CTID access control firmware upgrading method and system
A firmware upgrade and firmware technology, applied in software engineering design, instruments, electrical digital data processing, etc., can solve the problems of limited storage space, large firmware update size, inconvenient firmware upgrade, etc., to achieve the effect of improving utilization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
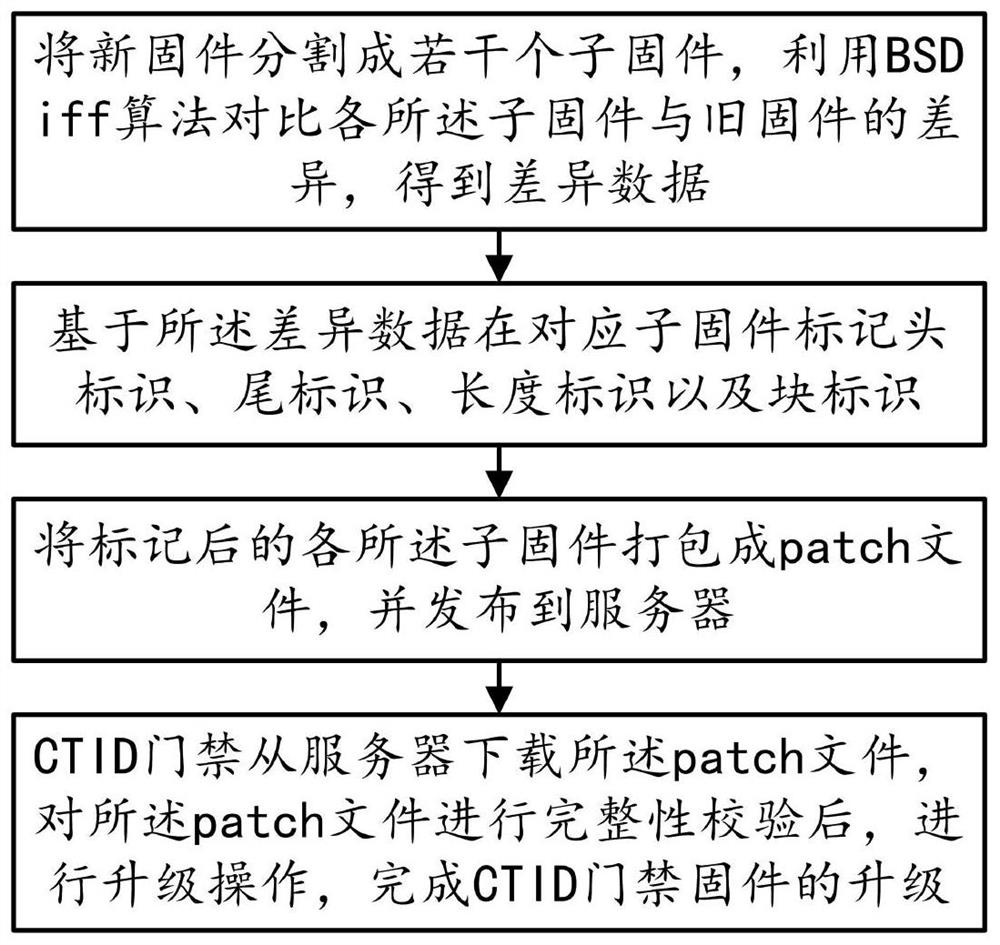
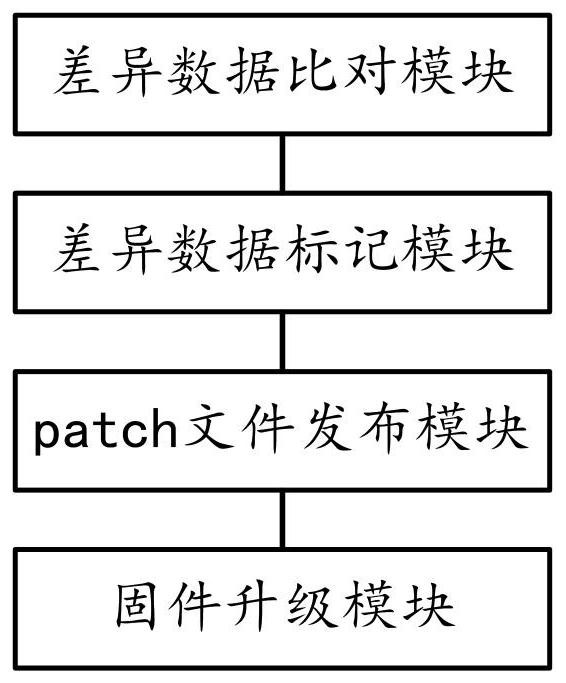
[0047] The technical solution in the embodiment of the present application has the following general idea: by dividing the new firmware into several sub-firmwares, comparing the difference between each sub-firmware and the old firmware to obtain difference data, packaging each sub-firmware with difference data into a patch file, using The patch file upgrades the CTID access control firmware to improve the utilization of the CTID access control storage space and expand more functions of the CTID access control.
[0048] Please refer to Figure 1 to Figure 2 Shown, the preferred embodiment of a kind of CTID access control firmware upgrade method of the present invention, comprises the following steps:
[0049] Step S10, the new firmware is divided into several sub-firmwares, and the difference between each sub-firmware and the old firmware is compared by using the BSDiff algorithm (difference update algorithm) to obtain difference data;
[0050] Step S20, marking the head ident...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com