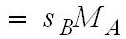Method, system and device for information encryption matching, processor and storage medium
An information encryption and processor technology, applied in the computer field, can solve problems such as unsatisfactory message encryption and matching requirements of partners, satisfactory performance, hash information collision, etc., and achieve fast processing speed, randomness, and high encryption strength Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] Before describing the embodiments according to the present invention in detail, it should be noted that in the following, relative terms such as first and second are only used to distinguish one entity or action from another entity or action, and do not necessarily require or Any actual such relationship or order between such entities or actions is implied. The terms "comprising", "comprising" or any other variant are intended to cover a non-exclusive inclusion whereby a process, method, article or apparatus comprising a set of elements includes not only those elements but also other elements not expressly listed elements, or elements inherent in such a process, method, article, or apparatus.
[0046] In order to describe the technical content of the present invention more clearly, further description will be given below in conjunction with specific embodiments.
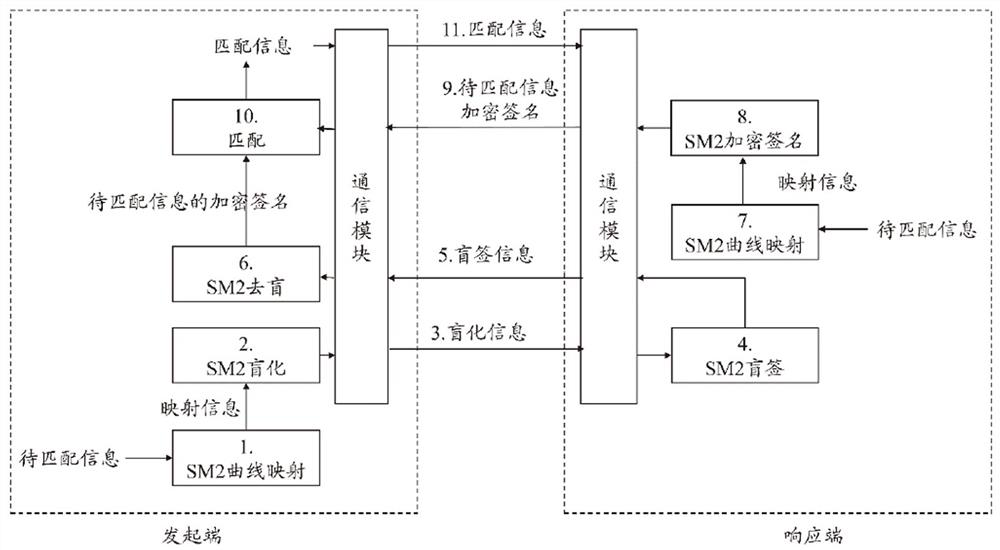
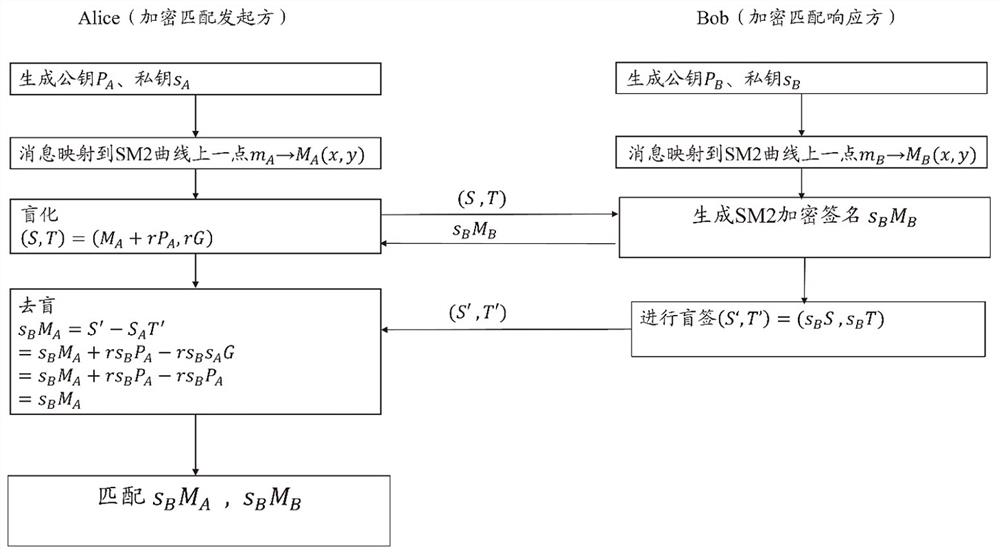
[0047] see figure 1 and figure 2 As shown, in the specific embodiment of the present invention, a messa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com