Time sequence position publishing method and system
A time series and location point technology, applied in the time series location release method and system field, can solve problems such as difficulty in resisting attacker's background knowledge attack, inflexibility, generalization failure, etc., achieve flexible privacy policy selection, avoid privacy leakage, and improve security sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
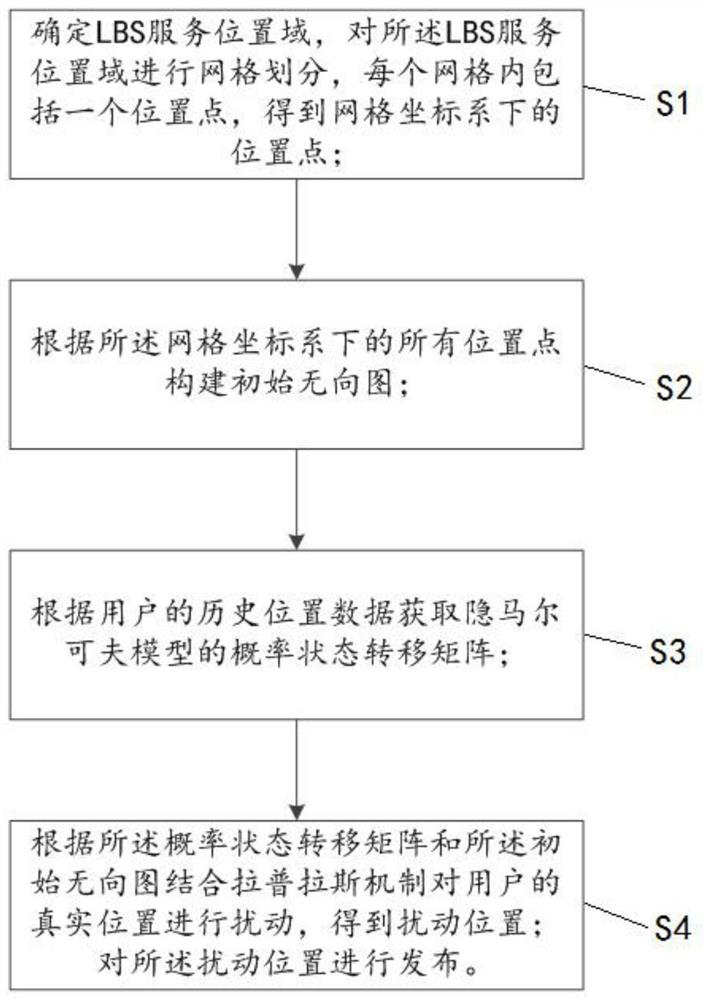
[0038] Such as figure 1 As shown, this embodiment provides a time series location release method, including:
[0039] Step S1: Determine the LBS service location domain, and divide the LBS service location domain into grids, each grid includes a location point, and obtain the location point in the grid coordinate system;
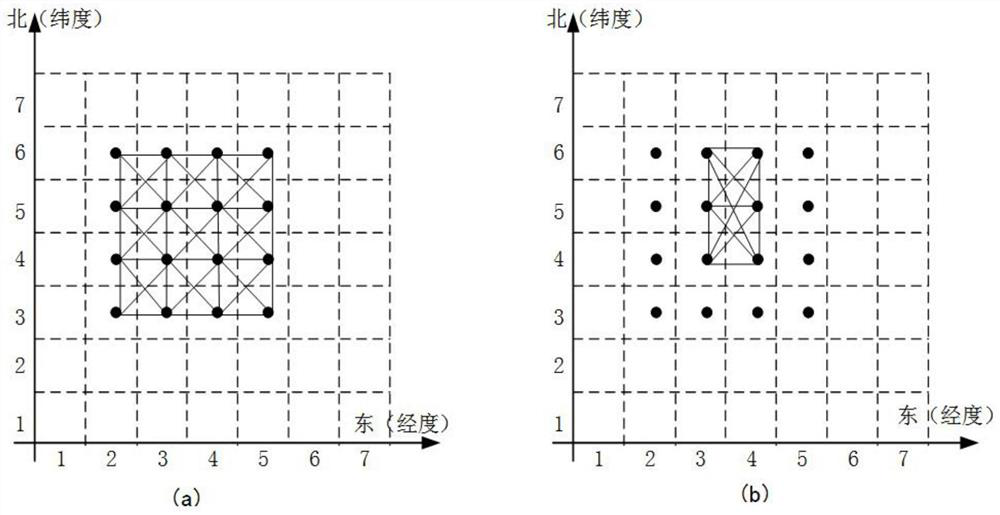
[0040]Before grid division, it is necessary to express the LBS service location domain with two-dimensional latitude and longitude coordinates, and then divide the LBS service location domain into grids based on the two-dimensional latitude and longitude coordinates. Each grid size can be 50 The standard of *50m is divided, and the LBS service location domain is divided into multiple small grids, and the number of grids (location points obtained by division) is recorded as n. Here, the location domain is divided into multiple location points, and these location points are the location points that the user moves within the range of the location domain. midd...
