Function hijacking method and device, medium and electronic equipment
A function and function library technology, applied in the computer field, can solve problems such as destroying the environment, reducing the running speed of the program, and failing to meet the debugging requirements.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0036] The first embodiment provided by the present disclosure is an embodiment of a function hijacking method.
[0037] Combine below Figure 1 to Figure 5 Embodiments of the present disclosure will be described in detail.
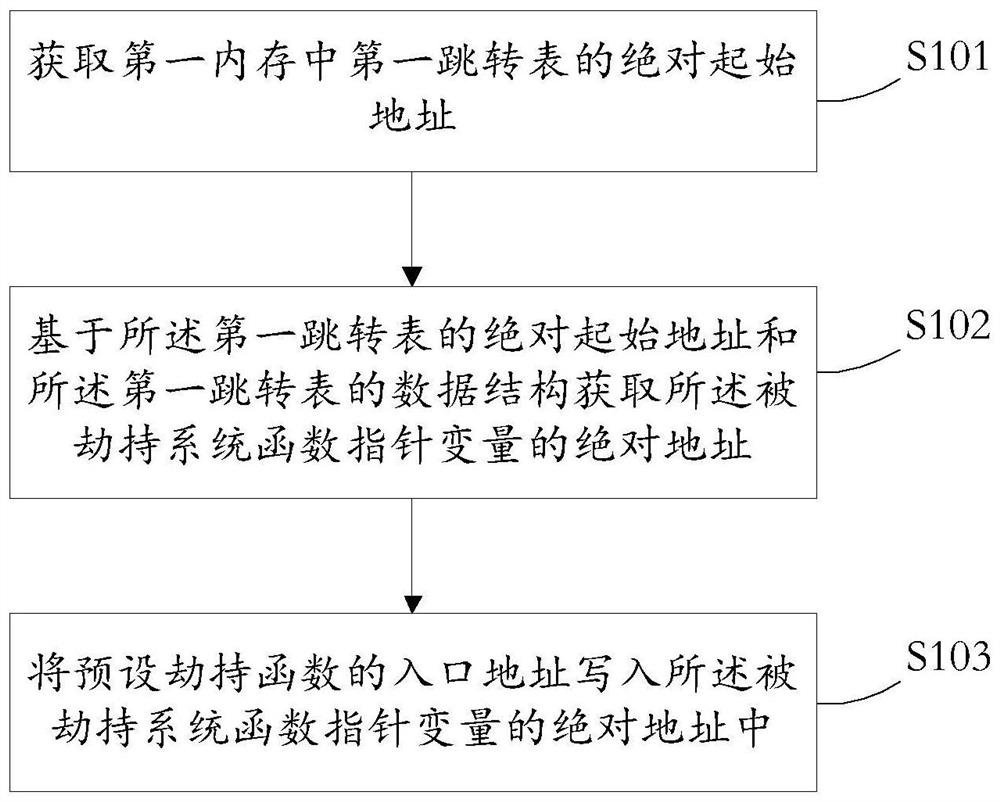
[0038] Such as figure 1 As shown, in step S101, the absolute starting address of the first jump table in the first memory is obtained.
