Management method of edge equipment and related device
An edge device and management method technology, applied in the computer field, can solve the problems of cumbersome deployment process, affecting the expansion efficiency of edge devices, and high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
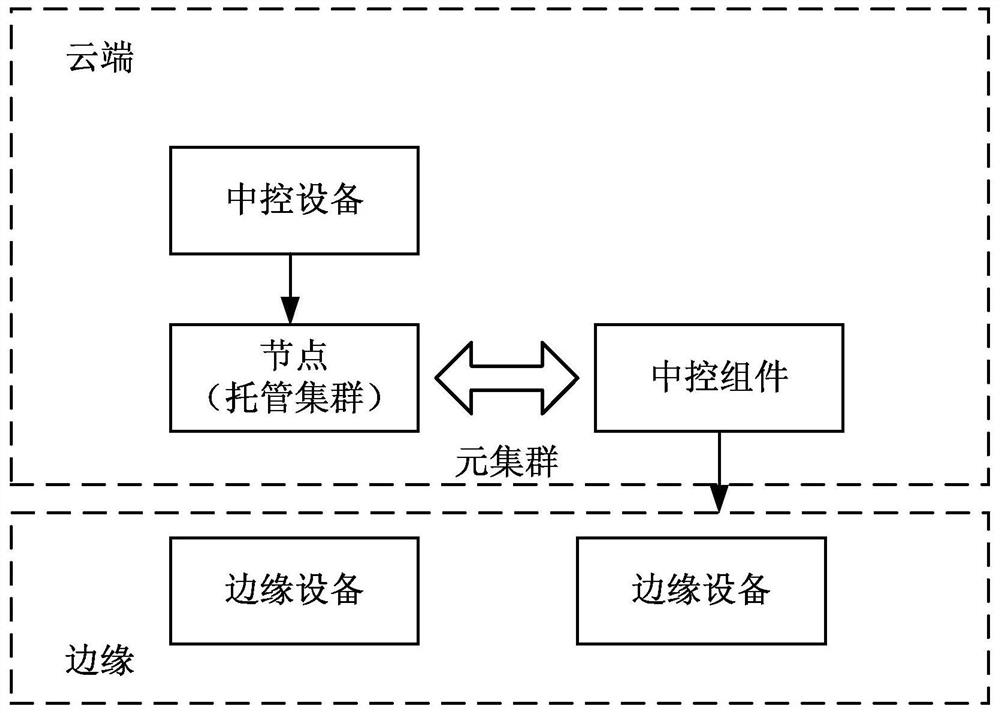
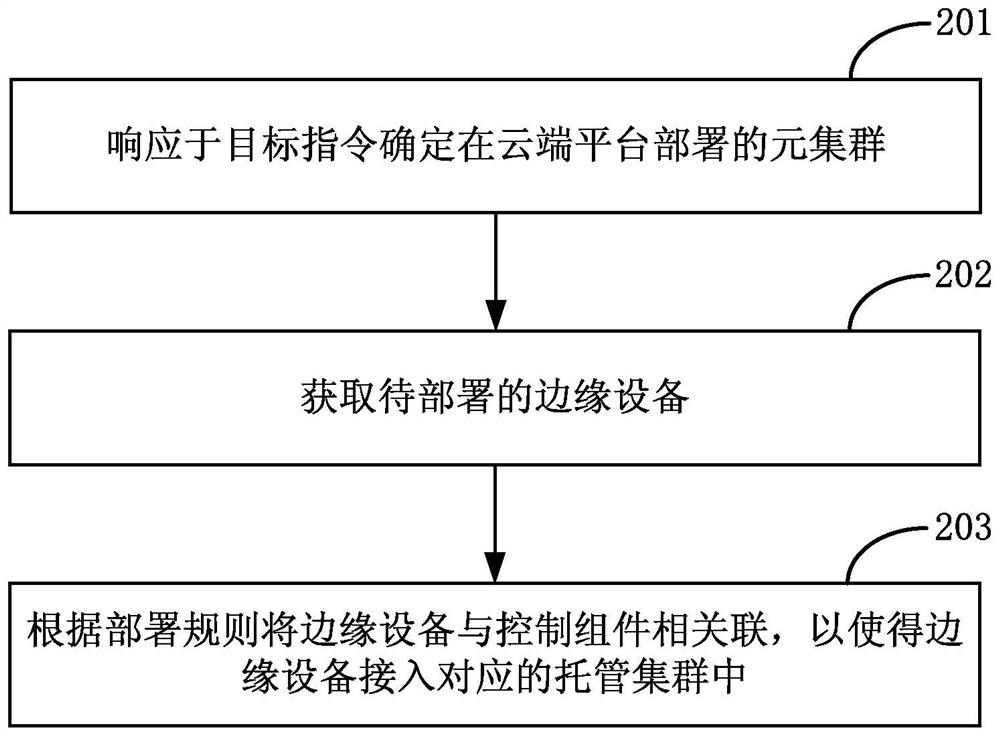
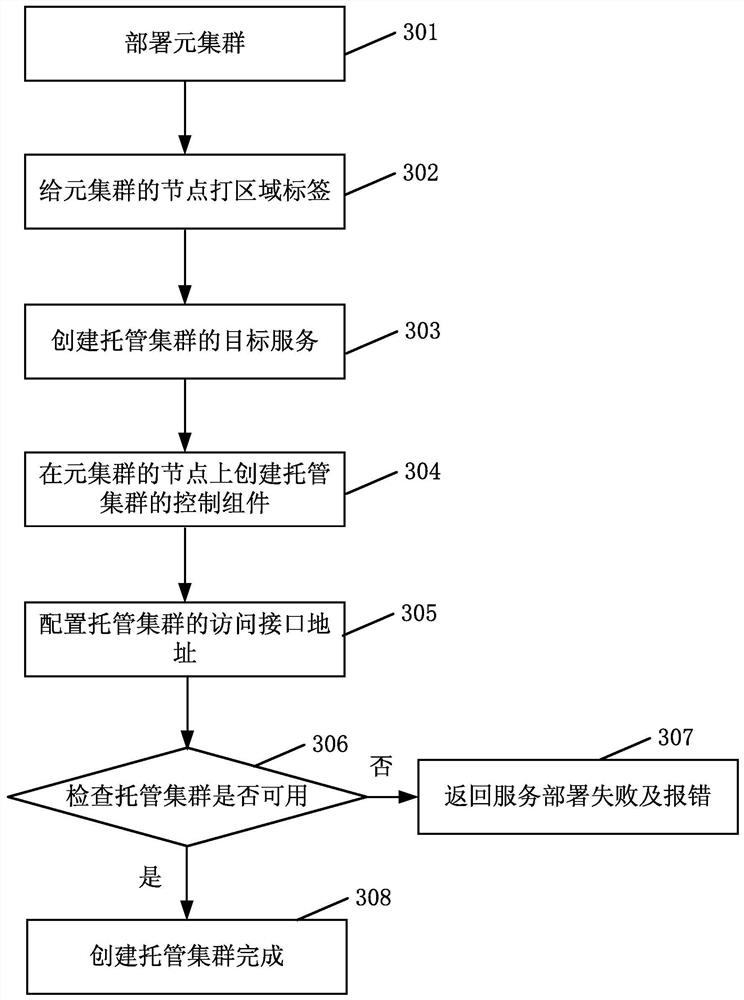
[0089] The embodiment of the present application provides a method for managing edge devices and related devices, which can be applied to systems or programs that include management functions of edge devices in terminal devices. The cluster includes a central control device and at least one associated hosting cluster, the central control device is used to issue target instructions to the hosting cluster, and at least one control component is configured in the hosting cluster; then obtain the edge device to be deployed; then the edge device It is associated with the control component to deploy the edge service corresponding to the target command on the edge device. In this way, the process of rapidly expanding and managing edge devices is realized. Since edge devices are managed through the control components in the hosting cluster, there is no need to redeploy the upper-layer meta-cluster framework during the cluster expansion process, which improves the expansion efficiency of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com