Encrypted data deduplication and sharing device and method for mobile edge computing network
A technology for encrypting data and edge computing, applied in computer security devices, computing, secure communication devices, etc., which can solve the problem of ineffective data deduplication in mobile edge computing scenarios, brute force attacks, and failure to consider multiple mobile edge computing. Edge server and other issues, to achieve the effect of efficient data storage and utilization, practical application significance, and safe data storage and utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
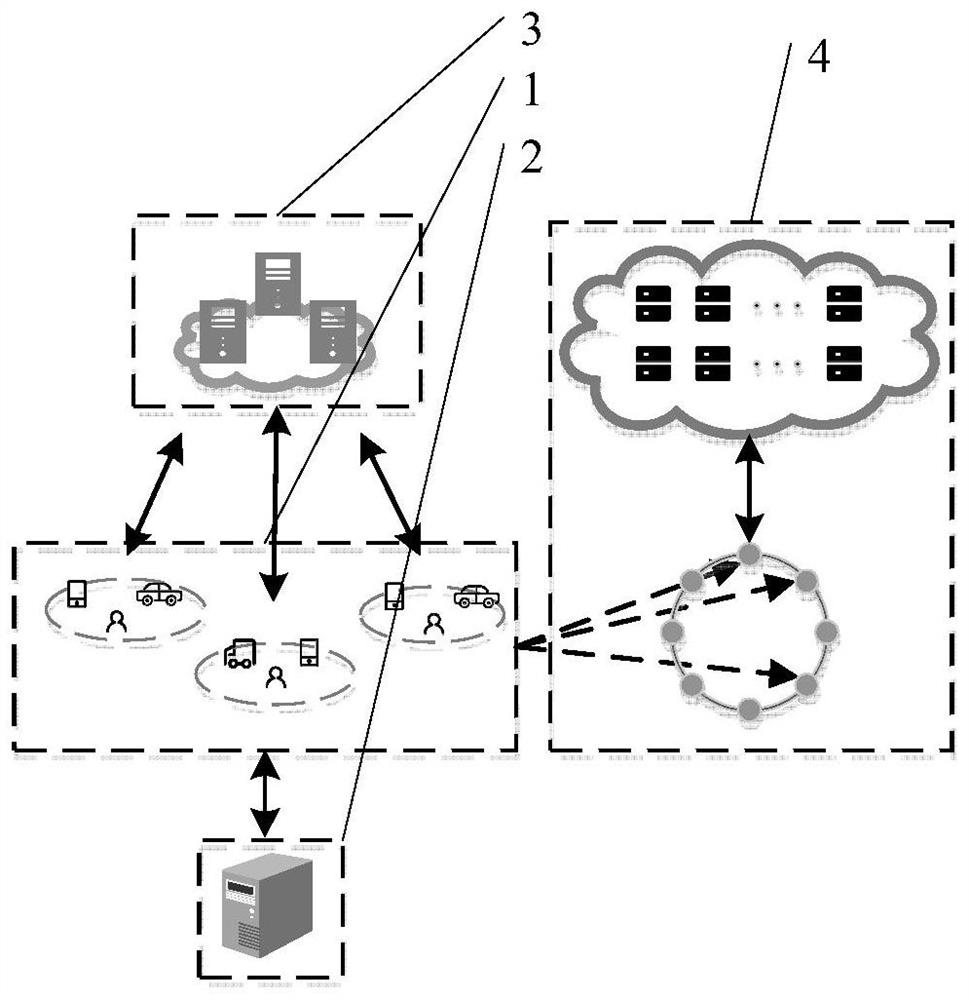
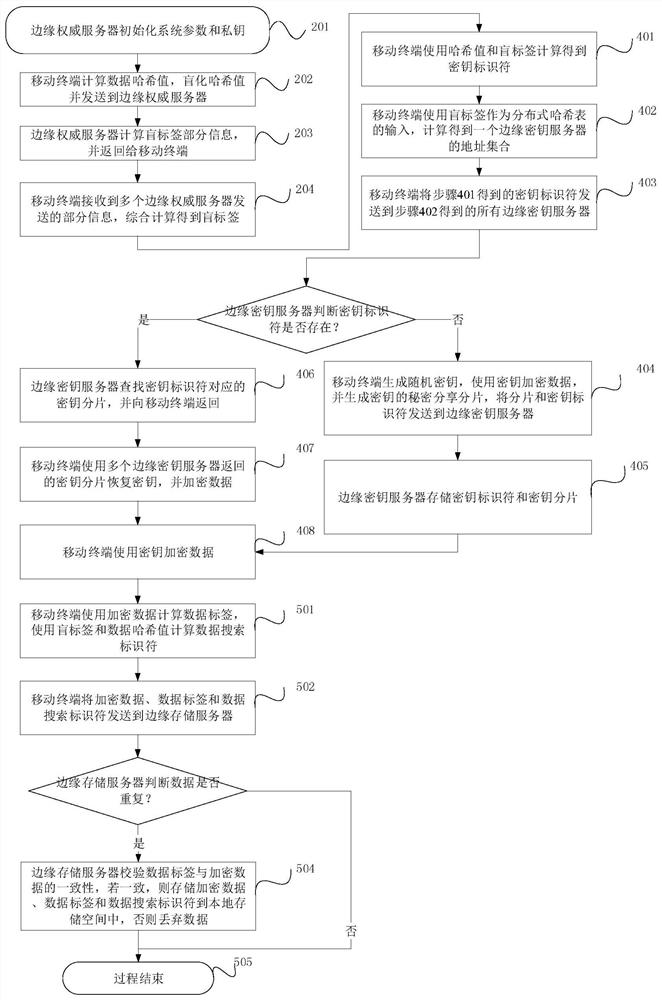
[0053] This embodiment provides a secure data deduplication and sharing device and method in a mobile edge computing network, such as figure 1 As shown: this device involves four functional entities: mobile terminal 1 , edge storage server 2 , edge authoritative server 3 and edge key server 4 . Mobile terminal 1 is the owner or user of the data; edge storage server 2 provides encrypted data storage service for mobile terminal 1, when mobile terminal 1 requests ciphertext storage service in the network, the adjacent available edge storage server 2 and mobile Terminal 1 establishes a connection and receives the encrypted data of mobile terminal 1; edge authoritative server 3 provides