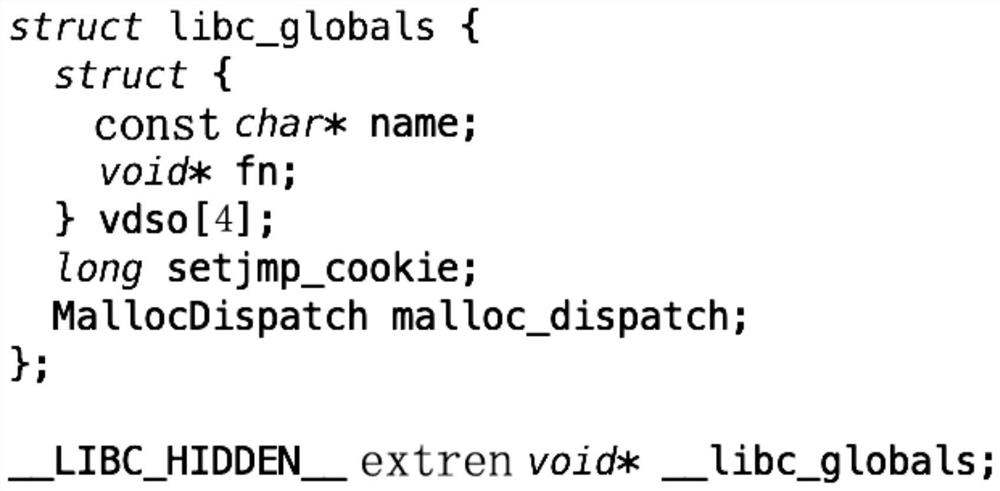
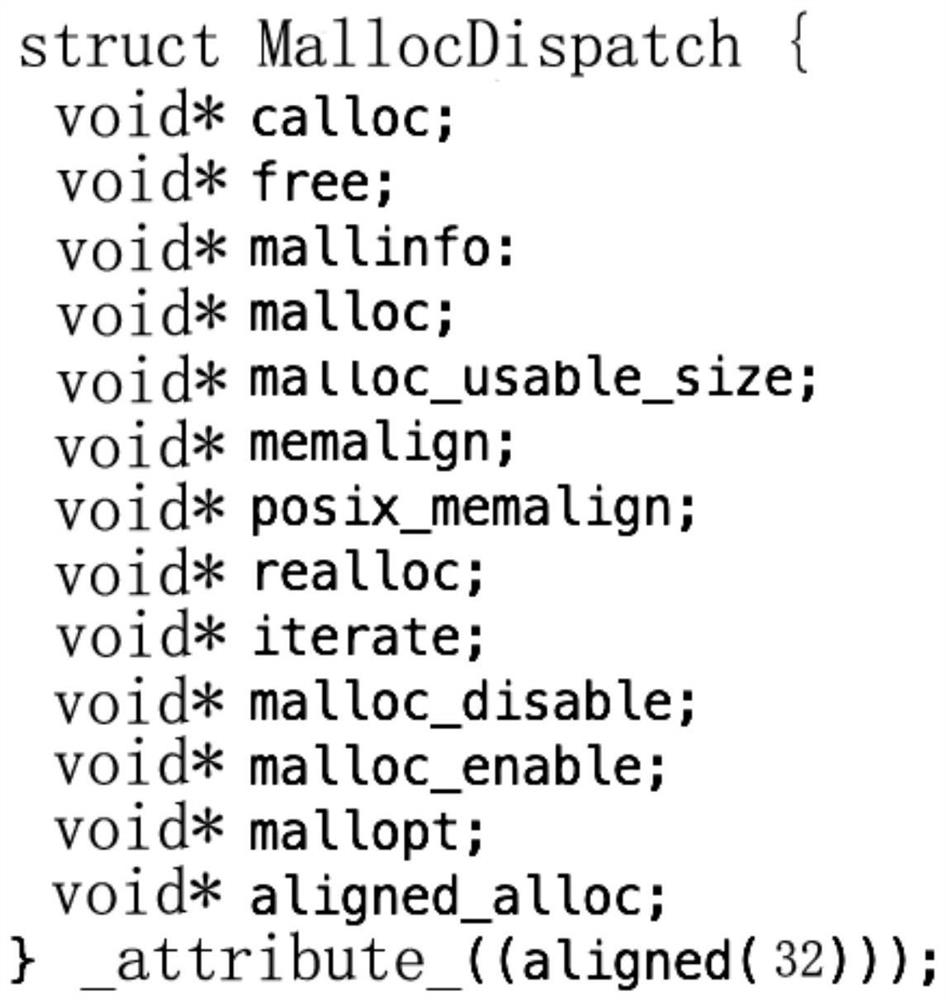
[0039] The first memory includes memory occupied by the first function library symbol table after the function library symbol table file is loaded.
[0040] The function library symbol table file is a kind of library file, which provides information about the hijacked system functions, so that developers can perform some operations related to the system through the hijacked system functions. Before the program calls the hijacked system function, the function library symbol table file defining the hijacked system function needs to be loaded into the memory. For example, in the Android system, the function library symb...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com