Rapid password cracking method and system, computer program and storage medium
A cryptographic and fast technology, applied in the field of cryptography, can solve the problems of computing power, time, energy waste, etc., and achieve the effect of reducing computing power, improving success rate and efficiency, and quickly cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
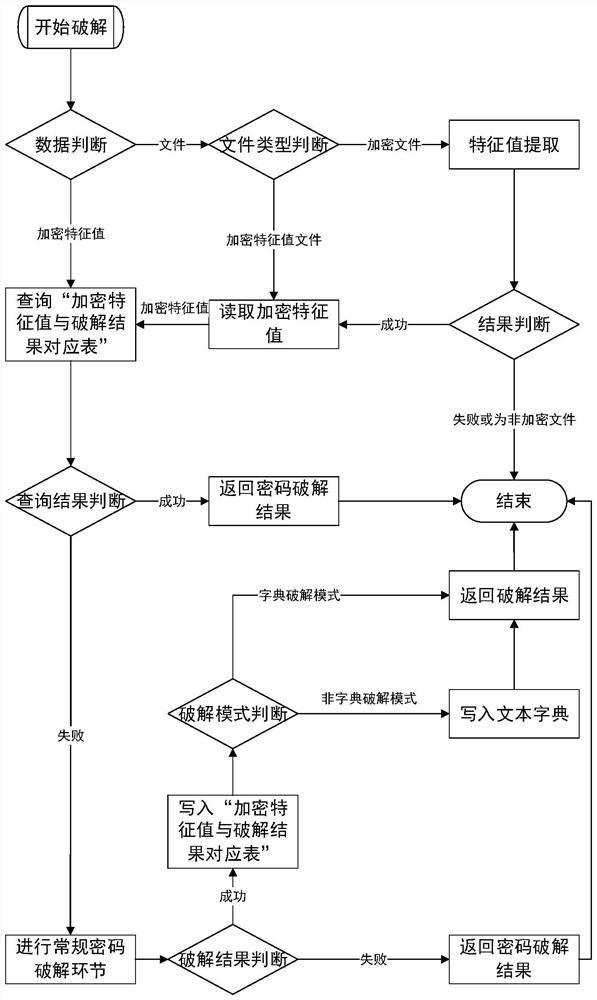
[0041] as attached figure 1 Shown is a flow chart of a method for quickly cracking passwords provided in this preferred embodiment, and the specific flow of the method for quickly cracking passwords can be as follows:
[0042] Step 1, preprocessing the target file.
[0043] Specifically, it is first judged whether the decryption target is an encrypted feature value or a file, and if the decryption target is an encrypted feature value, go directly to step 2.
[0044] If the decryption target is a file, then the file type needs to be judged. Specifically, the general file header carries file type information, and the file type can be obtained by parsing the file header. It can also be judged in conjunction with the file extension name, for example, *.doc is MS Word version 2003, and *.xlsx is MS Excel version 2007 or above. If the two methods conflict, the file type obtained by parsing the file header shall prevail. In general, the encrypted feature value file is a .txt text...