Embodiment 2
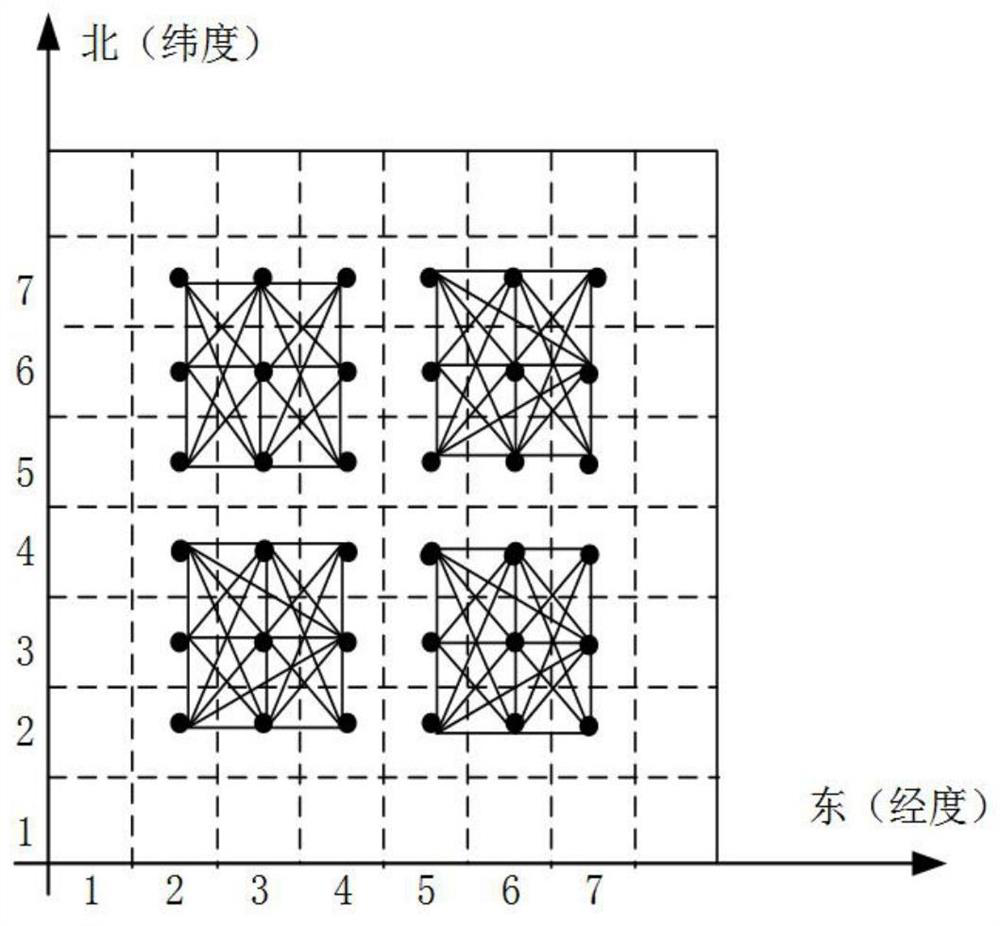
[0087] Such as Figure 5 As shown, this embodiment provides a time series location release system, including:
[0088] The location domain grid division module T1 is used to determine the LBS service location domain, each grid includes a location point, divides the LBS service location domain into a plurality of location points, and obtains the location points under the grid coordinate system;
[0089] An initial undirected graph construction module T2, configured to construct an initial undirected graph according to all position points in the grid coordinate system;
[0090] The probabilistic state transition matrix acquisition module T3 is used to obtain the probabilistic state transition matrix of the hidden Markov model according to the user's historical location data;
[0091] The disturbance location acquisition and release module T4 is used to disturb the real location of the user according to the probability state transition matrix and the initial undirected graph com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com