Confusion communication method based on protocol, client terminal, server and storage medium
A technology of client terminal and communication method, which is applied in the direction of digital transmission system, data exchange network, electrical components, etc., and can solve the problems of wrong interception of application or service by DPI system, low flexibility and applicability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
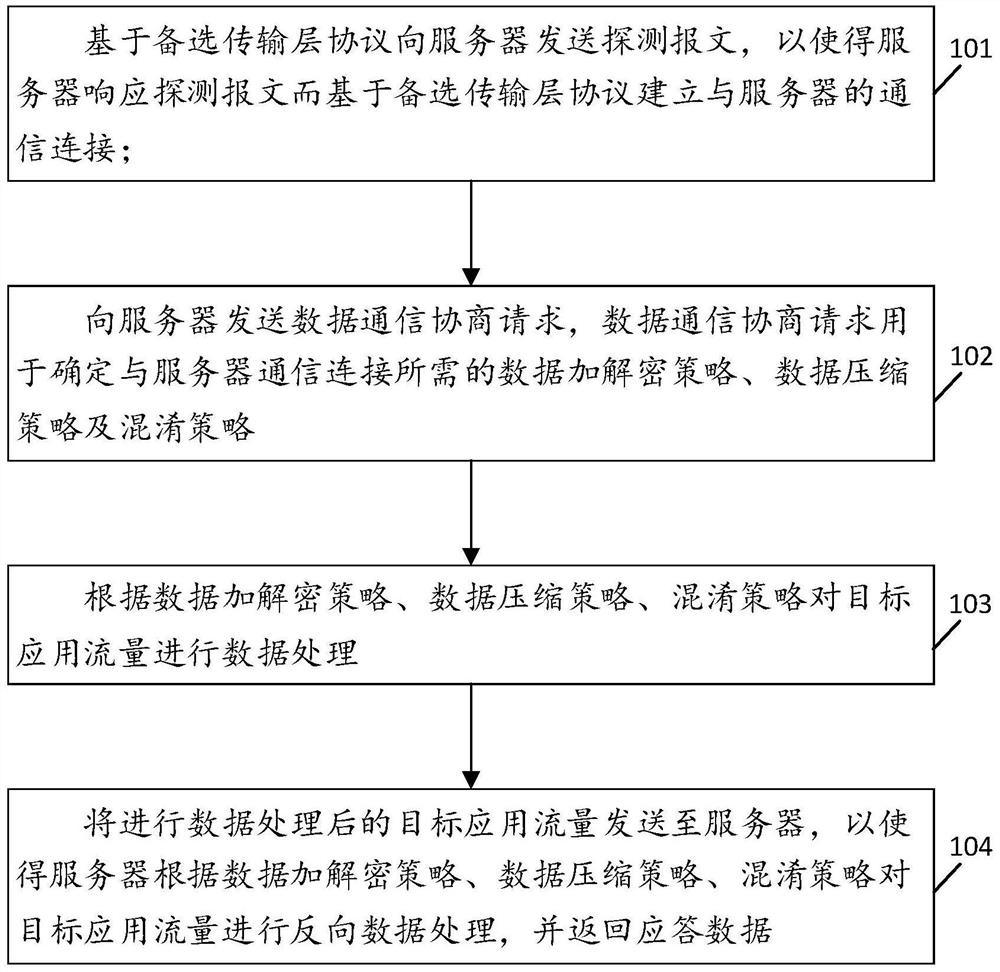
[0059] see figure 1 , figure 1 It is a schematic flowchart of a protocol-based obfuscated communication method disclosed in an embodiment of the present application, where the method is applied to a client terminal. Such as figure 1 As shown, the method of the embodiment of the present application includes steps:
[0060] 101. Send a detection message to the server based on the alternative transport layer protocol, so that the server responds to the detection message and establishes a communication connection with the server based on the alternative transport layer protocol;
[0061] 102. Send a data communication negotiation request to the server, where the data communication negotiation request is used to determine the data encryption and decryption strategy, data compression strategy, and obfuscation strategy required for the communication connection with the server;
[0062] 103. Perform data processing on target application traffic according to data encryption and decr...