Embodiment 2
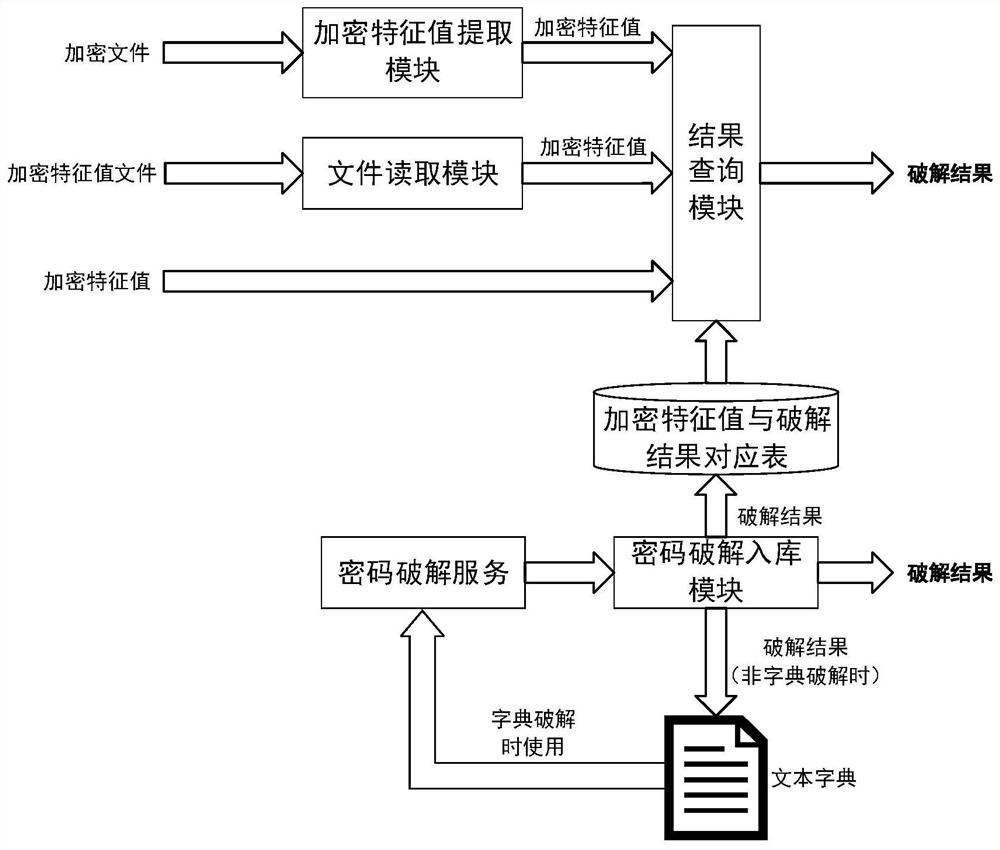
[0067] as attached figure 2 Shown is a working principle diagram of a fast password cracking system provided in this preferred embodiment. The password fast cracking system includes a file type judgment module, an encryption feature value extraction module, an encryption feature value reading module, an encryption feature value and Cracking result correspondence table, password cracking module, password cracking storage module and result query module.
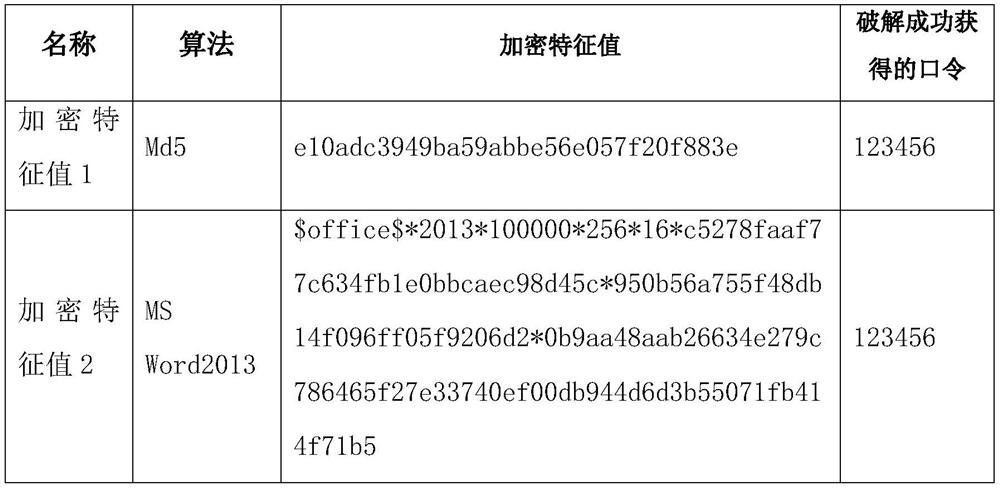
[0068] Among them, the file type judging module is used to judge the type of the decrypted target file; the encrypted feature value extraction module is used to extract the encrypted feature value of the file; the encrypted feature value reading module is used to read the encrypted feature value of the file; the encrypted feature value value and cracking result correspondence table, which is used to store the password corresponding to the encrypted feature value; the password cracking storage module is used to write the passwo...
Embodiment 3
[0071] This preferred embodiment provides a computer program, which can realize the steps in any embodiment of the method for quickly cracking passwords provided in the embodiments of the present application. Therefore, any fast password cracking method provided in the embodiments of the application can be realized For the beneficial effects of the cracking method, see the previous embodiments for details, and will not be repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com