Hardware Trojan horse detection method based on deep learning
A technology of hardware Trojan detection and deep learning, which is applied in the field of image processing, can solve problems such as ineffective classification, difficult detection, and chip identification, and achieve the effects of reducing the missed detection rate of hardware Trojans, saving manpower and material resources, and improving resolution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
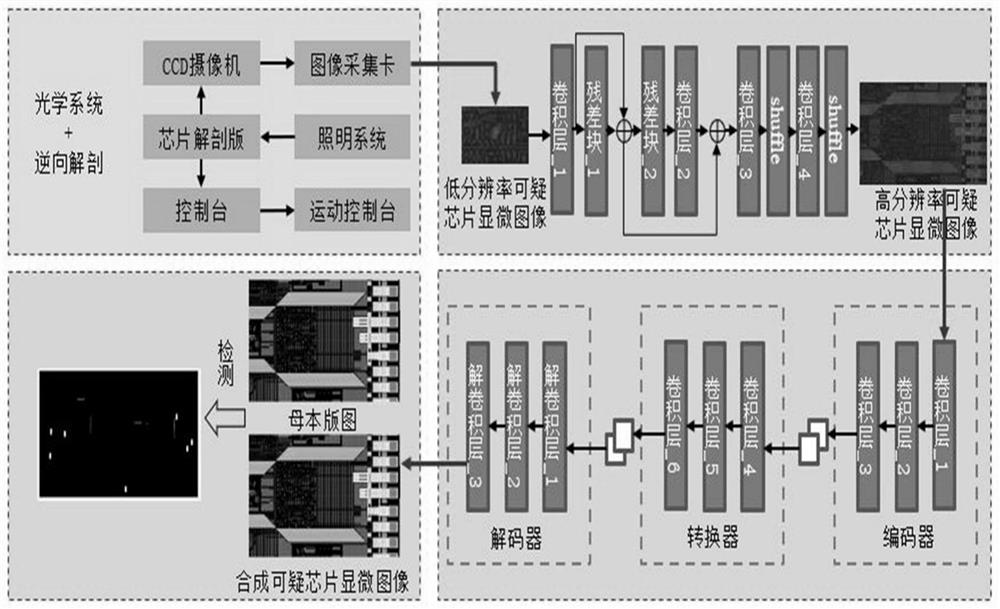
[0025] refer to figure 1 , the specific implementation steps of the present invention are as follows:
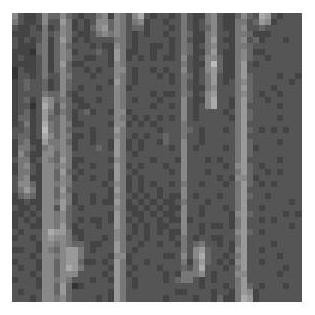
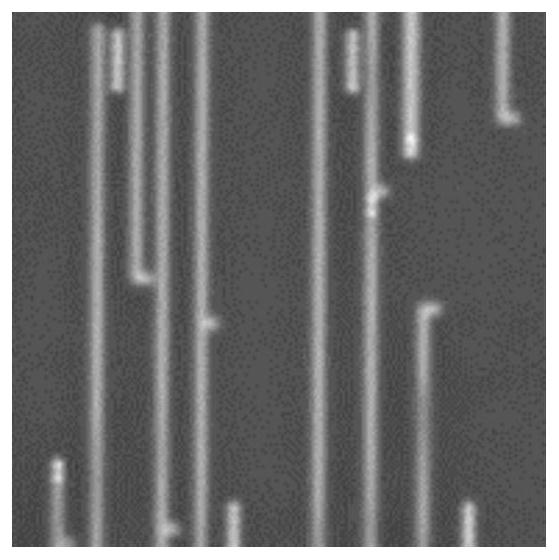
[0026] Step 1: collect the low-resolution chip microscopic image set W, the high-resolution chip microscopic image set X and the corresponding master microscopic image set Y to construct a training set.
[0027] 1.1) The bare chip is extracted from the chip, and chemically treated to peel off each layer of the bare chip, and then each layer of the bare chip is polished to smoothness, and the 800 times lens and the 1600 times lens of the scanning electron microscope are respectively Take a complete low-resolution chip microscopic image and a complete high-resolution chip microscopic image;
[0028] 1.2) Analyze the IP core of the mother chip corresponding to the chip in 1.1), and obtain a complete master microscopic image;
[0029] 1.3) Capture the complete low-resolution chip microscopic image, the complete high-resolution chip microscopic image and the complete master mic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com