Log analysis-based vulnerability scanning method, apparatus and device, and storage medium
A vulnerability scanning and vulnerability technology, applied in the field of computer networks, can solve the problem that the attack behavior is not timely and accurate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
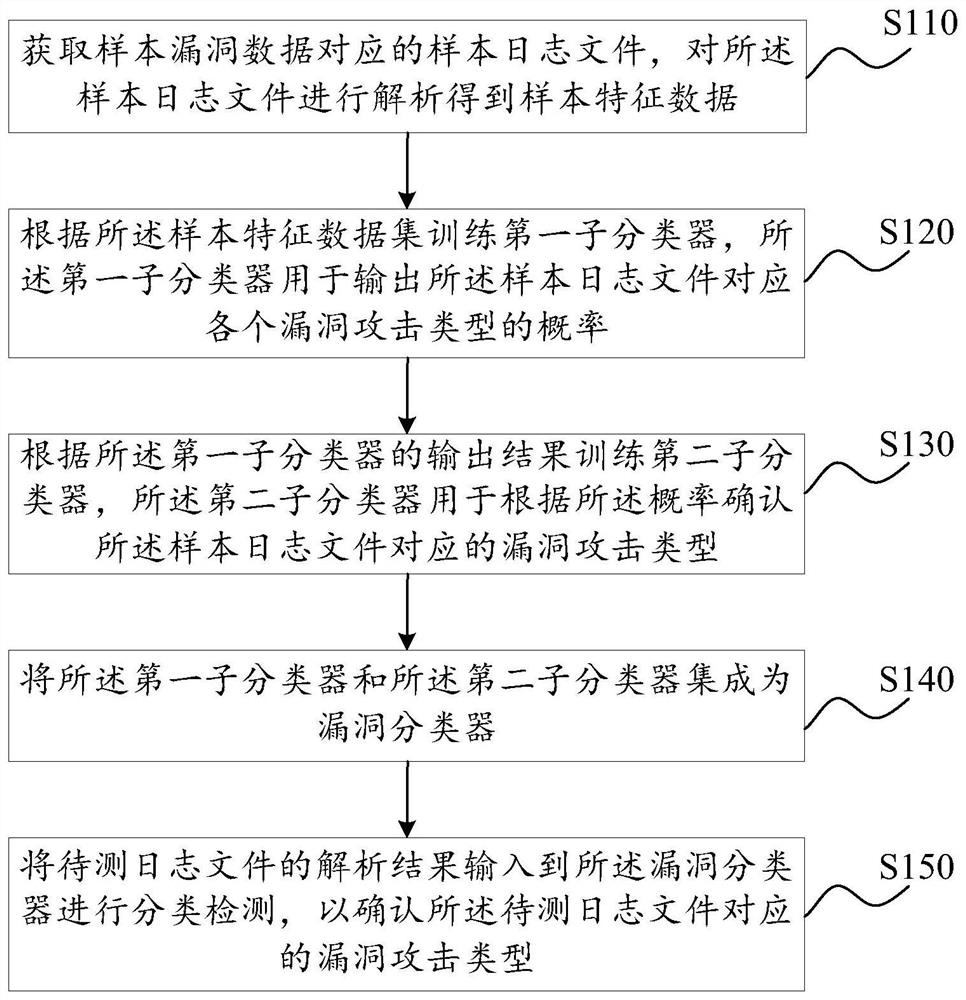
[0047] figure 1 It is a flowchart of a vulnerability scanning method based on log analysis provided by Embodiment 1 of the present invention. The vulnerability scanning method based on log analysis provided in the embodiment can be executed by an operating device corresponding to the vulnerability scanning method based on log analysis. The operating device can be implemented by software and / or hardware. The operating device can be two or more It can be composed of a physical entity, or it can be composed of a physical entity.
[0048] Specifically, refer to figure 1 , the vulnerability scanning method based on log analysis, specifically includes:
[0049] Step S110: Obtain a sample log file corresponding to the sample vulnerability data, and analyze the sample log file to obtain sample feature data.
[0050] In this solution, the sample vulnerability data used for training can be log files accumulated in daily discovery and response to vulnerability attacks, or log files fr...
