Method and system for sharing data and protecting copyright of electronic data
A technology of electronic data and data sharing, applied in digital data protection, digital data authentication, structured data retrieval, etc., can solve the problems of easy disclosure of privacy, easy tampering and theft of electronic evidence, etc., to improve security and prevent Piracy phenomenon, enhance the effect of supervision
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
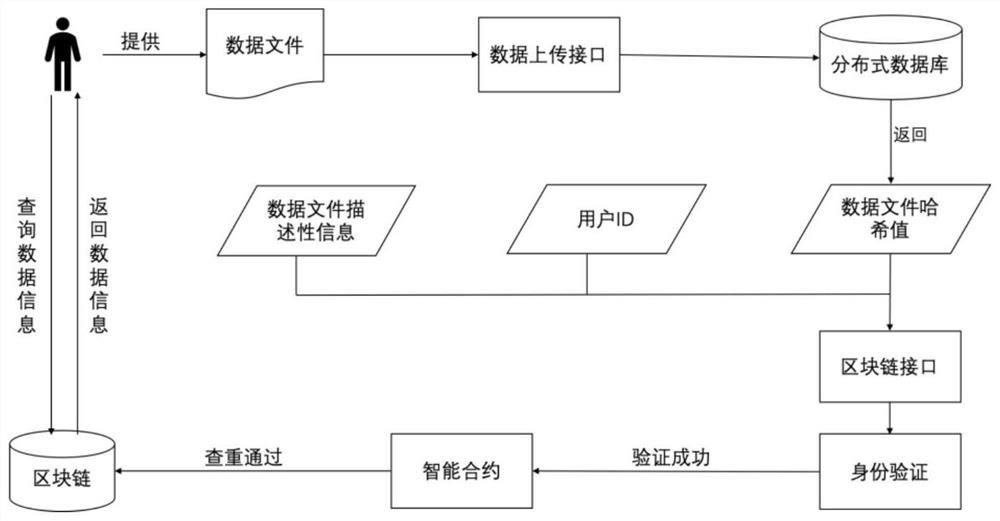
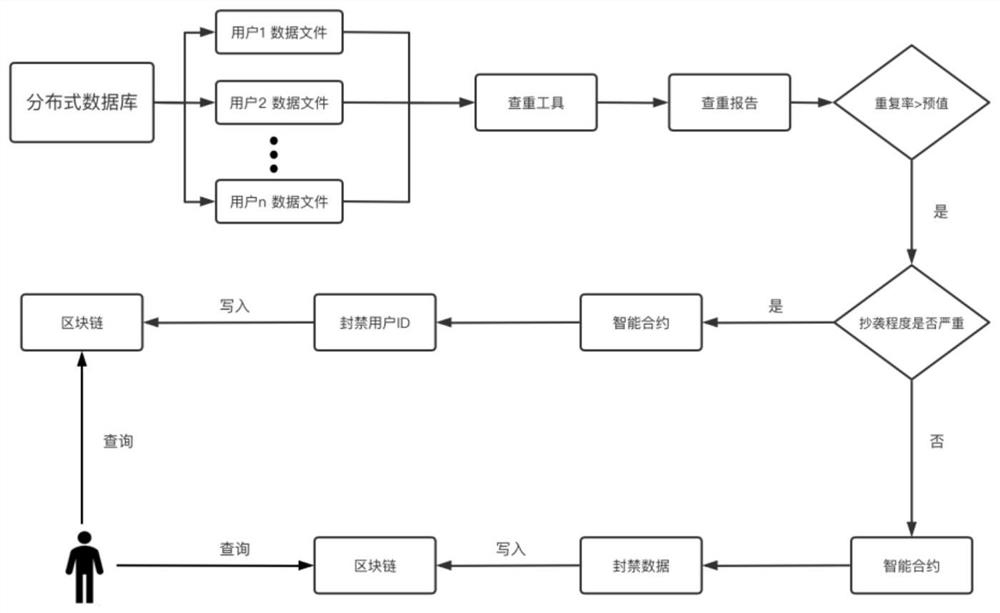
[0046]In view of the technical problems existing in the existing data storage technology that electronic data is easily tampered with, stolen, and privacy is easily leaked, this embodiment provides a method for data sharing and electronic data copyright protection according to the difficulties in the field of electronic copyright protection. A complete data protection model has been established, using a combination of storage in the blockchain and storage outside the blockchain, that is, storing specific data files in a distributed storage system outside the blockchain, and hashing the basic information and data files of the files. The hash value is stored on the blockchain. In this way, the privacy information of scientific data is protected and the data on the blockchain itself does not have the problem of data plagiarism, and the plagiarized data can be processed without deleting the data. Among them, the specific data files are not stored on the blockchain, but are stored ...