secure data blind label calculation service for mobile terminal 1, edge authoritative server 3 is a set of servers disclosed in the network, and mobile terminal 1 directly sends data to the set Each edge authoritative server 3 requests the data blind label calculation service; the edge key server 4 ...
Embodiment 2
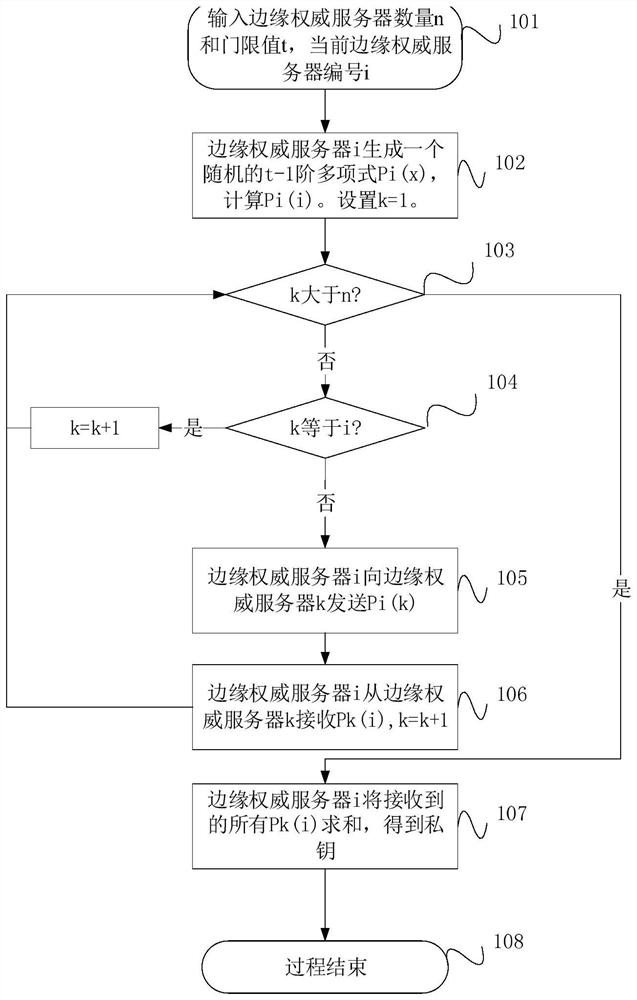
[0090] This embodiment specifically illustrates the concept of the present invention by setting the total number of edge authoritative servers n=10 and the blind label calculation threshold t=6, and the mobile terminal uploads the file D. The edge authoritative server i executes figure 2 The key initialization algorithm process of the edge authoritative server, for example, for the edge authoritative server 1:
[0091] Step 101, input the total number of edge authoritative servers n=10 and blind label calculation threshold t=6, and the edge authoritative server number 1 that executes the current algorithm;
[0092] Step 102, the edge authoritative server 1 generates a random 5th order polynomial P1(x), calculates P1(1), and sets k=1;
[0093] Step 103, if k is greater than 10, jump to step 107;
[0094] Step 104, if k=1, k=k+1, jump to step 103, otherwise continue;
[0095] Step 105, edge authoritative server 1 sends P1(k) to edge authoritative server k;
[0096] Step 106...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com