A Data Processing System Based on Sensitive Features
A data processing system and sensitive feature technology, applied in the field of data processing, can solve problems such as insufficient precision and efficiency, and achieve the effect of improving security and timeliness, and improving precision security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
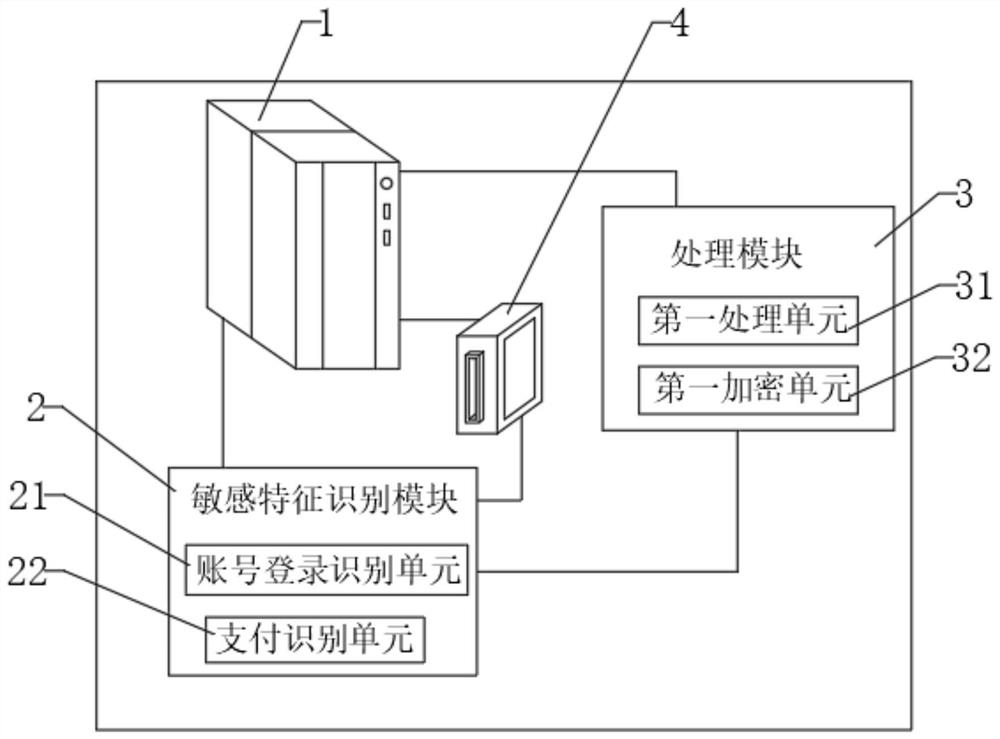
[0037] Example 1, please refer to figure 1 , a data processing system based on sensitive features, comprising a processor 1, the processor 1 is provided with a sensitive feature identification module 2, a processing module 3 and a storage module 4, and the sensitive feature identification module 2 is used to identify sensitive features , the storage module 4 is used to store sensitive features, by identifying the sensitive features, and then processing and analyzing the sensitive features through the processing module 3, the connection between the user's payment and these sensitive features can be obtained, so that the user can pay when the user pays. The transmission network and transmission data are encrypted and protected, which not only improves the efficiency of sensitive data processing, but also improves the security of sensitive data protection.
[0038] The sensitive feature identification module 2 includes an account login identification unit 21 and a payment identif...
Embodiment 2
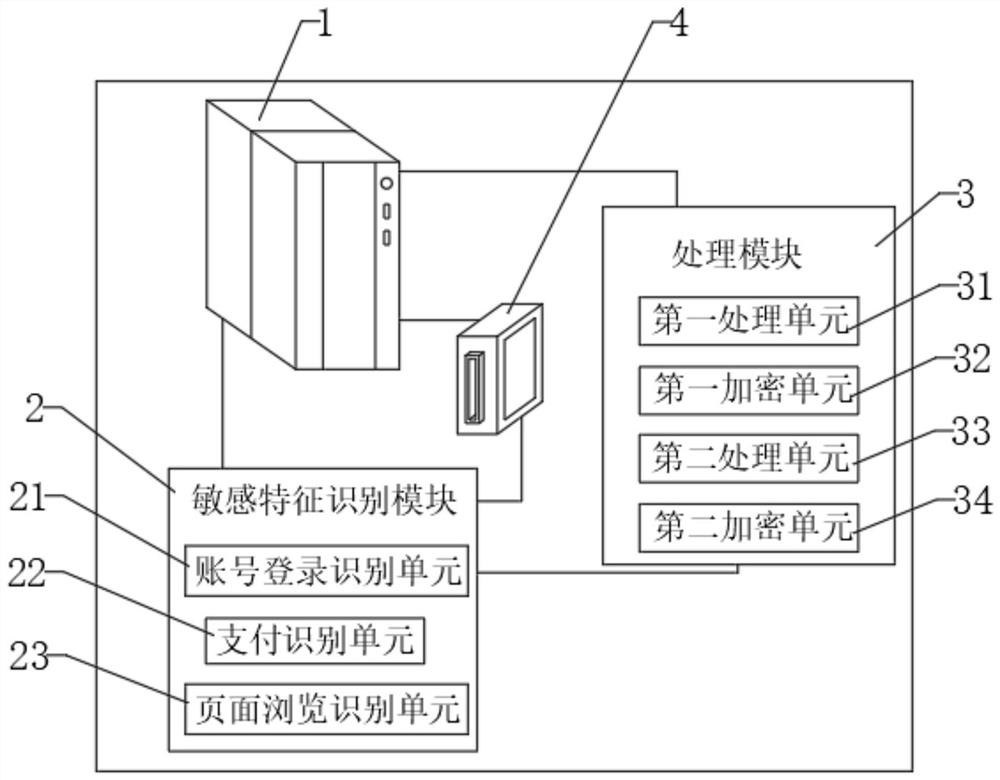
[0045] Example 2, please refer to figure 2 , in the second embodiment, the monitoring of user page browsing is increased more than that in the first embodiment, and the sensitive feature identification module 2 further includes a page browsing identification unit 23; the page browsing identification unit 23 is used for browsing duration and browsing time. After the user's payment habits become stable, the browsing time and the number of browsing times will also be relatively stable, so the probability of payment within the average browsing time and number of browsing is also greater.
