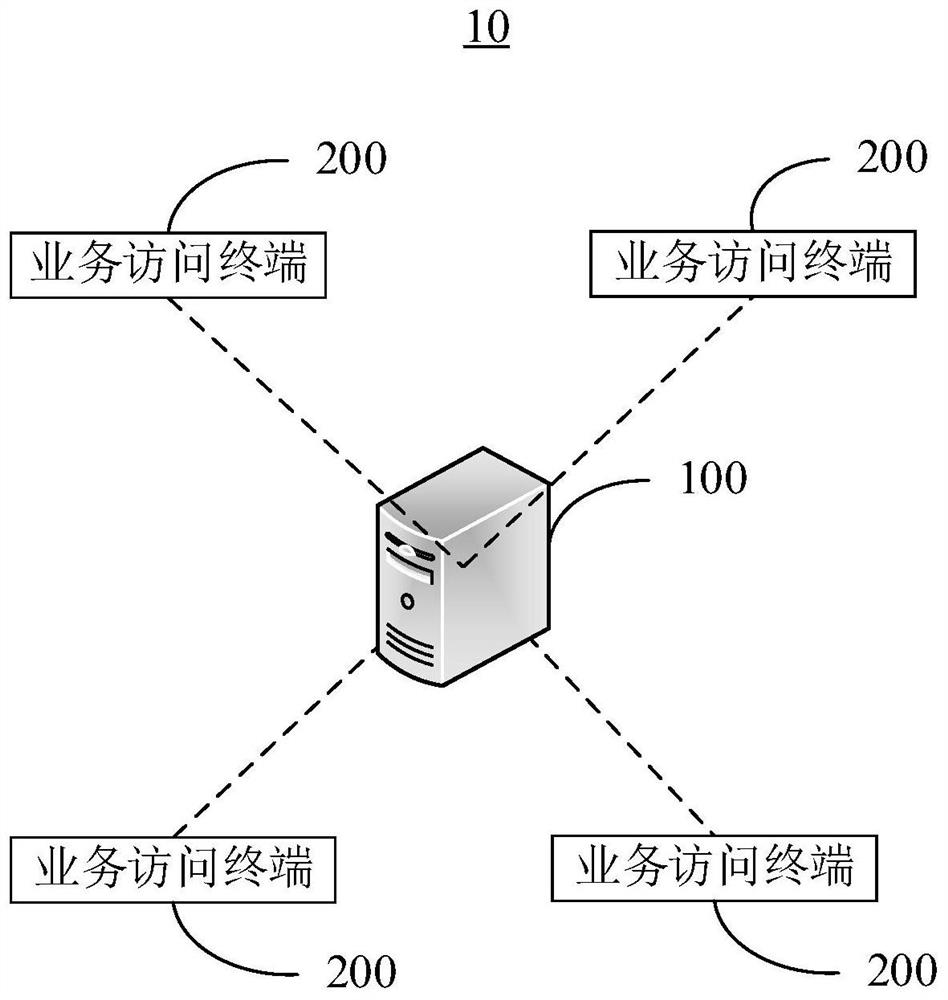
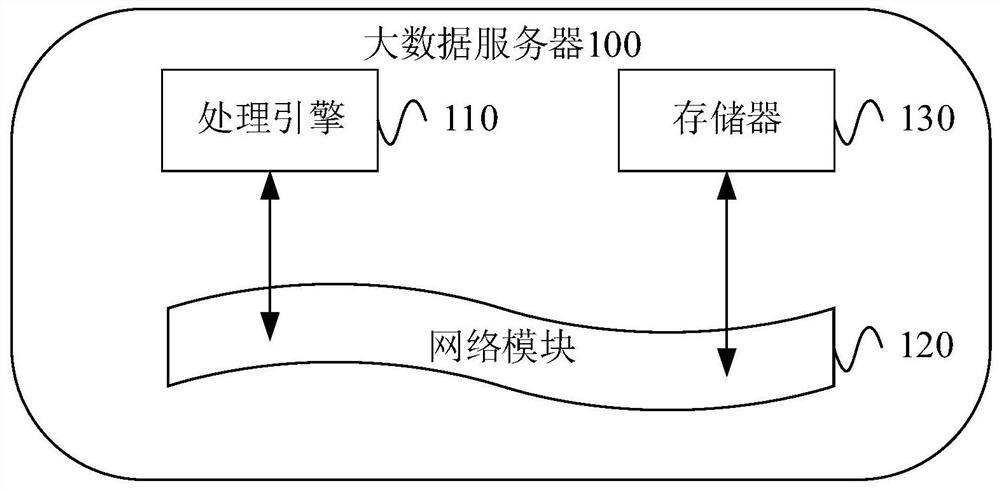
Data anti-intrusion method based on big data and artificial intelligence and big data server
A technology of artificial intelligence and big data, applied in electrical components, transmission systems, etc., can solve the problems of firewall being breached, data intrusion, difficult firewall adaptive upgrade and optimization, etc., to avoid being breached, ensure reliability, and improve intrusion. The effect of defensive performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach A
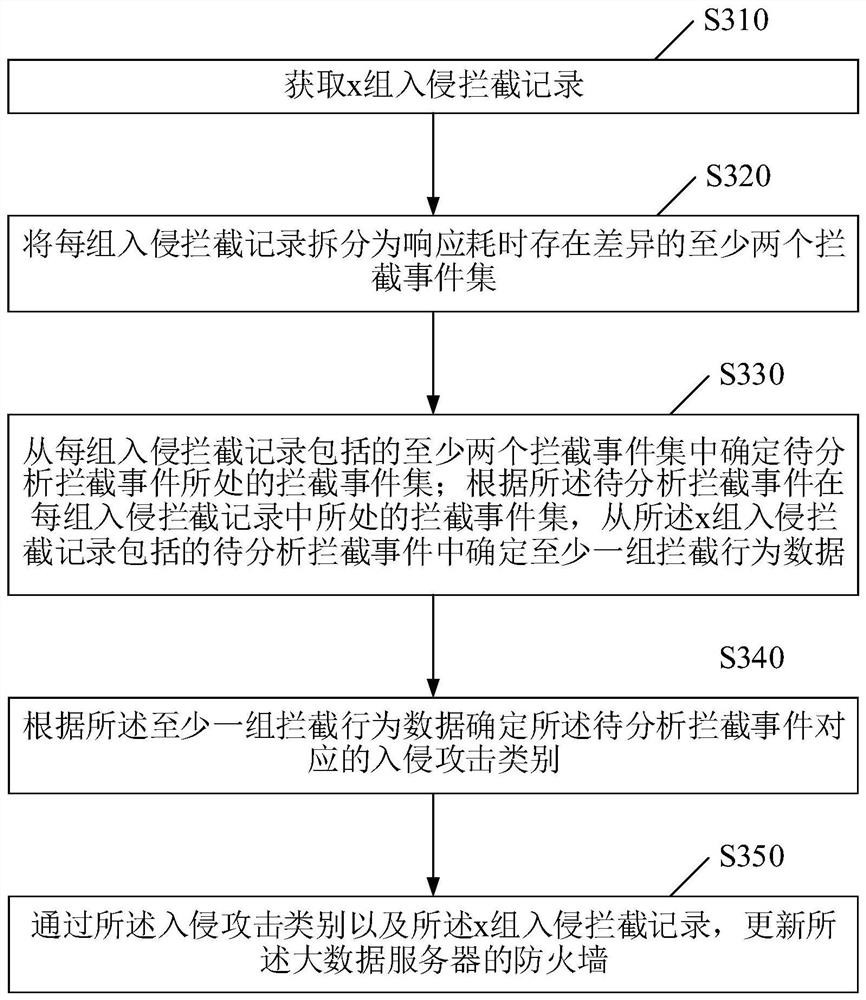
[0034] Embodiment A, according to the preset configuration information between response time consumption and interception mode, each group of intrusion interception records is split into at least two interception event sets with differences in response time consumption. For example, the configuration information may be a mapping relationship between response time consumption and interception mode.
Embodiment approach B
[0035] Embodiment B, by counting the time-consuming response and interception mode of each interception event set in the intrusion interception records within the preset time period, the configuration information between the time-consuming response and the interception mode is determined; according to the determined configuration information, each The group intrusion interception record is split into at least two interception event sets with differences in response time. For example, the preset time period can be designed according to actual conditions, such as several seconds or several minutes, which is not limited here.
[0036] In the actual implementation process, there may be multiple ways to determine the interception behavior data. In order to ensure that the interception behavior data can be quickly and accurately determined in different business scenarios, thereby improving the update efficiency of the firewall, according to the method described in step S330 Describe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com