Location privacy protection method for social vehicle networking based on double k-anonymity
A privacy protection, social car technology, applied in the field of location privacy protection of social vehicle networking based on double k-anonymity, can solve problems such as high computational complexity and overhead, unsatisfactory location privacy protection effect, and limited degree of location privacy protection. , to achieve effective location privacy protection and reduce the probability of guessing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
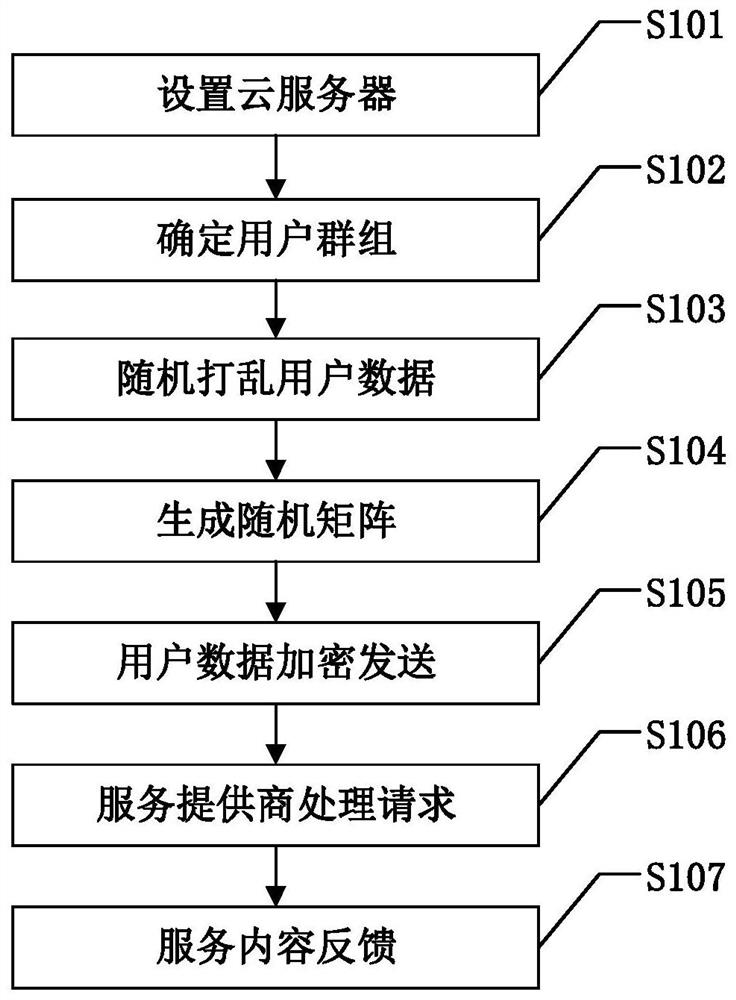
[0027] figure 1 This is a specific implementation flow chart of the method for protecting the location privacy of the social vehicle networking based on double k-anonymity of the present invention. like figure 1 As shown, the specific steps of the present invention based on the double k-anonymous social vehicle networking location privacy protection method include:
[0028] S101: Set up cloud server:
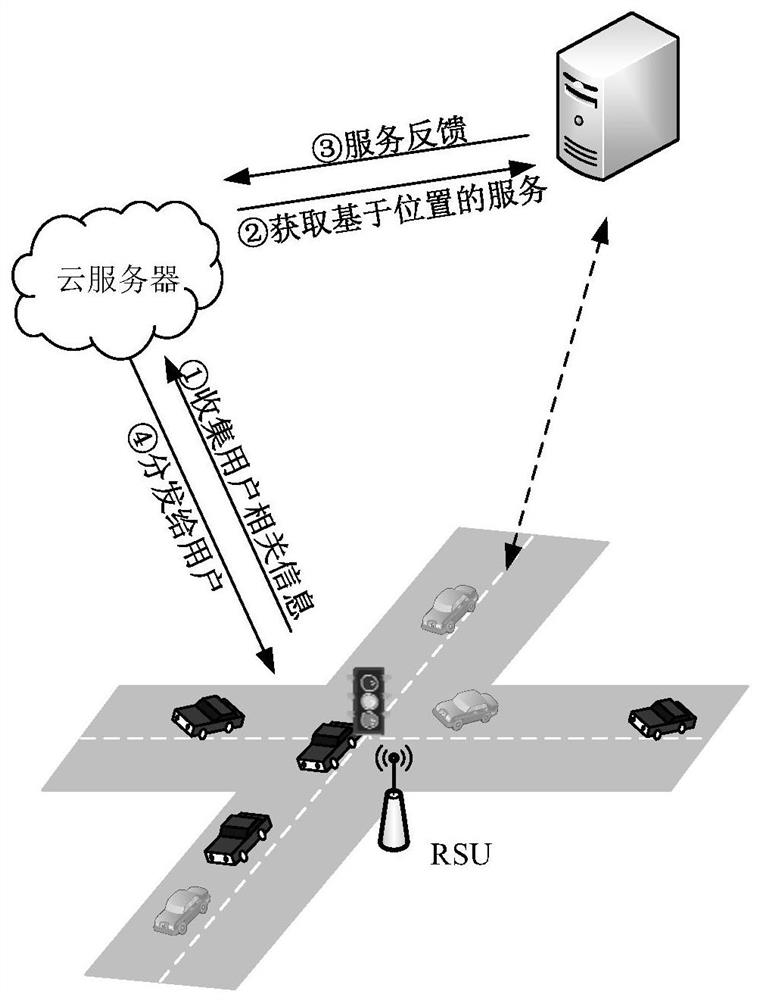
[0029] figure 2 It is a schematic diagram of the setting of the cloud server in the present invention. like figure 2 As shown, in the present invention, a cloud server is set as a trusted third party, which is used to isolate the direct communication between the service provider and the user, and realize the bidirectional transmission of information, that is, collect the user-related information from the user and distribute the location service information to the user. , obtain location-based services from service providers and receive service feedback from service provid...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com