Pluggable intelligent financial auditing platform
A financial and intelligent technology, applied in the field of financial information management systems, can solve the serious security problems of the Internet of Things, difficult "device, edge, cloud IoT basic software and hardware environments, and business applications that lack a systematic security and trustworthy framework dynamic trust assessment Mechanism and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
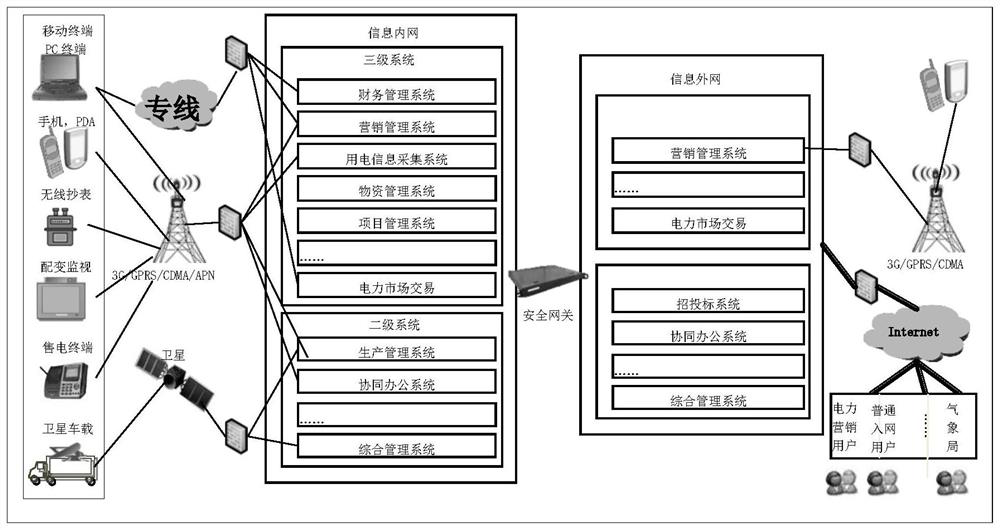
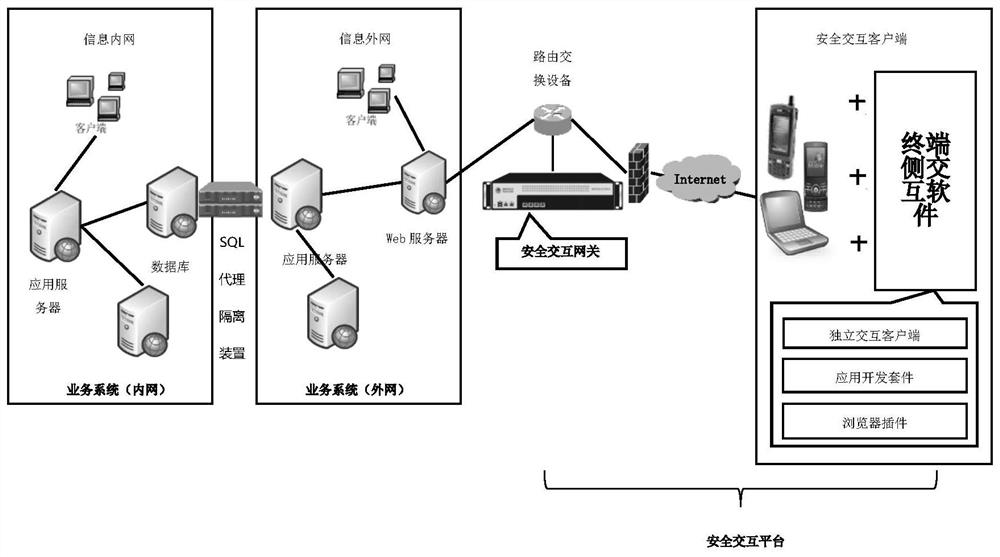
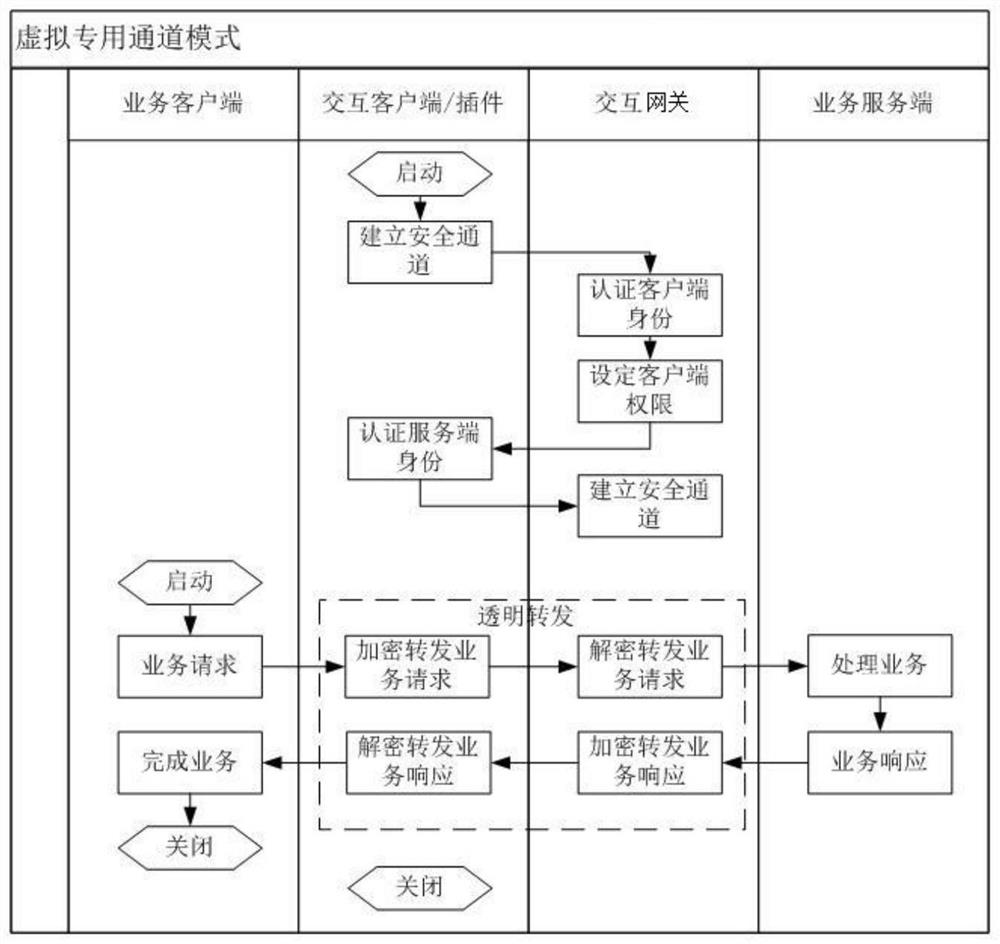
[0032] First of all, it needs to be explained that in the prior art, the financial audit application in the financial audit platform of the power company is the most widely connected business application system with various business applications in the power information network. It is deployed as a first-level system and configured in the information On the intranet side, the financial audit application implements financial audit process management according to configuration rules by exchanging financial audit data with each business application system in its second-level system and third-level system. exemplary, such as figure 1 The structure of the existing financial audit platform shown in the information intranet side runs a secondary system including business applications such as production management system and collaborative office system, and a tertiary system including business applications such as financial management system and sales management system. Each business ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com