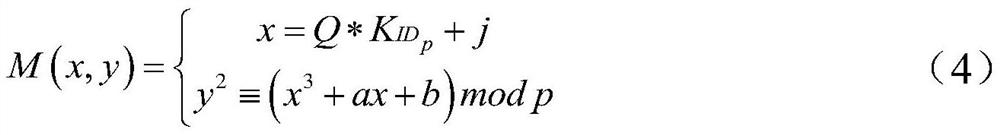Internet of Things equipment identity security authentication method based on block chain and fog computing
A security authentication technology for IoT devices, which is applied in the field of IoT device identity security authentication based on blockchain and fog computing, can solve problems such as not considering device authentication, limited device resources, increasing difficulty, etc., and achieves a good algorithm Safety, ensure safe communication, ensure real effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
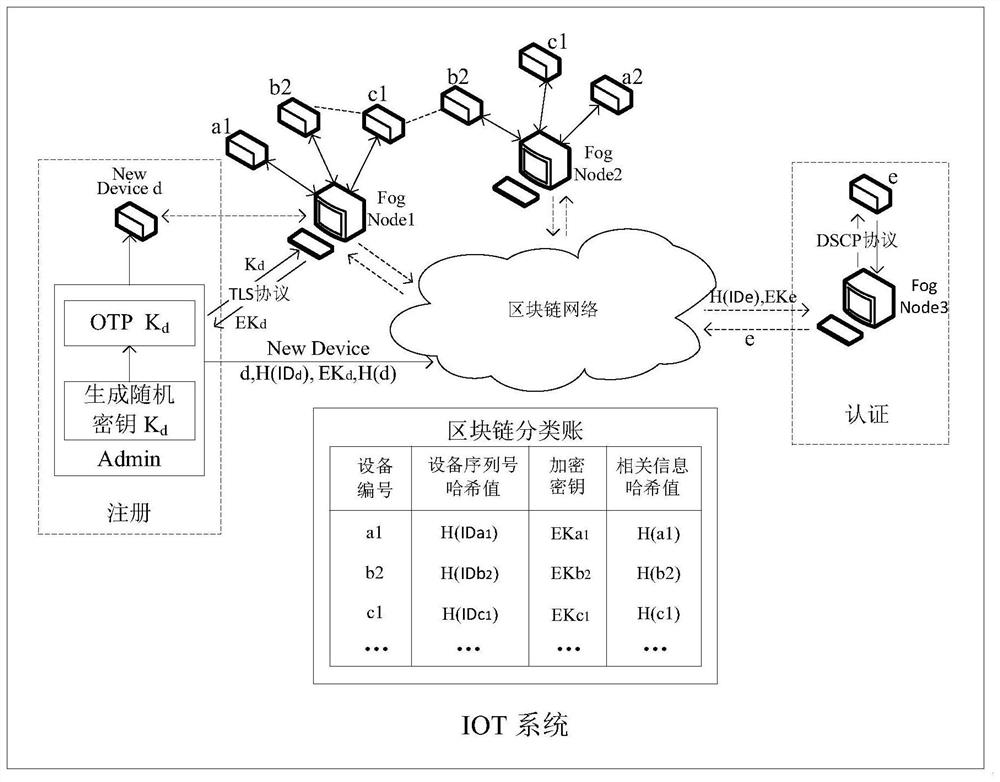
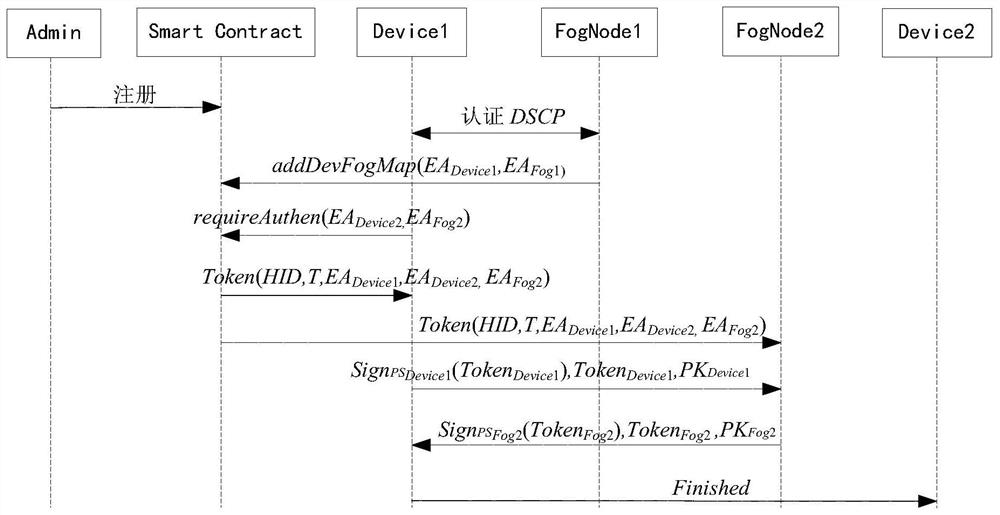
[0057] The present invention is based on block chain and fog computing IoT device identity security authentication method, such as figure 1 As shown, the specific steps are as follows:
[0058] Step 1, use the elliptic curve algorithm ECC to generate the key pairs required by the device manager Admin, the IoT device Device and the fog node FogNode; specifically:
[0059] Choose an elliptic curve y 2 ≡x 3 +ax+b(modp), p is a prime number, construct an elliptic curve Abel group E p (a,b), at E p In (a,b), select generator point G=(x 0 ,y 0 ), G is an n-order subgroup generating element basis point, satisfying nG=O, O is an infinite point, a and b are y 2 ≡x 3 Coefficient of +ax+b, 4a 3 +27b 2 ≠0. Let the private key be a random number d, the range of d is [1,n-1], n is the order of the subgroup, the public key generated by the random...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com