Privacy protection method and system for enterprise DID identity system
A privacy protection system and privacy protection technology, applied in digital data protection, business, data processing applications, etc., can solve problems such as affecting enterprise efficiency, lengthy review process, and non-transparent business processes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
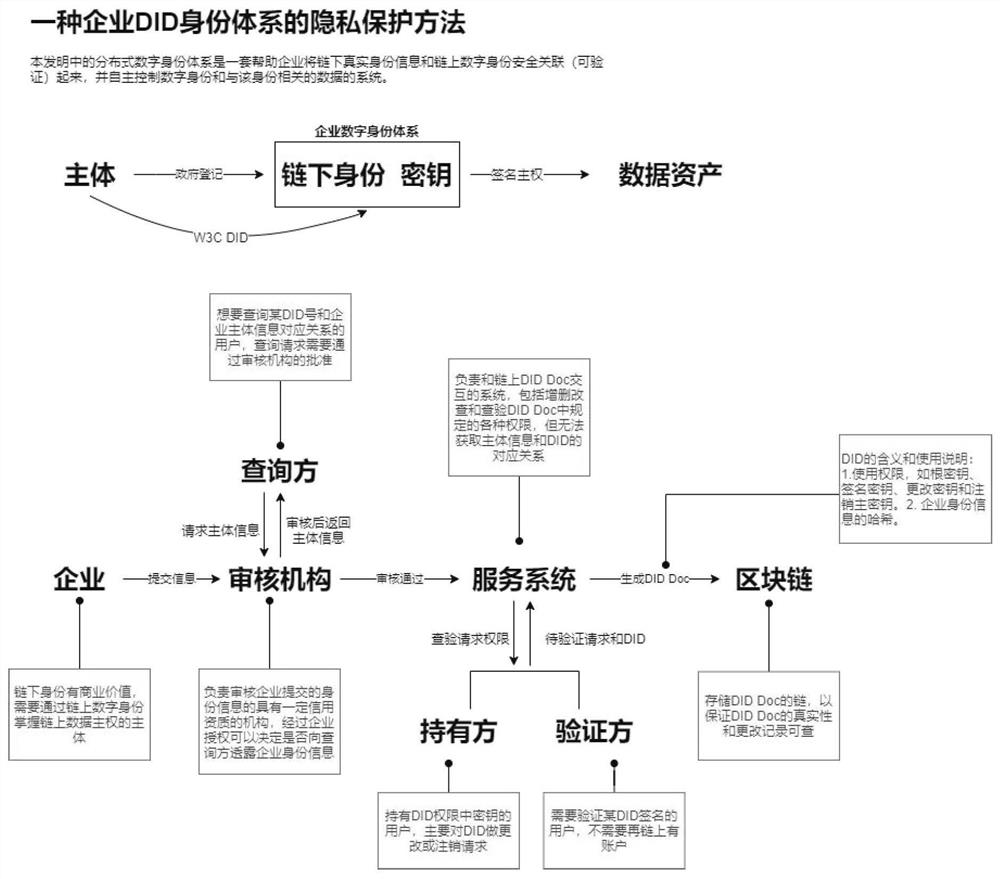
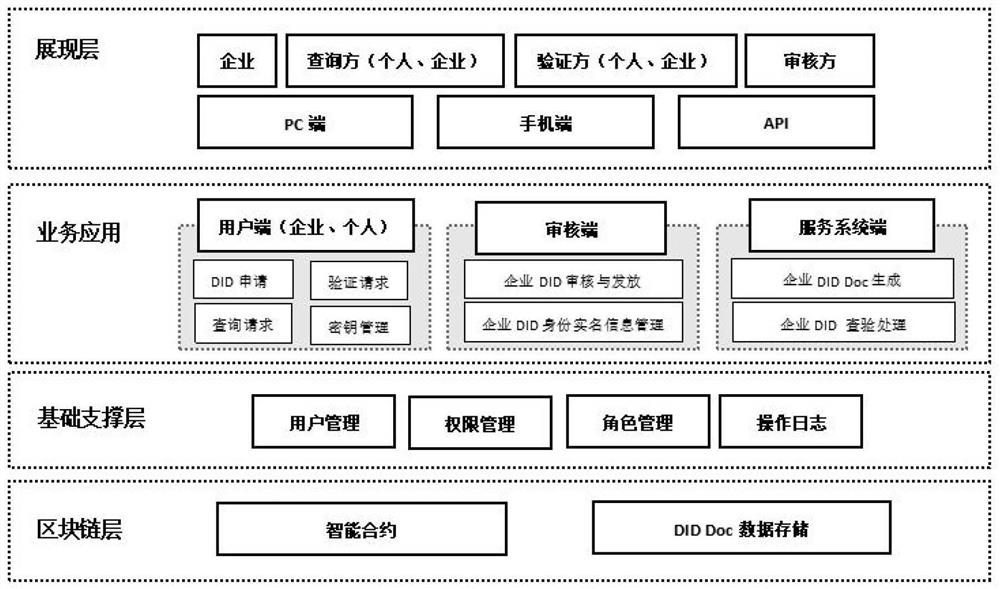
[0044] This is a distributed enterprise digital identity system, which helps enterprises securely and verifiably associate real identity information under the chain with digital identities on the chain, and independently control digital identities and data related to the identity. The present invention applies the DID technology to the enterprise identity scene to realize the self-control of the enterprise identity data. The authenticity of the corporate identity depends on the review of the audit organization under the chain. Enterprises can provide their own DID information to the querying party, and authorize the querying party to query the mapping relationship between the DID identity on the chain and the real identity off the chain at the audit agency.
[0045] The difficulties of the present invention include: 1) Generation and management of enterprise DID 2) Binding of enterprise DID and entity identity under the enterprise chain, while the mapping relationship is invis...
Embodiment 2
[0073] Embodiment 2 is a modification of embodiment 1
[0074] An application scenario is listed here, which is the credit penetration scenario in blockchain supply chain finance.
[0075] The commercial core of blockchain supply chain finance is to transfer the credit of a large downstream core enterprise to the upstream supplier through credit penetration, so as to reduce the financing cost of the upstream supplier, shorten the account period, and revitalize the enterprise. Liquid assets, increased efficiency.
[0076] In the process of credit penetration, it is assumed that the core enterprise A transfers the company's X share of digital credit to its first-tier supplier B through the blockchain, and B then splits it and transfers it to the second-tier suppliers C and D. A and C, A and D have no direct supply relationship, and sometimes in real business scenarios, B does not want A to know the detailed information of secondary suppliers C and D. At this time, the second-t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com