Security test method and system for mobile terminal applications
A security testing and application technology, applied in software testing/debugging, error detection/correction, instruments, etc., can solve the problem that manual testing is difficult to keep up with the speed of business development, so as to solve data source problems, improve efficiency, and satisfy The effect of security testing requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
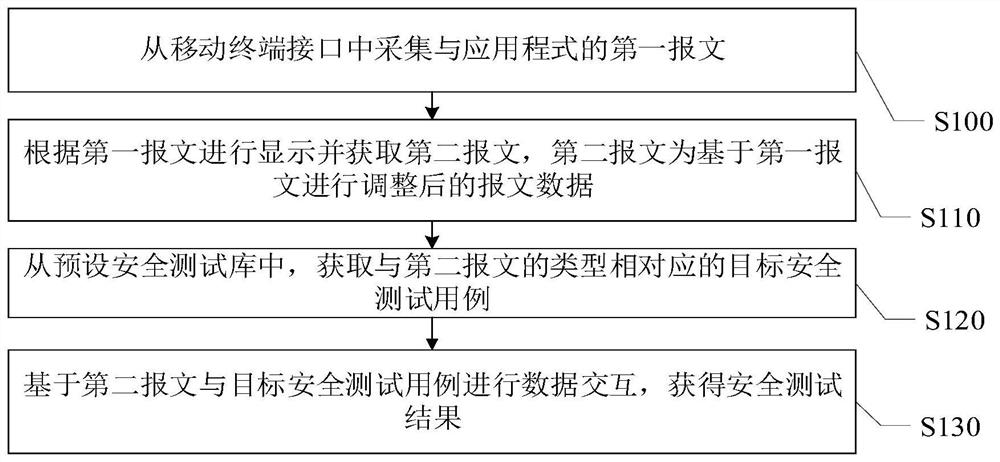
[0034] see figure 1 , figure 1 A schematic diagram of the steps of a security testing method for a mobile application program provided by an embodiment of the present invention, as shown below:
[0035] Step S100, collecting the first message with the application program from the mobile terminal interface;
[0036] In some embodiments, the operating system of the mobile terminal may include operating systems of terminal devices such as an Android (Android) operating system and an Apple mobile phone (IOS) operating system. In order to shield differences between operating systems in one or more embodiments of this specification, corresponding data collection programs may be set in advance according to different types of operating systems.
[0037] By installing the data collection program in the mobile terminal, the first message related to the application program is collected from the interface of the operating system of the mobile terminal through the data collection program...
Embodiment 2
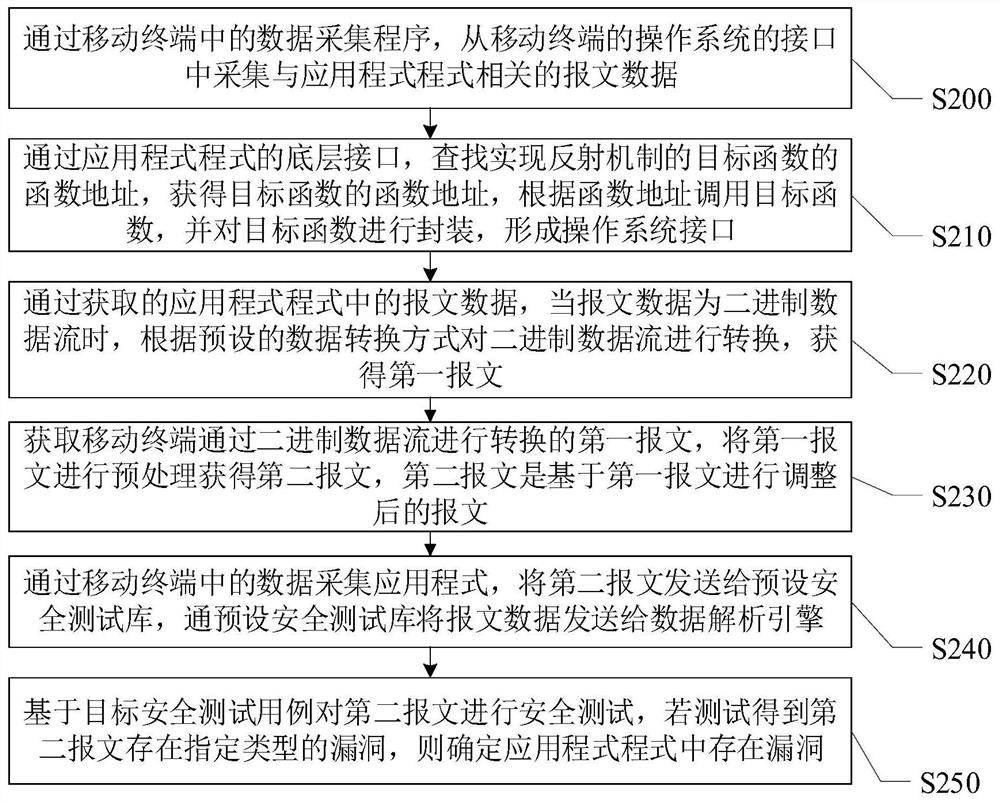
[0046] see figure 2 , figure 2 A schematic diagram of detailed steps of a security testing method for a mobile terminal application program provided by an embodiment of the present invention, as shown below:
[0047] Step S200, through the data collection program in the mobile terminal, collect message data related to the application program from the interface of the operating system of the mobile terminal.
