A blockchain-based online process evidence collection and evidence storage method
A blockchain and block technology, applied in the direction of program/content distribution protection, user identity/authority verification, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
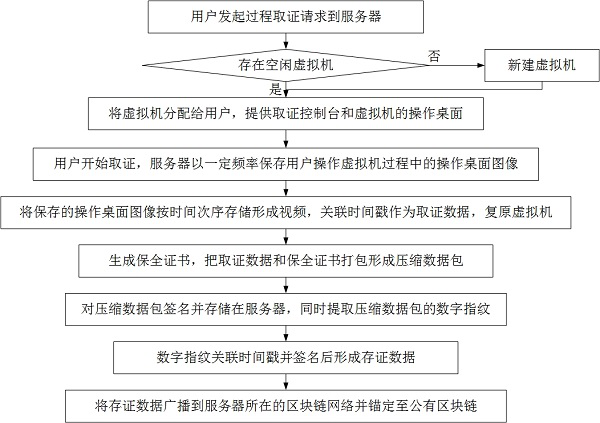
[0020] A blockchain-based online process forensics and evidence storage method, such as figure 1 shown, including:
[0021] Forensics:
[0022] The user initiates a process forensics request to the server; the server queries whether there is an idle virtual machine currently, if there is an idle virtual machine, the idle virtual machine is allocated to the user, and if there is no idle virtual machine, a new virtual machine is allocated to the user. The virtual machine is networked and able to install application software.
[0023] Provide users with the forensic console and the operation desktop of the virtual machine, and assign the forensic number. The forensic console is used to start / end forensics, and users can connect and operate the virtual machine remotely. The name of the running process of the virtual machine is displayed in the semi-transparent suspension of the operation desktop, and the area where the process name is displayed can be changed by dragging with th...
Embodiment 2
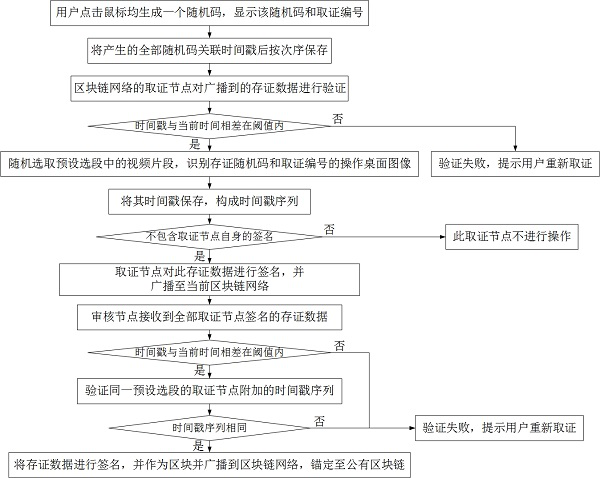
[0032] A blockchain-based online process forensics and evidence storage method, this embodiment is further improved on the basis of Embodiment 1, such as figure 2 As shown in the figure, during the user's forensics process, each time the user clicks the mouse, the server generates a random code, and the random code, the forensics number and the preset standard solid-color icon for quick identification are displayed under the mouse pointer. duration. When saving the operating desktop image of the virtual machine with the server, it is saved to the picture, and the server associates all the generated random codes with time stamps and saves them in order to form a random code array. The random code array is signed and encrypted and included in the forensic data. Random clicks of the mouse will cause the unique forensic number and random code to be displayed, that is, a watermark that is randomly mixed in the forensic screen is actually formed.
[0033] The forensic node of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com