Hard disk self-destruction system for preventing computer files from being stolen
A computer and file technology, applied in the protection of internal/peripheral computer components, erasure methods, recording signal processing, etc., can solve problems such as inability to start self-destructing systems, structural security vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
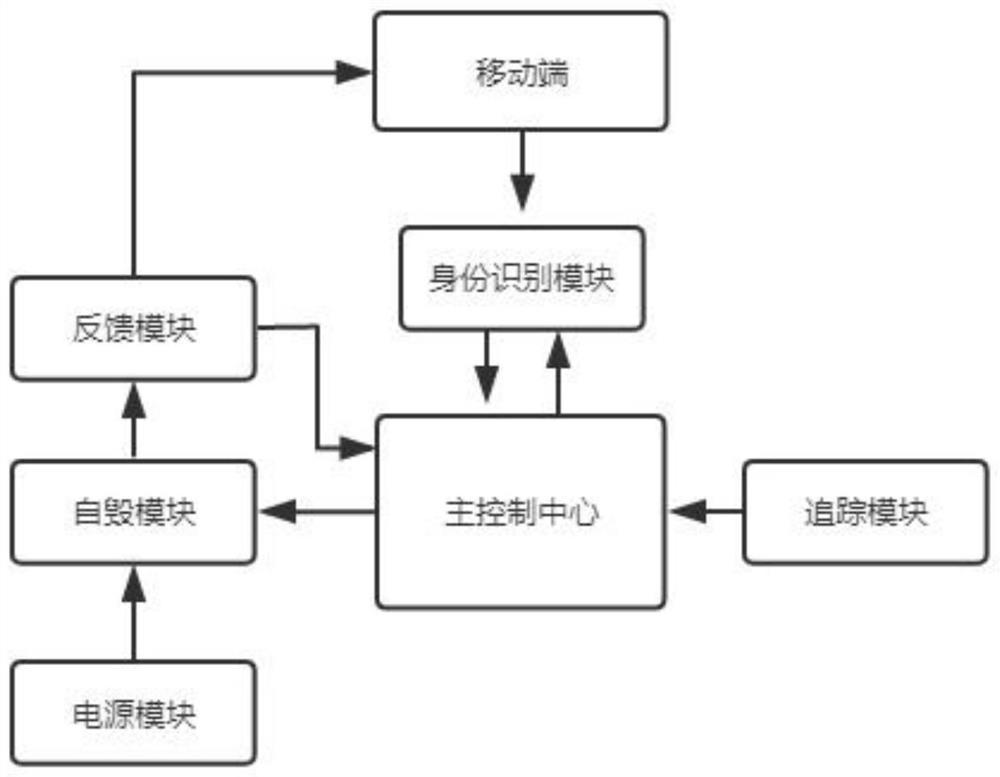
[0034] A hard disk self-destruction system for computer file anti-theft, such as figure 1As shown, it includes a main control center, a mobile terminal, an identification module, a power supply module, a self-destruct module, a feedback module and a tracking module. The main control center is the control core of the self-destruct system, and the main control center is connected to the identification module by communication , the main control center includes a storage module for storing self-destruct program system data; the mobile terminal communicates with the identity recognition module, and the mobile terminal includes but not limited to mobile phones, computers, etc.; the identity recognition module is used to identify the identity of the operator information; the power supply module is electrically connected to the self-destruction module; the self-destruction module is connected to the main control center by communication; the feedback module is respectively connected to ...
