High-security storage access method and device based on user iris recognition
A technology for iris recognition and safe storage, which is applied in the fields of instruments, digital data authentication, and electronic digital data processing, etc. It can solve problems such as weak security and poor user experience, and achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] In order to explain in detail the technical content, structural features, achieved goals and effects of the technical solution, the following will be described in detail in conjunction with specific embodiments and accompanying drawings.
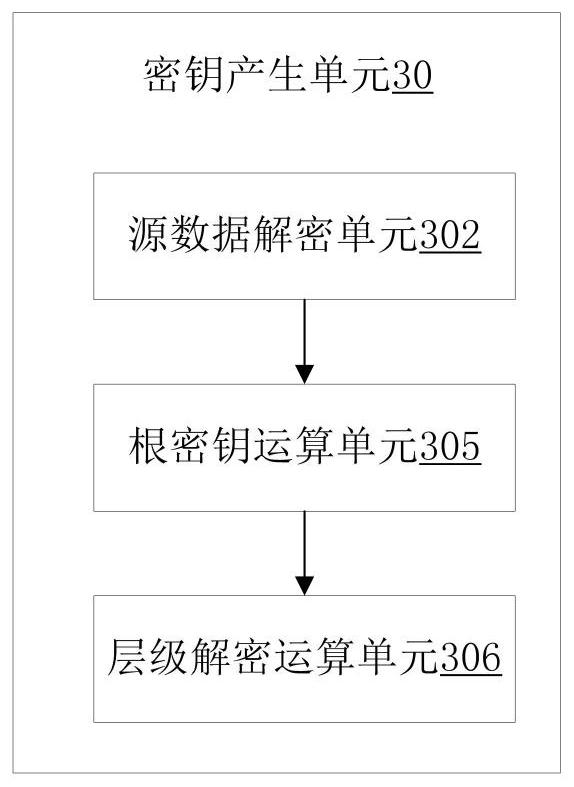
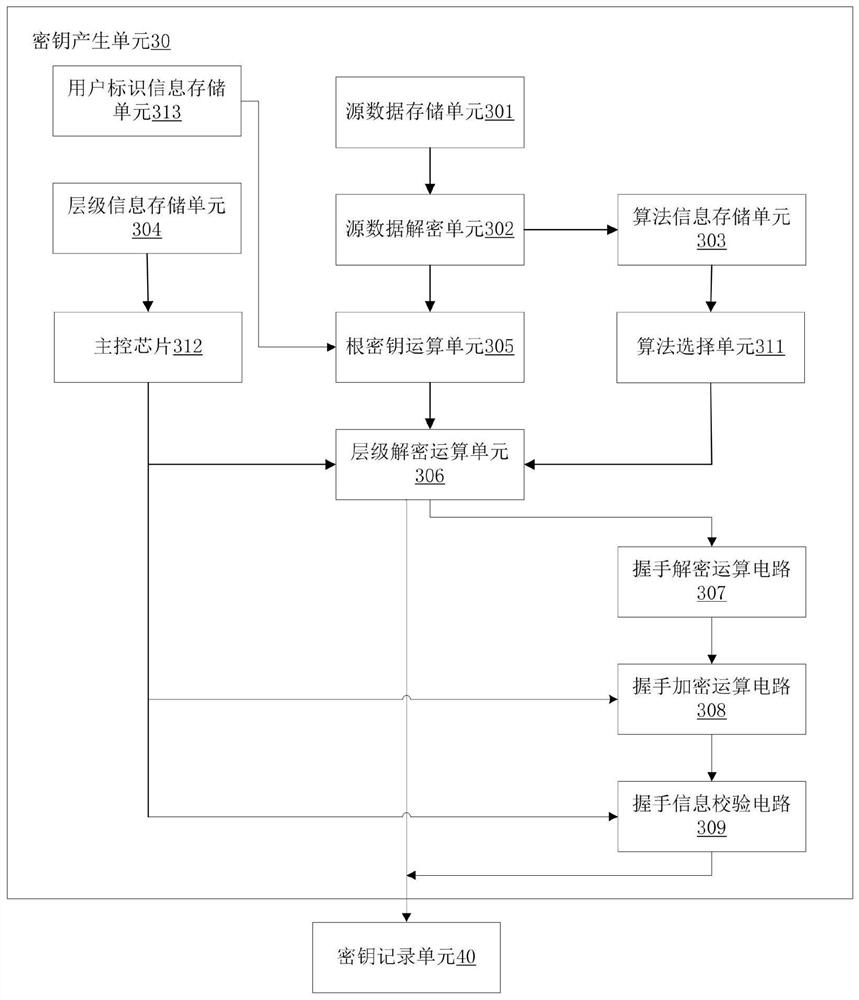
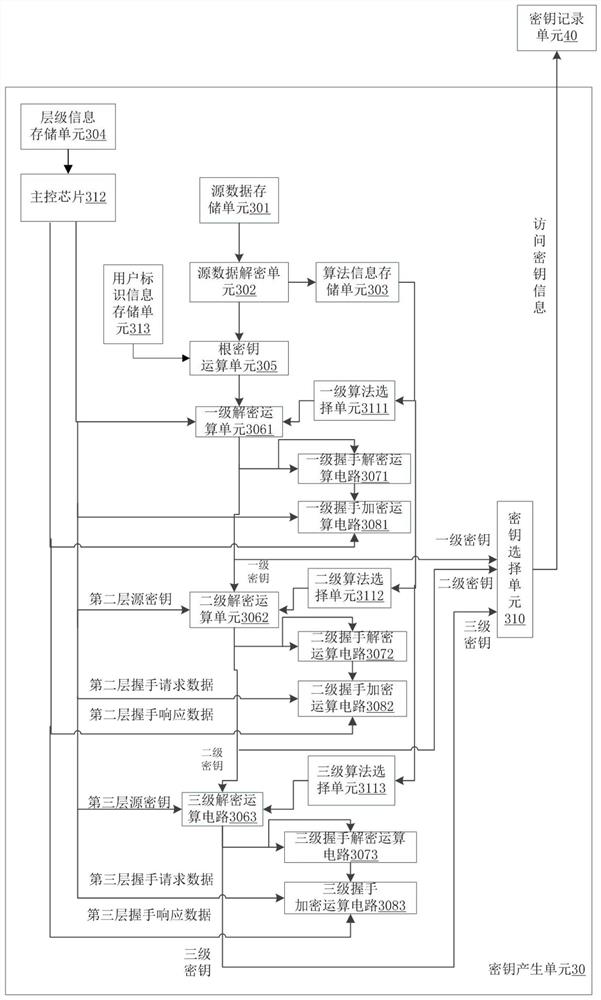
[0075] Such as Figure 9 As shown, the first aspect of the present invention provides a high-security storage access method based on user iris recognition, and the method is applied to a high-security storage access device based on user iris recognition, and the device includes: an iris recognition unit, a legal iris Information storage unit, user level storage unit, key generation unit, second encryption and decryption circuit, read and write control circuit, data storage unit;
[0076] The method comprises the steps of:
[0077] First enter step S901 iris identification unit receives the iris information of the current user collected by the iris collection unit, compares the iris information of the current user collected with the l...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap