NAT security and access control method and device, equipment and storage medium
A technology of security control and equipment, applied in the field of network communication, can solve problems such as hidden dangers of access equipment and central office equipment, and achieve the effect of saving software and hardware entry resources and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
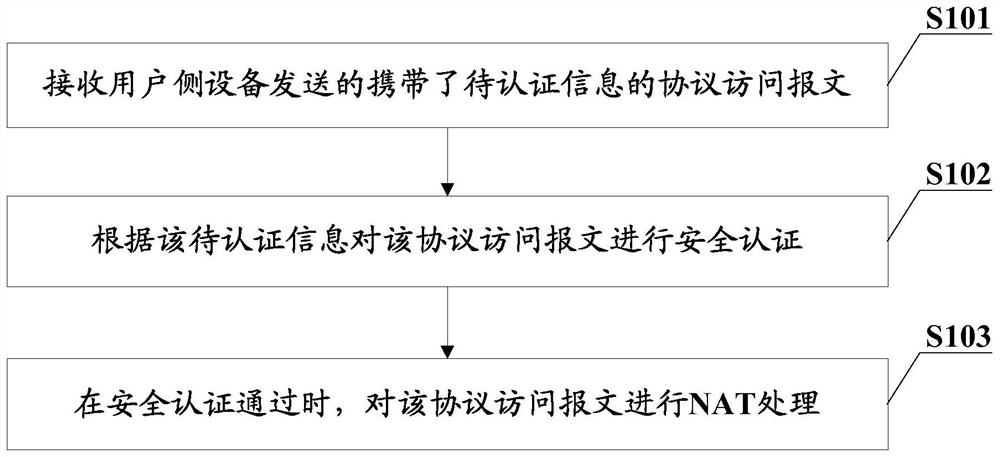
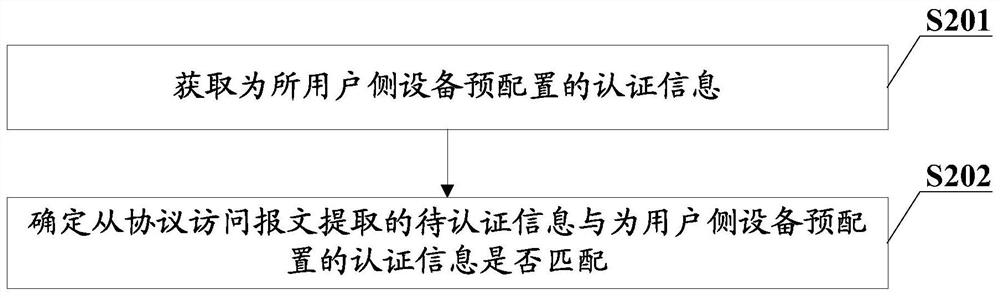
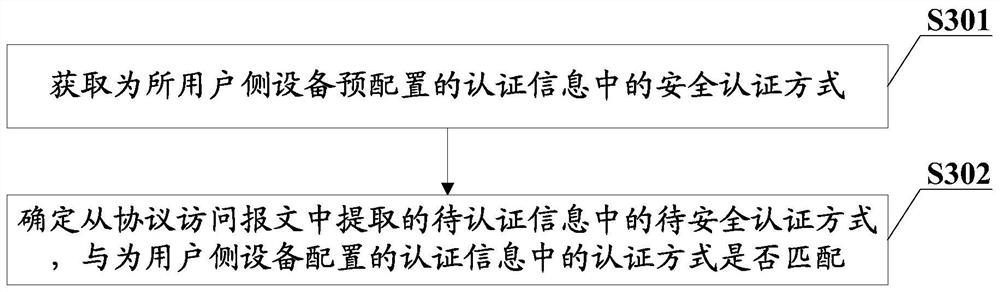
[0039] In the related technology, the access device directly performs NAT processing on the received protocol access message without performing security verification, which not only causes the resources of the access device to be maliciously occupied, but also gives the access device and the local end device For the problem of potential safety hazards, this embodiment provides a NAT security control method. When the user-side device sends a protocol access message, the protocol access message sent includes information to be authenticated, and the access device receives the information sent by the user-side device. After accessing the protocol access packet, the protocol access packet is authenticated according to the information to be authenticated in the protocol access packet. Only when the authentication is passed, the protocol access packet is NAT-processed. Only the protocol access packets sent by the user-side device of the identity can be processed normally, which not on...
Embodiment 2
[0078] This embodiment provides a NAT security control device, which can be set in various access devices supporting the NAT function. Please refer to Figure 6 As shown, the NAT security control device includes:
[0079] A message receiving module 601, configured to receive a protocol access message carrying information to be authenticated and sent by the user-side device;
[0080] The NAT security control module 602 is configured to perform security authentication on the protocol access message according to the information to be authenticated in the received protocol access message, and perform NAT processing on the protocol access message when the security authentication is passed. For the specific authentication control process, please refer to the above-mentioned embodiments, which will not be repeated here.
[0081] It should be understood that the above-mentioned functions of the message receiving module 601 and the NAT security control module 602 may be implemented by...
Embodiment 3
[0130] This embodiment also provides an access device with NAT function, see Figure 10 As shown, it includes a first processor 1001, a first memory 1002 and a first communication bus 1003;
[0131] The first communication bus 1003 is used to realize the communication connection between the first processor 1001 and the first memory 1002;
[0132] In an example, the first processor 1001 may be configured to execute the first computer program stored in the first memory 1002, so as to implement the steps of the NAT security control method in the above embodiments.
[0133] This embodiment also provides a user side device, see Figure 11 As shown, it includes a second processor 1001, a second memory 1002 and a second communication bus 1003;
[0134] The second communication bus 1003 is used to realize the communication connection between the second processor 1001 and the second memory 1002;
[0135] In an example, the second processor 1001 may be configured to execute the secon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com