Trusted data authorization method, certificate authorization method and service access method
A data authorization and trusted technology, applied in the field of data security interaction, can solve problems such as data sharing difficulties, irregular use of user data, and difficulties in business data collaboration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048]In order to facilitate the understanding of those skilled in the art, the present invention will be further described below in conjunction with the embodiments and accompanying drawings.
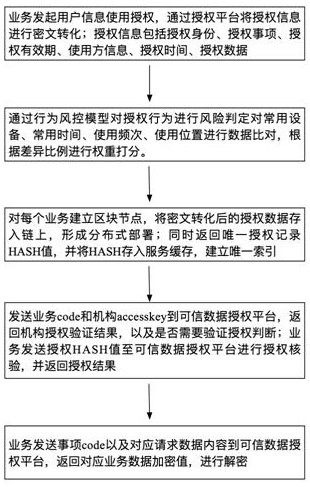
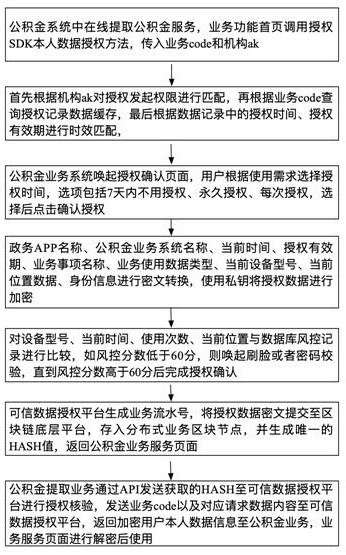
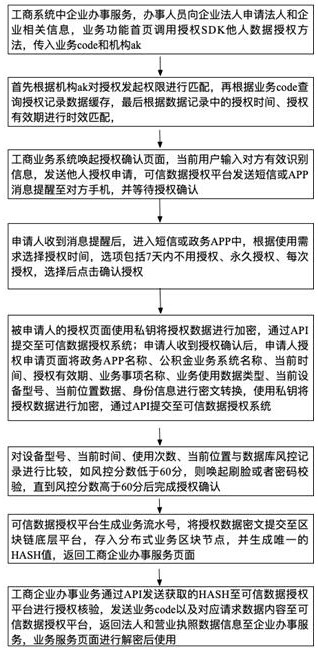
[0049] The trusted data authorization method based on blockchain in this embodiment utilizes the technical characteristics of blockchain such as non-tamperable, traceable, privacy protection, and distributed fault tolerance, and builds a trusted data authorization platform around the technical concept of overall planning, openness, and control. , Establish a standard on-chain process to realize perceivable authorization behaviors, identifiable authorization risks, and traceable authorization records.
[0050] Such as figure 1 As shown, a trusted data authorization method includes the following steps: when the business initiates user information authorization, the authorization information is transformed into ciphertext through the trusted data authorization platform; If the risk is ju...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com