Data quality monitoring method and system and computer equipment
A data quality and monitoring system technology, applied in the Internet field, can solve problems such as inability to notify business personnel of problematic or wrong data, inability to verify data quality in time, and invalidity of data processing, so as to achieve data integrity and avoid information burying , Guarantee the effect of data quality monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0045] Below, will refer to Figure 1 to Figure 3 Embodiments of the data quality monitoring method of the present invention are described.
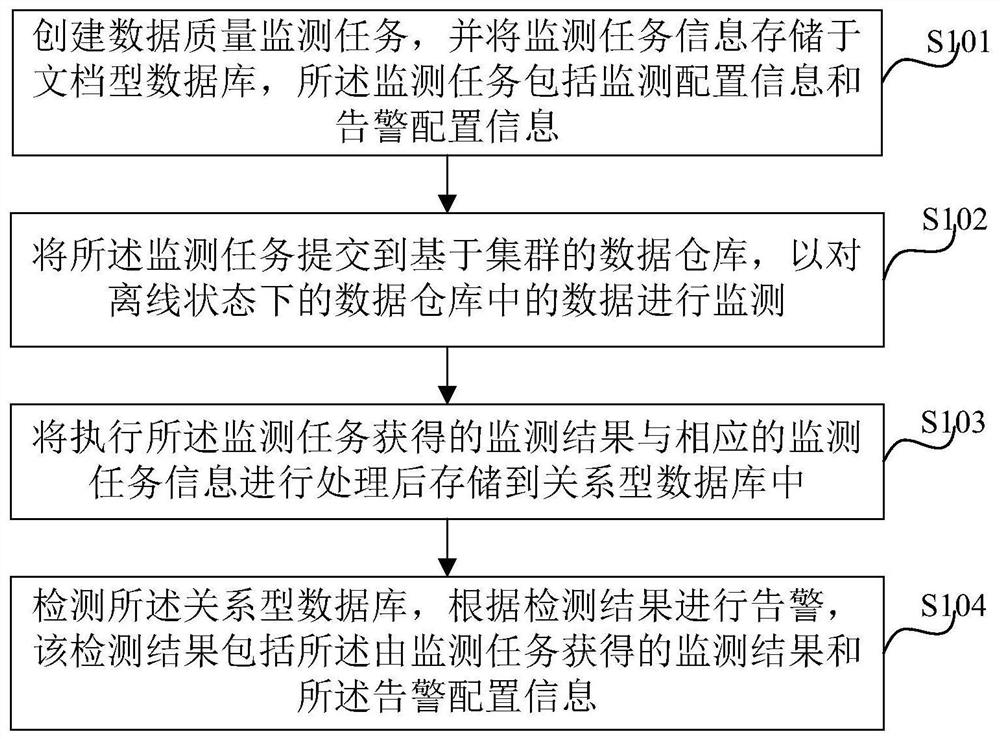
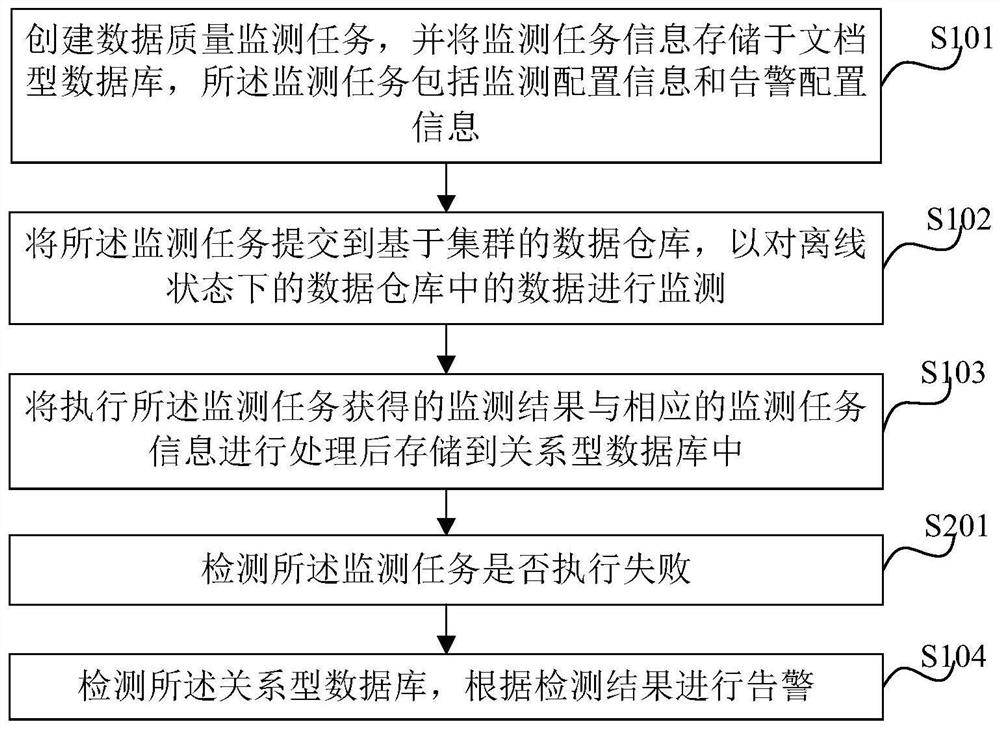
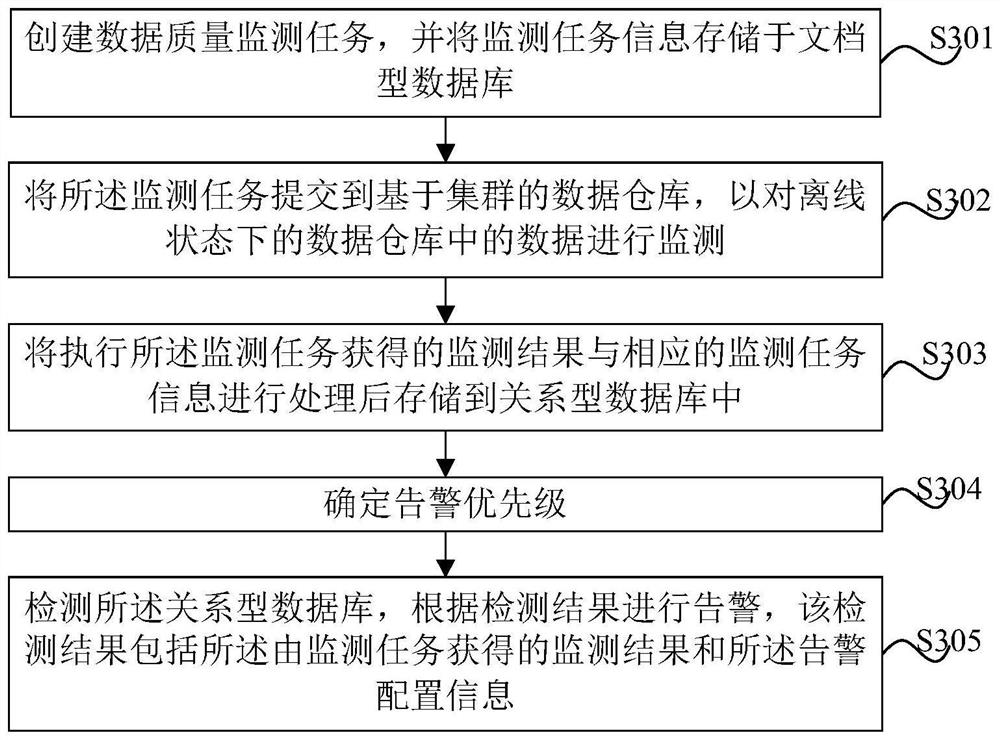
[0046] figure 1 It is a flowchart of an example of the data quality monitoring method of the present invention. Such as figure 1 As shown, the method includes the following steps.
[0047] Step S101, creating a data quality monitoring task, and storing the monitoring task information in a document database, the monitoring task information including monitoring configuration information and alarm configuration information.
[0048] Step S102, submit the monitoring task to the cluster-based data warehouse, so as to monitor the data in the offline data warehouse.
[0049] In step S103, the monitoring result obtained by executing the monitoring task and the corresponding monitoring task information are processed and stored in the relational database.
[0050] Step S104, detecting the relational database, and issuing an alarm according to...
Embodiment 2
[0114] The system embodiment of the present invention is described below, and the system can be used to implement the method embodiment of the present invention. The details described in the system embodiments of the present invention should be regarded as supplements to the above method embodiments; details not disclosed in the system embodiments of the present invention can be implemented by referring to the above method embodiments.
[0115] refer to Figure 4 , Figure 5 with Image 6 , the present invention also provides a data quality monitoring system 400, which is used to monitor the data quality of an offline data warehouse, the data quality monitoring system 400 includes: a creation module 401, used to create a data quality monitoring task, and the The monitoring task information is stored in the document database; the monitoring module 402 is configured to submit the monitoring task to the cluster-based data warehouse to monitor the data in the offline data wareho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com