[0048] Step S210, through the underlying interface of the application program, search for the function address of the target function implementing the reflection mechanism, obtain the function address of the target function, call the target function according to the function address, and encapsulate the target function to form an operating system interface.
[0049] Step S220, through the acquired message data in the application program, when the message data is a binary data stream, convert the binary data stream according to a preset data conversion method to obtain ...
Embodiment 3
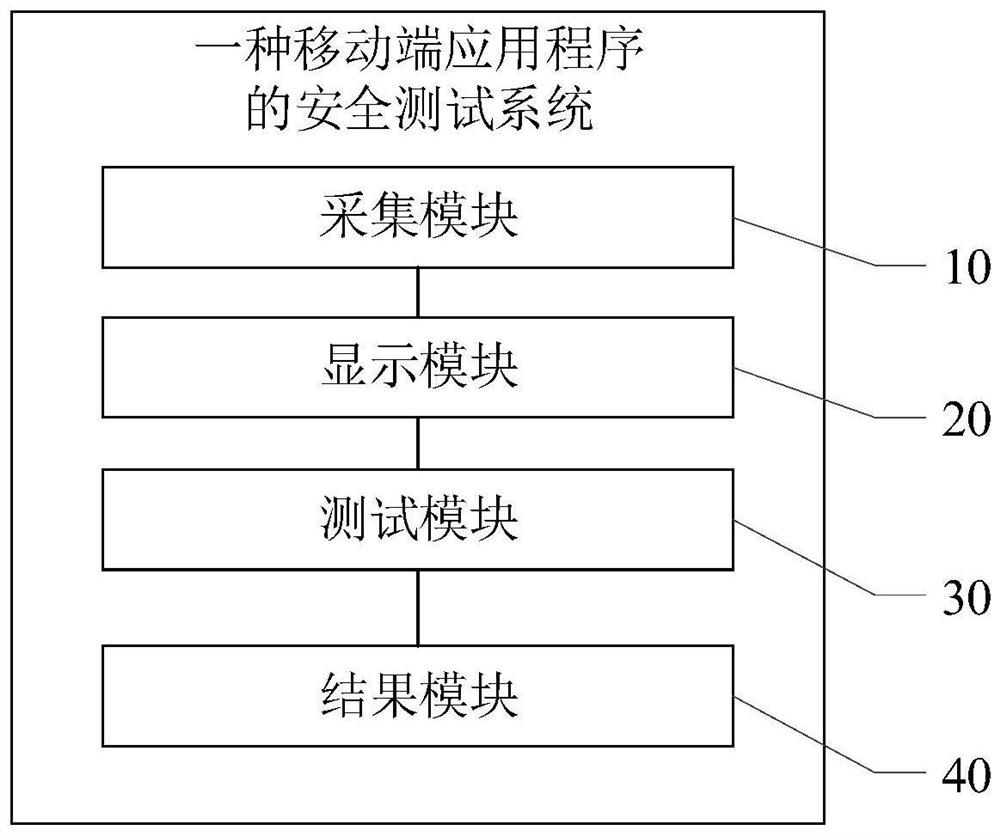
[0055] see image 3 , image 3 A schematic diagram of a security testing system module of a mobile terminal application program provided by the embodiment of the present invention, which is as follows:
[0056] The collection module 10 is used to collect the first message with the application program from the mobile terminal interface;
[0057] A display module 20, configured to display and obtain a second message according to the first message, where the second message is adjusted message data based on the first message;
[0058] A test module 30, configured to obtain a target security test case corresponding to the type of the second message from a preset security test library;
[0059] The result module 40 is configured to perform data interaction with the target security test case based on the second message to obtain a security test result.
[0060] Such as Figure 4 As shown, the embodiment of the present application provides an electronic device, which includes a me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com