no. 2 example
[0084] This embodiment provides a system for data sharing and electronic data copyright protection, including the following modules:
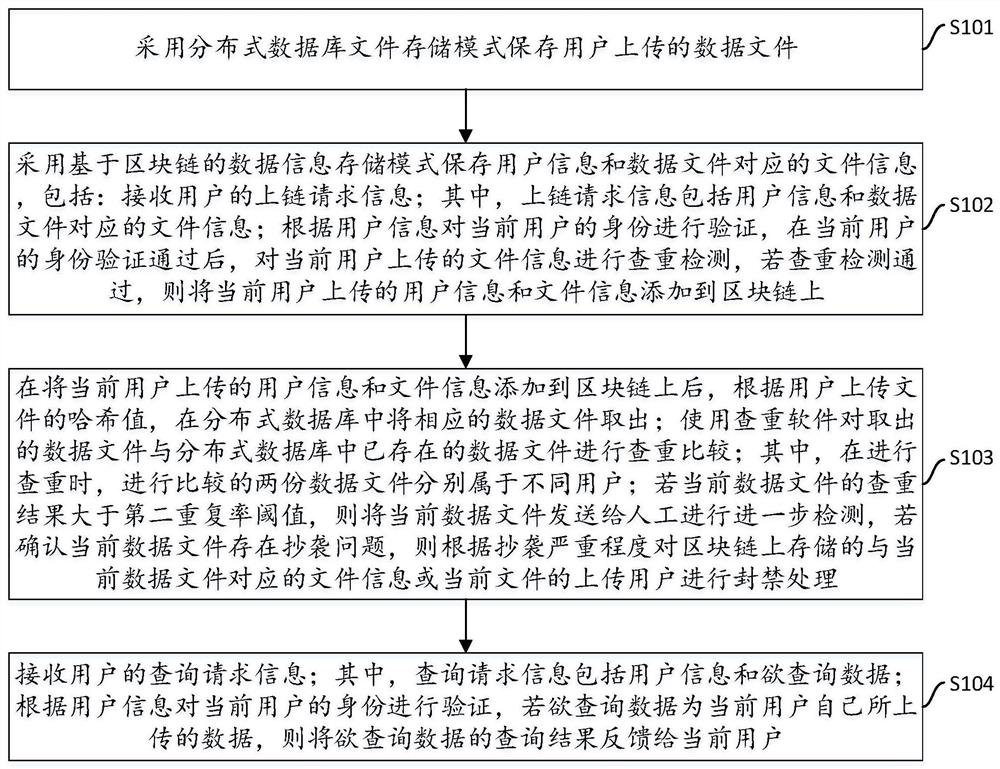
[0085] The data file storage module based on the distributed database is used to save the data files uploaded by users in the distributed database file storage mode;
[0086] The blockchain-based data information storage module is used to store user information and file information corresponding to data files in a blockchain-based data information storage mode, including: receiving the user's uplink request information, and the uplink request information includes The file information corresponding to the user information and the data file; verify the identity of the current user according to the user information, and after the identity verification of the current user passes, perform a duplicate check on the file information uploaded by the current user, if the duplicate check If passed, the user information and file information uploaded by the...
no. 3 example
[0090] This embodiment provides an electronic device, which includes a processor and a memory; at least one instruction is stored in the memory, and the instruction is loaded and executed by the processor, so as to implement the method of the first embodiment.
[0091] The electronic device may have relatively large differences due to different configurations or performances, and may include one or more processors (central processing units, CPU) and one or more memories, wherein at least one instruction is stored in the memory, so The above instruction is loaded by the processor and executes the above method.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com