Identification data encryption access method in nuclear power networked cooperative computing environment
A technology for identification data and access methods, which is applied in the field of encrypted access to identification data in the nuclear power network collaborative computing environment, can solve problems such as illegal acquisition, malicious attacks on data information, etc., to improve data information security and enhance the level of collaborative design , The effect of improving the efficiency of R & D and design
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] In order to make the above objects, features and advantages of the present invention more obvious and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments:
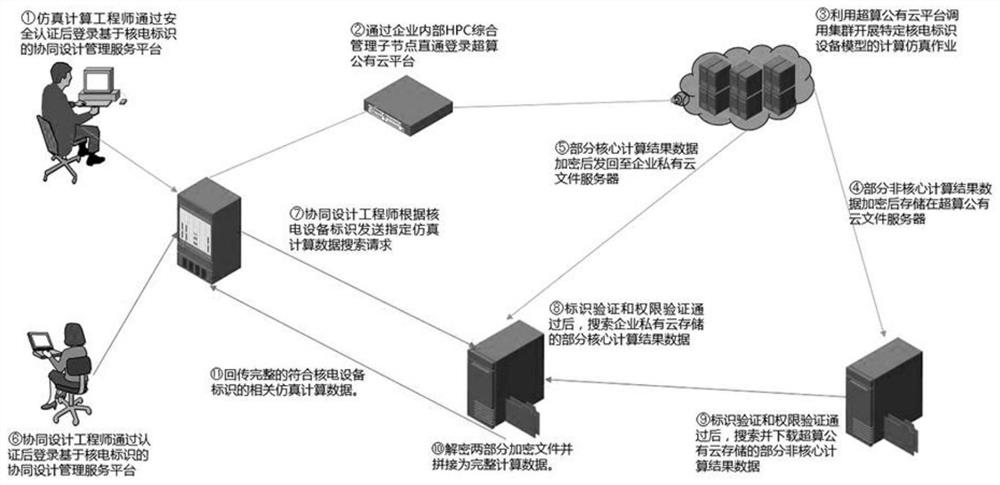
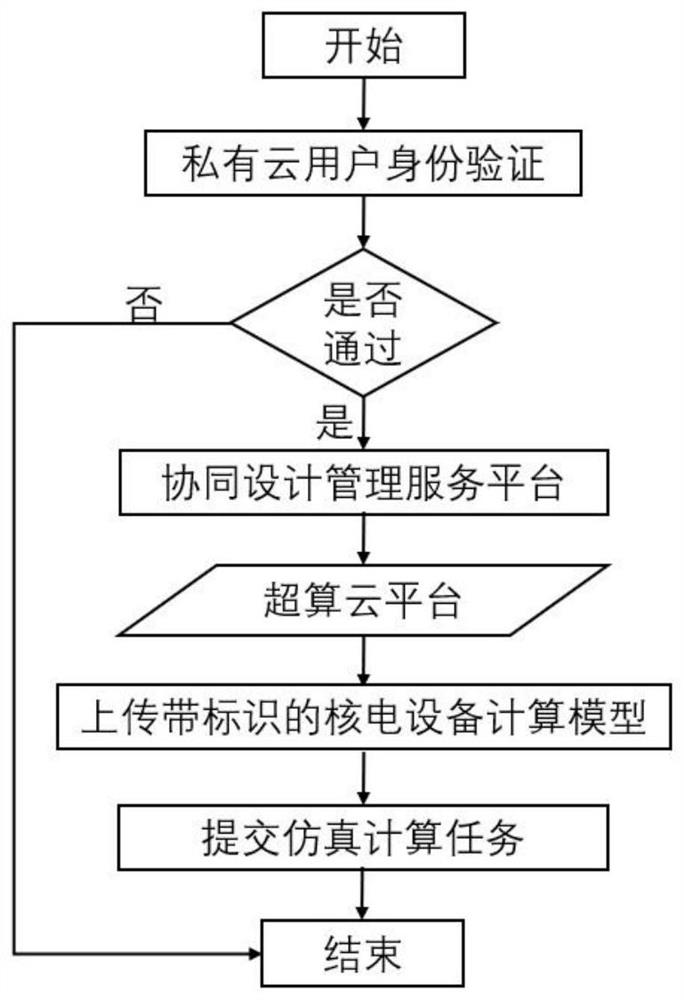
