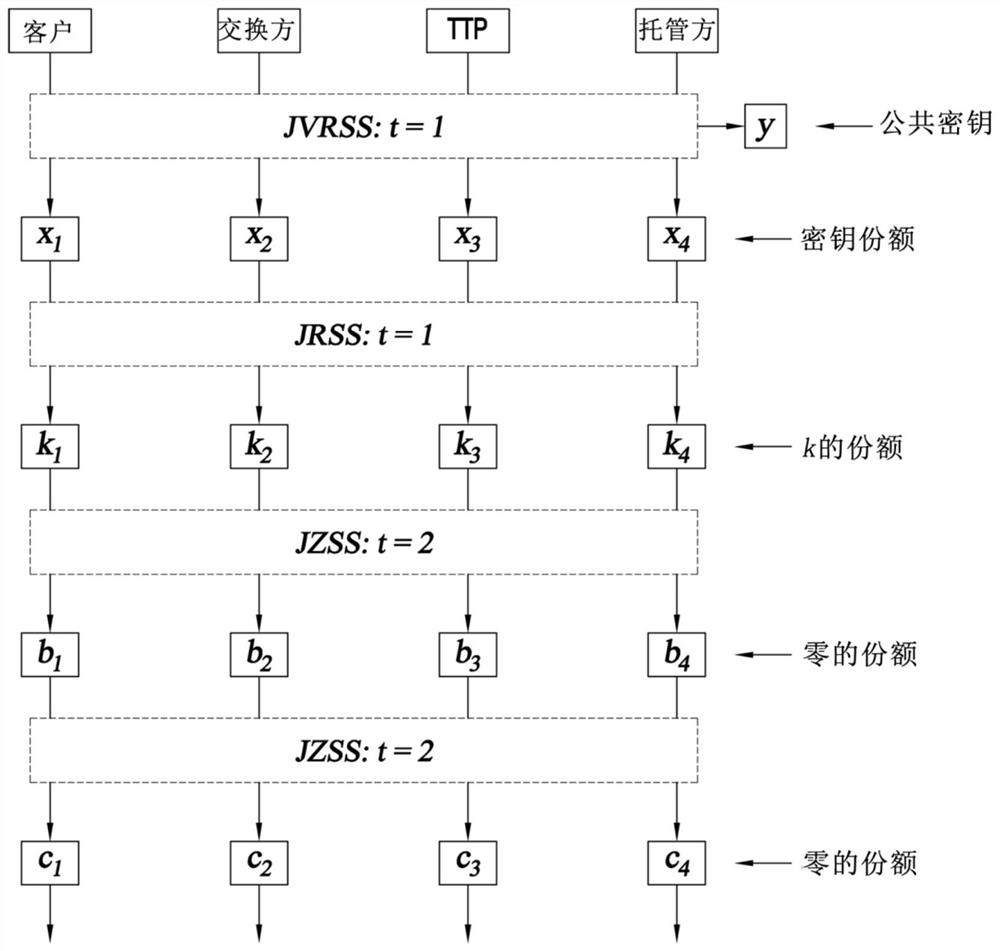
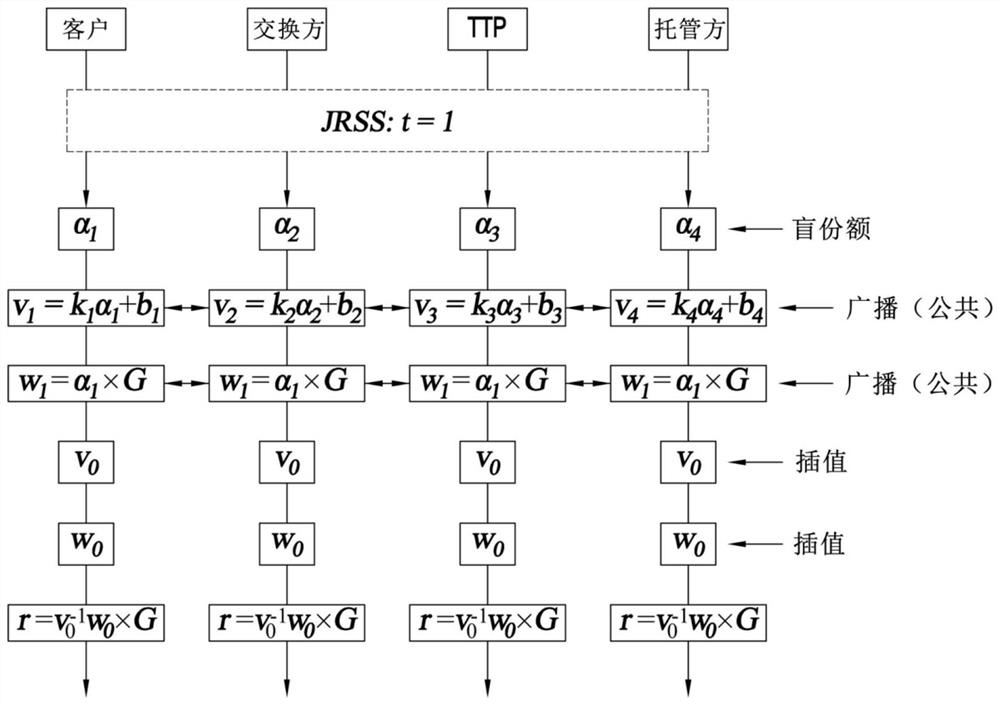
[0061] refer to figure 1 , a system 2 embodying the present invention for performing fast signing of blockchain transactions 4 has four parties in a threshold signature scheme, the four parties being a client 6, an exchange party 8, a trusted third party (TTP) 10, and an escrow Party 12. Each party has a corresponding elliptic curve public / private key pair (y C , x c ), (y Ex, x Ex ), (y T , x T ), (y Es, x Es ). The present invention features an additional party, the TTP 10, compared to the typical "2 of 3" hosting configuration of the prior art. As explained in more detail below, the generation of every signature that requires the TTP 10 to participate does not involve the escrow party 12 (in the case of troubleshooting).
[0062] The TTP 10 is required to have a fast (low latency) and reliable connection to the exchange party 8, and the TTP 10 should be separate from all other party entities.
[0063] Then, a secure communication channel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com