[0046] The account login identification unit 21 is also used to obtain the IP address when the user logs in. Generally, the user will pay in a familiar place and within a comfortable time period, so the IP address used is also very important. When the user logs in the IP address. If it belongs to the address that has been registered the longest at the time of payment, the possibility of payment...
Embodiment 3
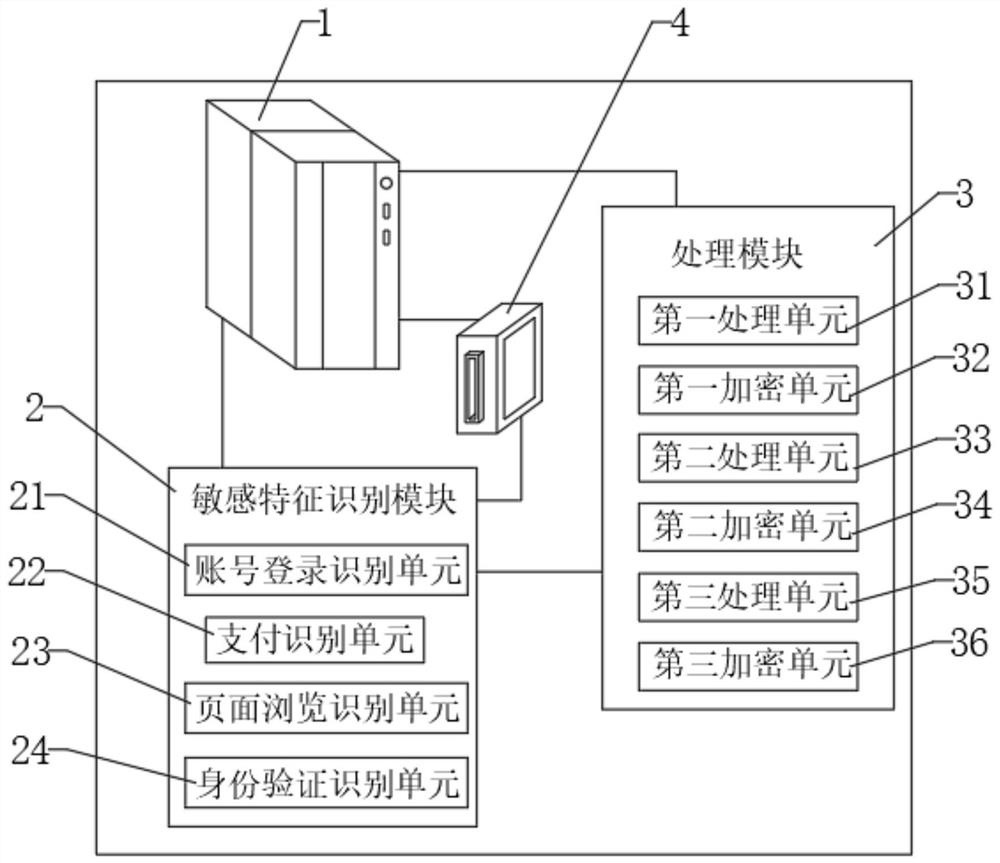
[0054] Example three, please refer to image 3 , compared with the second embodiment, in the third embodiment, the acquisition and processing of identity verification-related data is added, and the sensitive feature identification module 2 also includes an identity verification and identification unit 24; the identity verification and identification unit 24 is used to obtain the identity verification. The verification code data and physical identification data at the time of verification, the general user has a great probability of payment behavior when performing verification code verification and physical identification.
[0055] The processing module 3 includes a third processing unit 35; respectively counts the frequency of the verification code data and the physical sign identification data of the user when payment occurs, and records the frequency of the verification code appearance and the physical sign identification appearance frequency respectively, and counts the abo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com