Network-based intelligent authority management method, system, terminal and storage medium
An authority management and terminal technology, applied in the field of network management, can solve problems such as affecting the user experience and cumbersome networking process, and achieve the effect of improving the user experience, simplifying the networking process, and reducing process problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
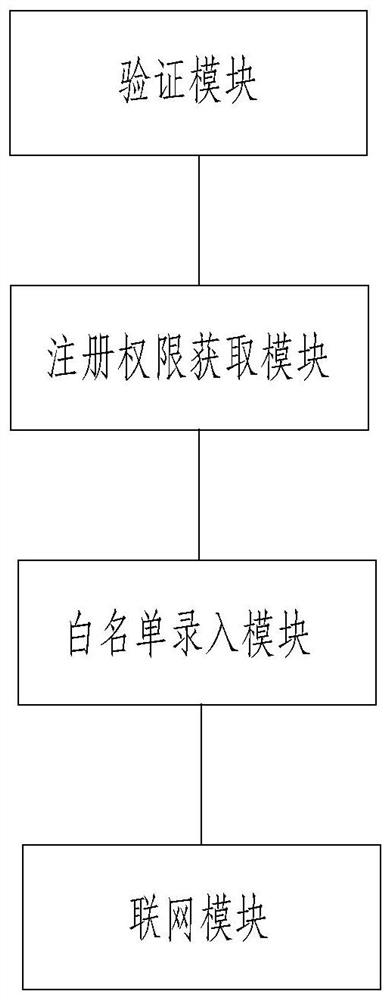
[0066] Embodiment 1: The embodiment of this application discloses a network-based intelligent authority management system. refer to figure 1 , the system includes a verification module, a registration authority acquisition module, a whitelist entry module and a networking module, and the verification module, the registration authority acquisition module, the whitelist entry module and the networking module all use a processor.
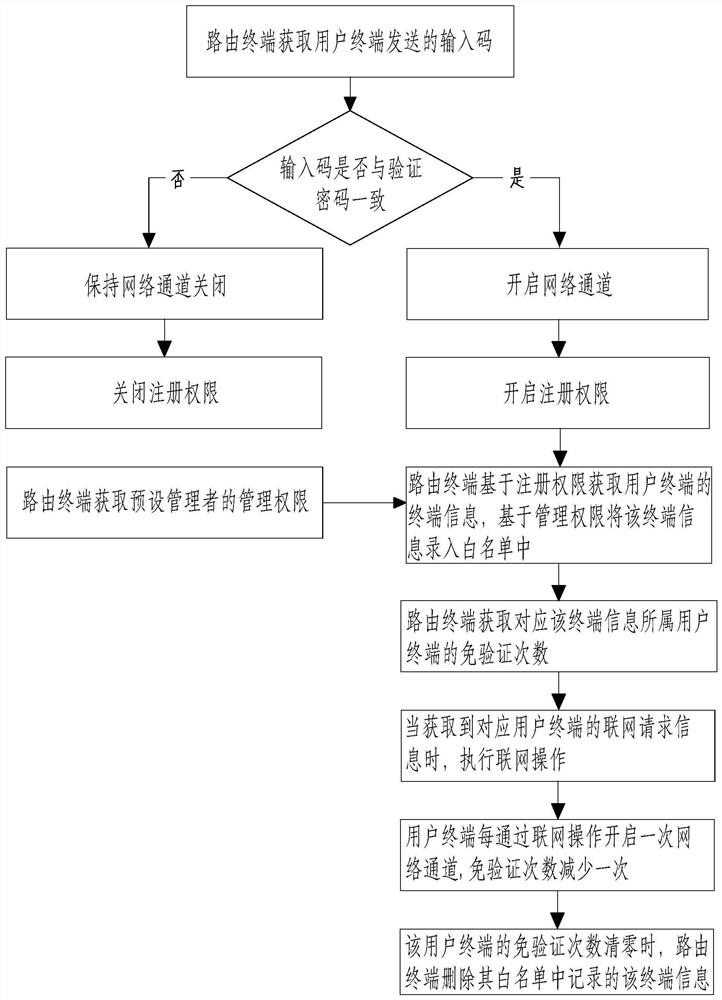
[0067] The embodiment of the present application discloses a network-based intelligent authority management method. refer to figure 2 , the network-based intelligent rights management method includes a first entry operation and a network operation, wherein the first entry operation includes the following steps:
[0068] S100: The verification module performs the first verification, the routing terminal obtains the input code sent by the user terminal, and determines whether to open the network channel with the user terminal based on the input code a...
Embodiment 2
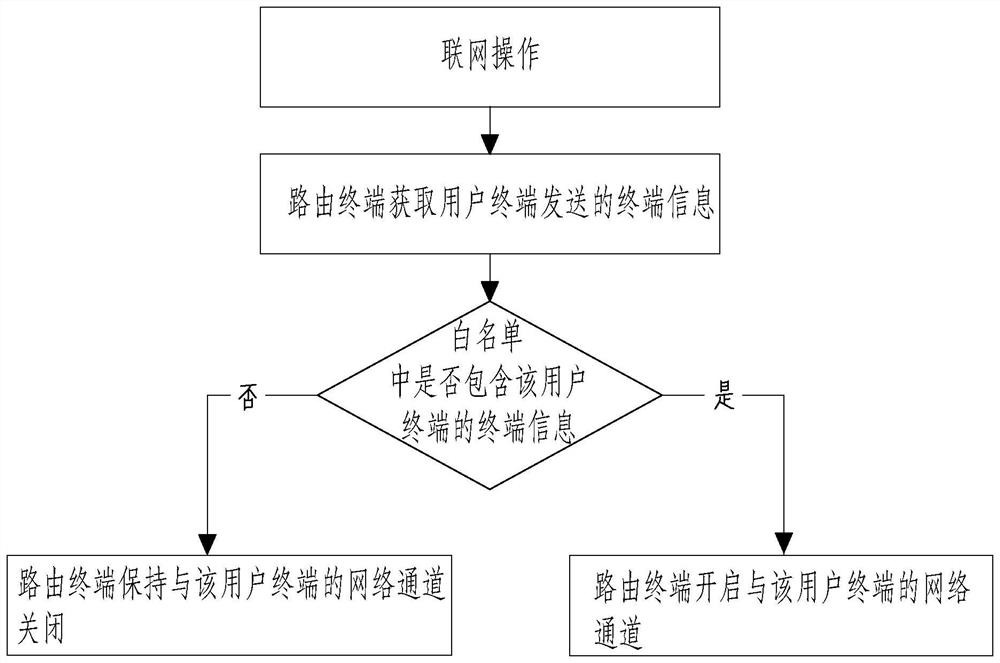
[0099] Embodiment two: refer to Image 6 , the difference from Embodiment 1 is that the temporary networking operation includes,
[0100] A1. The user terminal entered into the white list obtains the networking request information and terminal information of other user terminals;
[0101] A2. The user terminal sends the terminal information of other user terminals to the routing terminal;
[0102] Specifically, the routing terminal and the user terminal entered in the white list will receive the networking request information at the same time, and the user terminal entered in the white list can collect terminal information of other user terminals in a targeted manner, and the collection method can be Bluetooth or wifi. The user terminal sends the terminal information of other user terminals to the routing terminal, and the routing terminal records the terminal information.
[0103] A3. The routing terminal obtains temporary networking permission based on the terminal informa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com