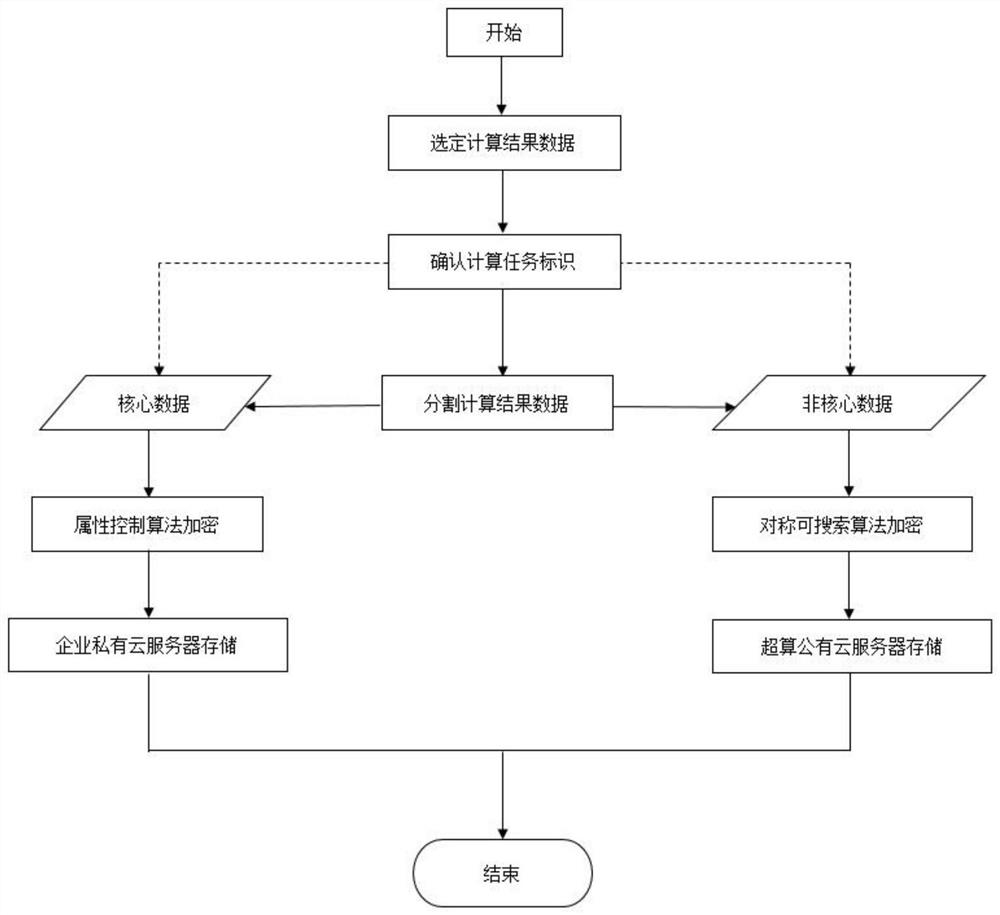
[0019] (1) When it is necessary to carry out simulation analysis of nuclear power equipment, the professional simulation calculation engineer will log in to the collaborative design management service platform based on the nuclear power identification analysis system to carry out daily work after confirming his identity through the enterprise security LDAP unified authentication mechanism. In daily work, each nuclear power equipment component opened by the user on the collaborative design platform must have a clear identification code.
[0020] The initialization algorithm INIT is enabled, and the enterprise private cloud storage server generates and outputs the public key PK and the system master key SK to the designat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com