Embodiment 2
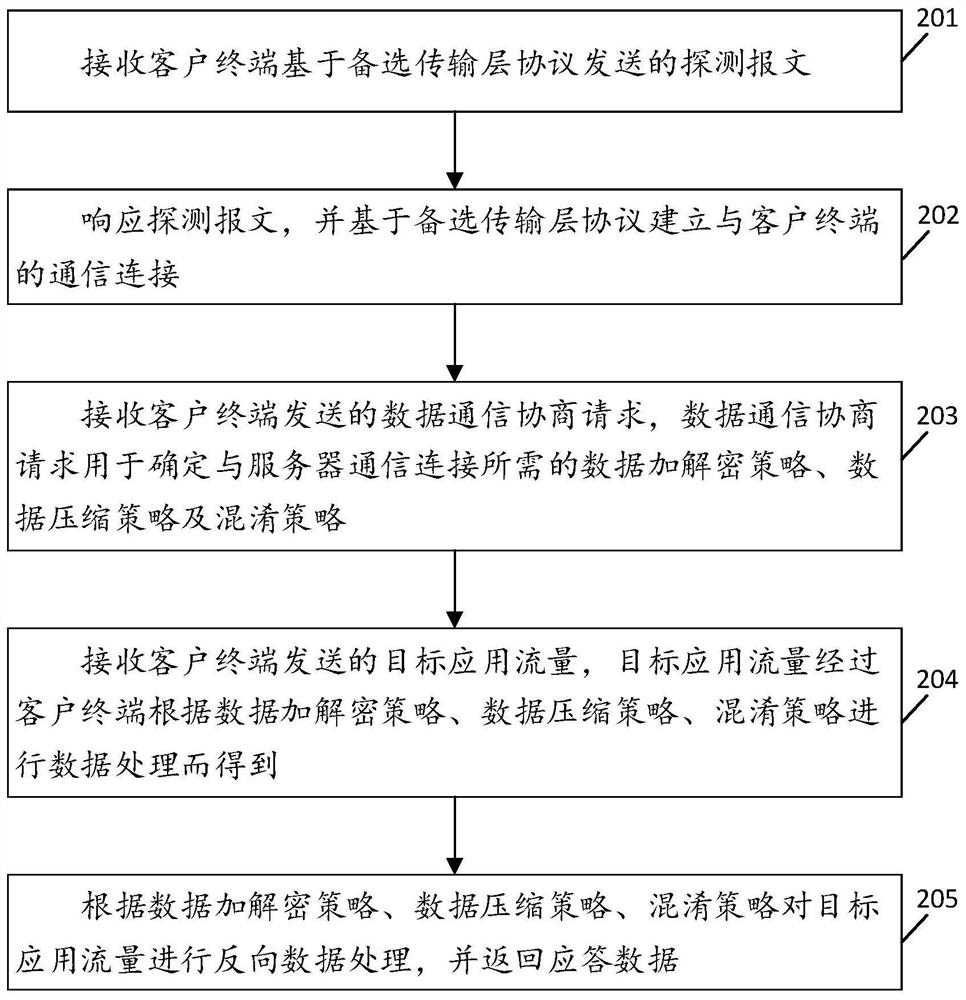
[0087] see figure 2 , figure 2 It is a schematic flowchart of a protocol-based obfuscated communication method disclosed in the embodiment of this application. Wherein, the method of the embodiment of the present application is applied to the server, and the method of the embodiment of the present application includes steps:
[0088] 201. Receive the detection message sent by the client terminal based on the alternative transport layer protocol;
[0089] 202. Respond to the detection message, and establish a communication connection with the client terminal based on an alternative transport layer protocol;
[0090] 203. Receive a data communication negotiation request sent by the client terminal, where the data communication negotiation request is used to determine the data encryption and decryption strategy, data compression strategy, and obfuscation strategy required for the communication connection with the server;
[0091] 204. Receive the target application traffic s...
Embodiment 3
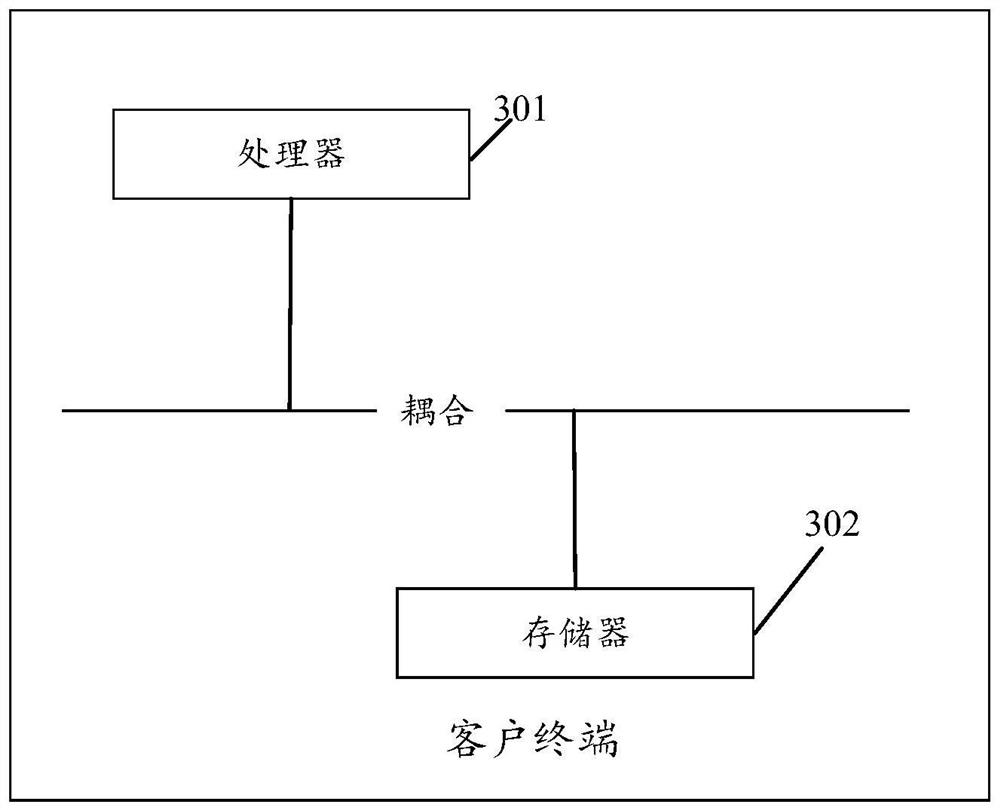
[0106] see image 3 , image 3 It is a schematic structural diagram of a client terminal disclosed in the embodiment of this application. Such as image 3 As shown, the client terminal of the embodiment of the present application includes:
[0107] Processor 301;
[0108] The memory 302 is configured to store machine-readable instructions, and when the instructions are executed by the processor, execute the protocol-based obfuscated communication method according to Embodiment 1 of the present application.
[0109] In the embodiment of the present application, the client terminal can detect the transport layer protocol applicable to the server with the server, and then match the transport layer protocol of the server and establish a communication connection with the server. In this way, the client terminal can communicate with the server based on different transport layer protocols. Communication connections, and then support the proxy and confusion of multiple transport l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com