Honeypot system attack playback method and device, storage medium and equipment
A playback device and honeypot technology, applied in the transmission system, electrical components, etc., can solve the problem that the recording method is easy to be exposed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
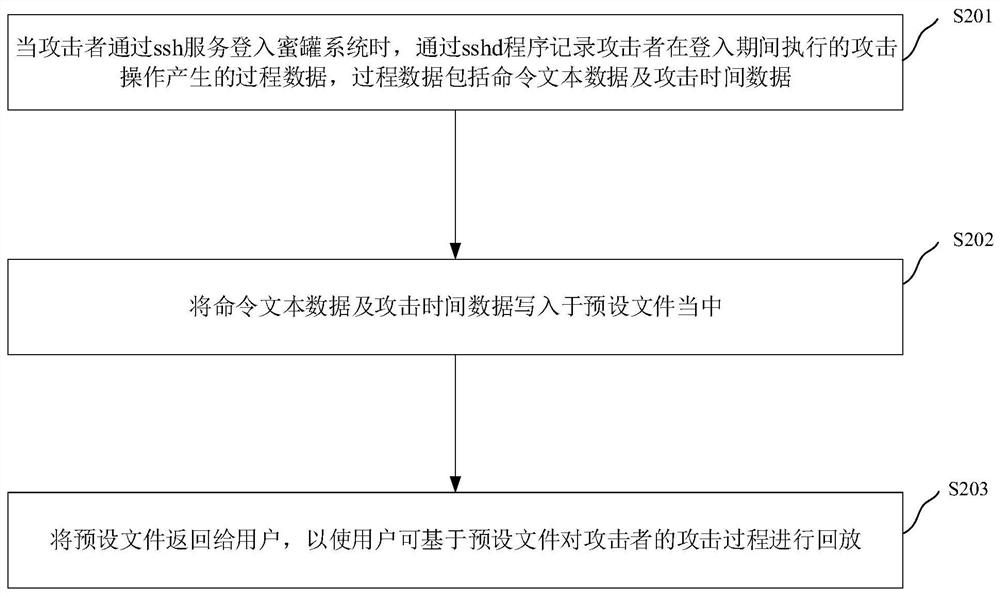
[0045] Example 1: Please refer to figure 2 , which shows the honeypot system attack playback method in the first embodiment of the present invention, which can be applied to the honeypot system attack playback device. The honeypot system attack playback method can be implemented by software and / or hardware. The method specifically includes steps S201 to step S203.
[0046] Step S201, when the attacker logs into the honeypot system through the ssh service, the process data generated by the attack operation performed by the attacker during the login period is recorded through the sshd program, and the process data includes command text data and attack time data.
[0047] During specific implementation, the process data generated by the attack operations performed by the attacker during login can be recorded through the echo record subroutine. Among them, the process data is the echo content returned by the bash module to the attacker, including command text data and attack tim...
Embodiment 2
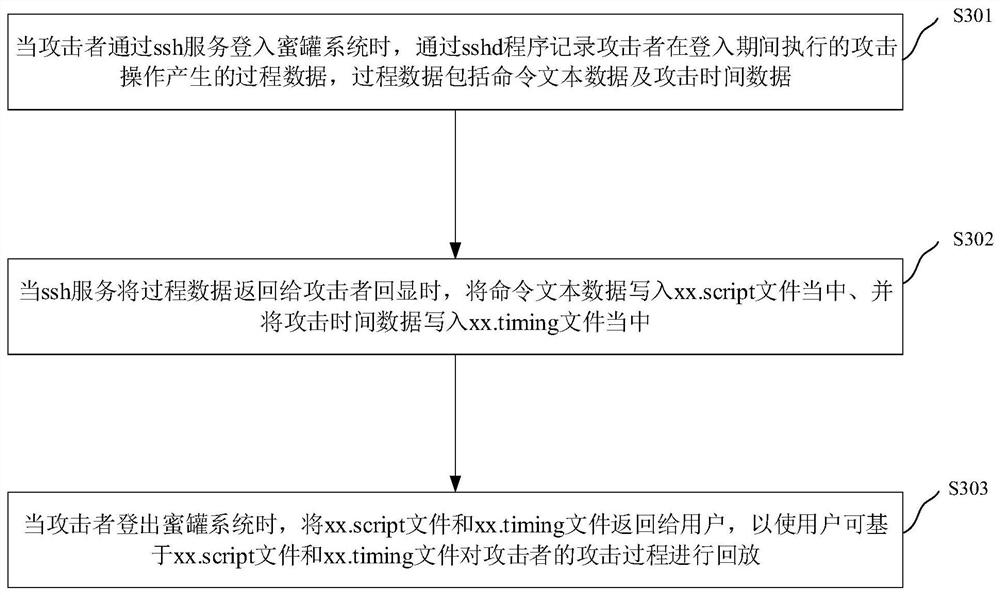
[0055] Example 2: Please refer to image 3 , which shows the honeypot system attack playback method in the second embodiment of the present invention, which can be applied to the honeypot system attack playback device. The honeypot system attack playback method can be implemented by software and / or hardware. The method specifically includes steps S301 to step S303.
[0056] Step S301, when the attacker logs into the honeypot system through the ssh service, the process data generated by the attack operation performed by the attacker during the login period is recorded through the sshd program, and the process data includes command text data and attack time data.
[0057] Step S302, when the ssh service returns the process data to the attacker for echo, write the command text data into the xx.script file, and write the attack time data into the xx.timing file.
[0058] Wherein, the xx.script file and the xx.timing file are pre-files with fixed formats. That is to say, in this ...
Embodiment 3
[0080] Embodiment 3: Another aspect of the present invention also provides a honeypot system attack playback device, please refer to Figure 4 , shows the honeypot system attack playback device in the third embodiment of the present invention, which can be applied to the honeypot system attack playback device, specifically, it can be the processor of the honeypot system attack playback device, and the honeypot system attack playback device includes :
[0081] The data recording module 41 is used for when the assailant logs in the honeypot system by the ssh service, records the process data generated by the attack operation performed by the assailant during the login period through the sshd program, and the process data includes command text data and attack time data;
[0082] Data writing module 42, for writing command text data and attack time data in the middle of the default file;
[0083] The file return module 43 is configured to return the preset file to the user, so th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com