Embodiment 2
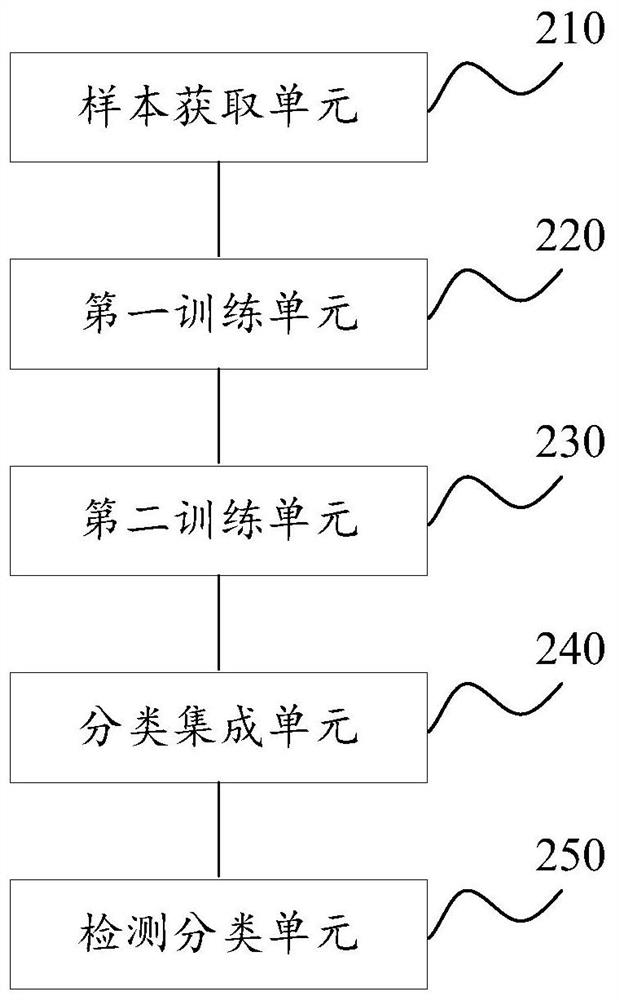
[0076] figure 2 A schematic structural diagram of a log analysis-based vulnerability scanning device provided in Embodiment 2 of the present application is given, refer to figure 2 , the vulnerability scanning device based on log analysis includes a sample acquisition unit 210 , a first training unit 220 , a second training unit 230 , a classification integration unit 240 and a detection classification unit 250 .
[0077] Among them, the sample acquisition unit 210 is used to obtain the sample log file corresponding to the sample vulnerability data, and analyze the sample log file to obtain the sample feature data; the first training unit 220 is used to train the first sample log file according to the sample feature data set. A sub-classifier, the first sub-classifier is used to output the probability of each vulnerability attack type corresponding to the sample log file; the second training unit 230 is used to train the second sub-classification according to the output resu...
Embodiment 3
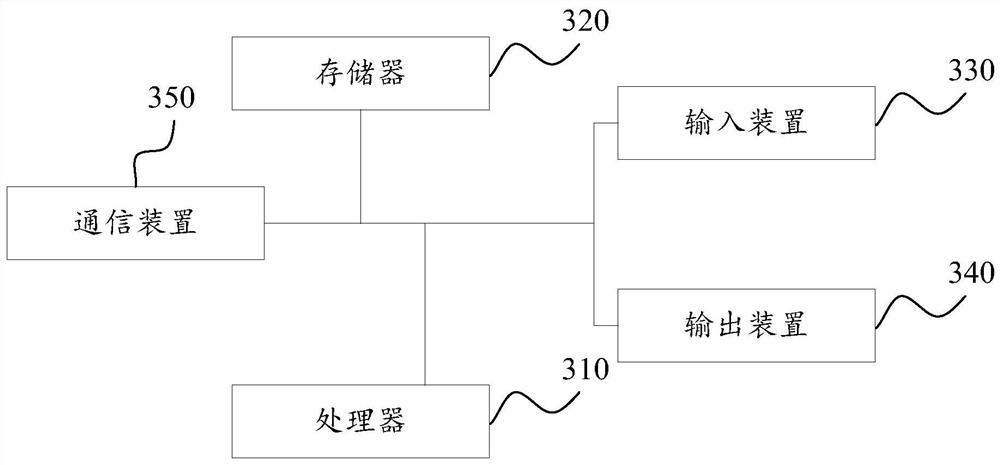
[0090] image 3 It is a schematic structural diagram of a terminal device provided by Embodiment 3 of the present invention, and the terminal device is a specific hardware presentation solution of the operation device of the above-mentioned vulnerability scanning method based on log analysis. Such as image 3 As shown, the terminal device includes a processor 310, a memory 320, an input device 330, an output device 340, and a communication device 350; the number of processors 310 in the terminal device may be one or more, image 3 A processor 310 is taken as an example; the processor 310, memory 320, input device 330, output device 340, and communication device 350 in the terminal device can be connected through a bus or other methods, image 3 Take connection via bus as an example.
[0091] The memory 320, as a computer-readable storage medium, can be used to store software programs, computer-executable programs and modules, such as program instructions / modules correspondin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com