Embodiment 2
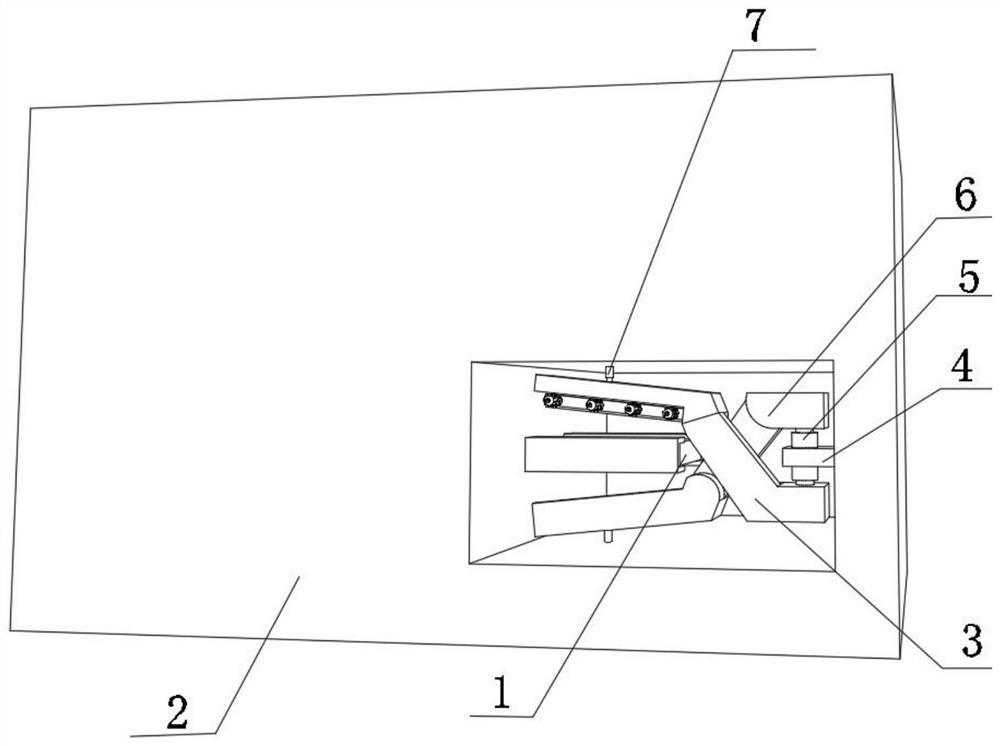
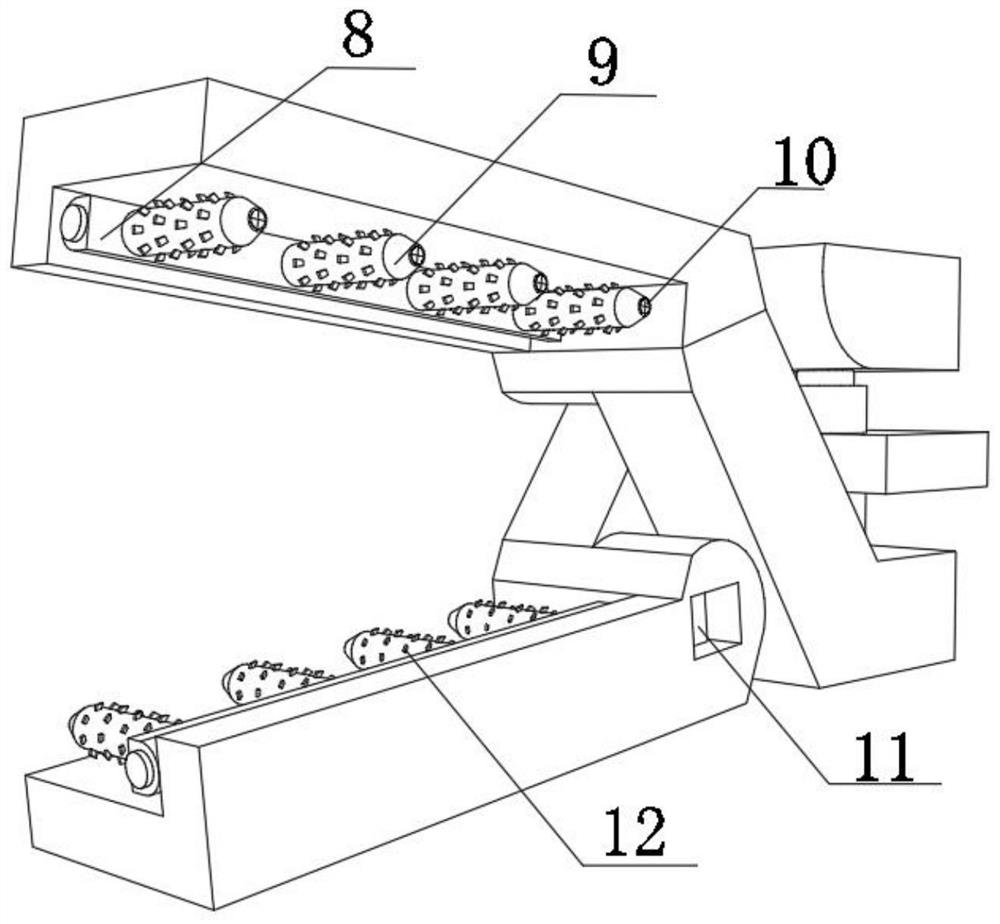
[0044] A kind of anti-theft hard disk self-destruction system for computer files described in embodiment 1, such as Figure 1-5 As shown, in order to prevent criminals from extracting useful files by repairing the disk; this embodiment makes the following improvements on the basis of Embodiment 1: the self-destruction module also includes a self-destruction structure, and the self-destruction structure includes setting The hard disk body 1 on the inner wall of the body 2 and the fixing seat 4 arranged on the inner wall of one side of the body 2, the top outer wall and the bottom outer wall of the fixing seat 4 are all fixed with an electric push column 5 by bolts, and the switch control end of the electric push column 5 It is electrically connected with the main control center. The extension ends of the two electric push columns 5 are respectively fixed with the second connecting rod 6 and the first connecting rod 3 by bolts. The outer wall on one side is rotationally connecte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com