Industrial control system-oriented intrusion detection rule matching optimization method
An industrial control system and intrusion detection technology, which is applied in the direction of instruments, calculations, and electrical digital data processing, etc., can solve problems such as low matching efficiency, insufficient discovery, unrealistic classification and sorting, etc., to shorten the alarm time and improve detection efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] Below in conjunction with accompanying drawing and embodiment the present invention is described in further detail:
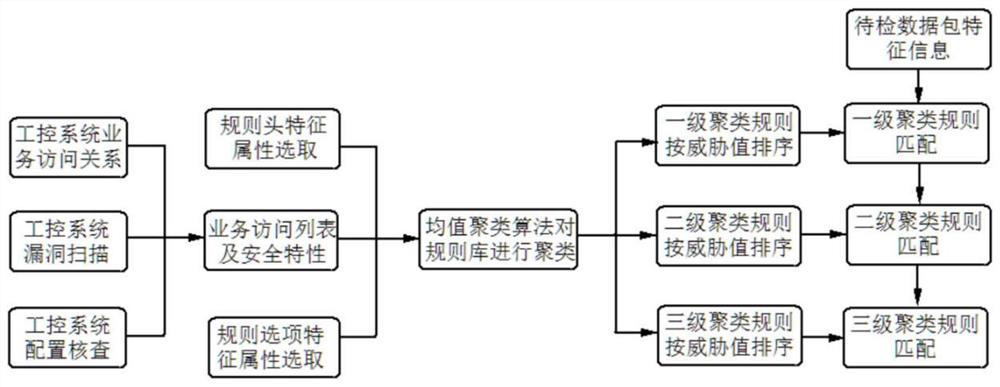
[0024] Such as figure 1 As shown, an intrusion detection rule matching optimization method for industrial control systems is illustrated by taking the open source intrusion detection system Snort as an example, including the following steps:
[0025] (1) According to the network topology of the industrial control system and the actual situation of the business system, organize the reasonable access list of the industrial control system business, including the internal access of the industrial control system and the interactive access between the internal and external, and sort out the protocol, source address, and source port corresponding to the access relationship , destination address, destination port and other information, the uncontrolled access list can be obtained from the reasonable access list of the industrial control system business; and then...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com