Network asset management method and device, equipment and medium
A technology of network assets and management methods, applied in resources, data processing applications, instruments, etc., can solve problems such as unfavorable key information infrastructure protection, achieve comprehensive and accurate risk classification, and facilitate risk management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
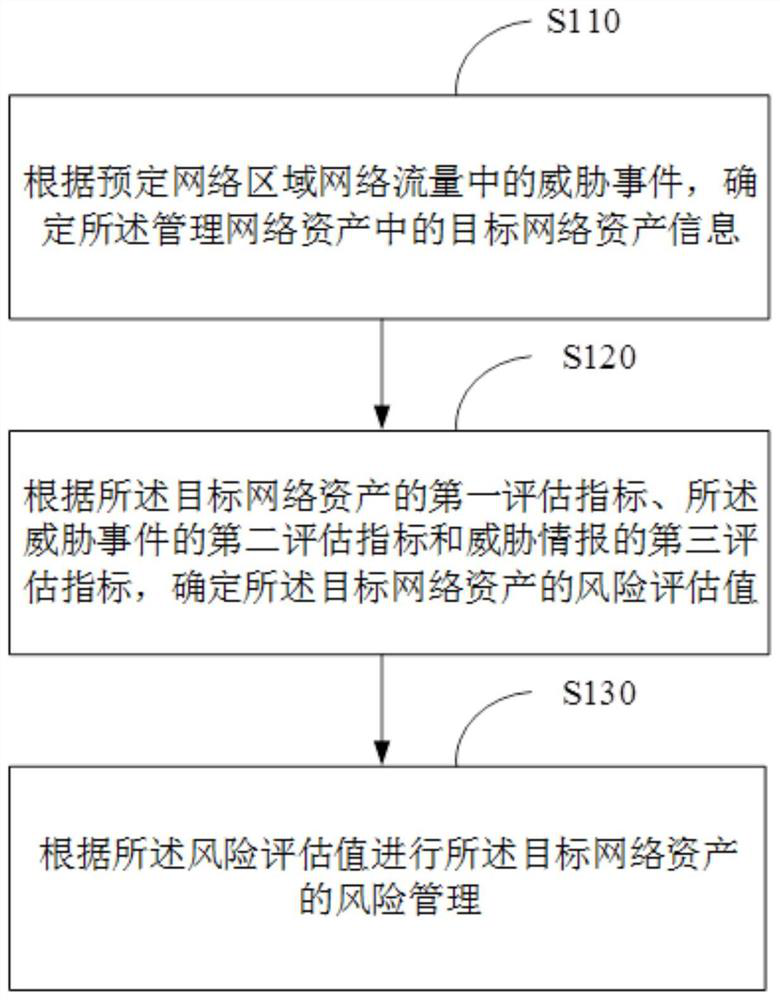
[0029] figure 1 It is a flow chart of a network asset management method provided by Embodiment 1 of the present disclosure, and the method can be executed by a network security event monitoring and analysis system. Among them, the threat attack signature database, network threat information database, network asset information database and threat intelligence database are deployed in the network security event monitoring and analysis system.
[0030] Wherein, the deployed threat attack feature library is used to manage feature information of various network threat attacks and provide various types of network threat attack features. The threat attack feature library contains various types of network threat attack feature information and network attack event monitoring rules. The network attack event monitoring rules are used to detect network attack events in network traffic. The types of monitoring rules include but are not limited to advanced persistent threats ( Advanced Per...
Embodiment 2
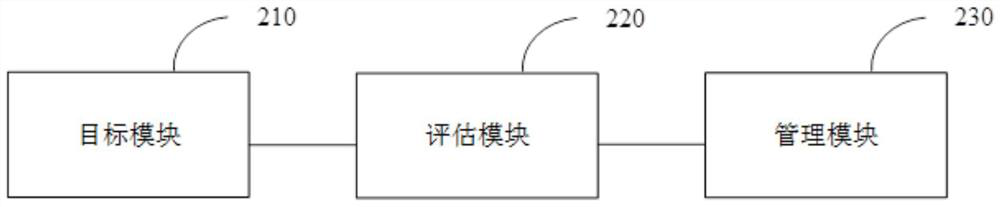
[0070] figure 2 A structural diagram of a network asset management device provided in Embodiment 2 of the present disclosure. The device can execute the network asset management method in Embodiment 1 above, and can be configured in a network security event monitoring and analysis system, such as figure 2 As shown, the apparatus includes an object module 210, an evaluation module 220 and a management module 230, wherein:
[0071] The target module 210 is configured to determine target network asset information in the management network assets according to threat events in network traffic in a predetermined network area, where the predetermined network area includes two or more management network assets.
[0072] The assessment module 220 is configured to determine a risk assessment value of the target network asset according to the first assessment indicator of the target network asset, the second assessment indicator of the threat event, and the third assessment indicator o...
Embodiment 3
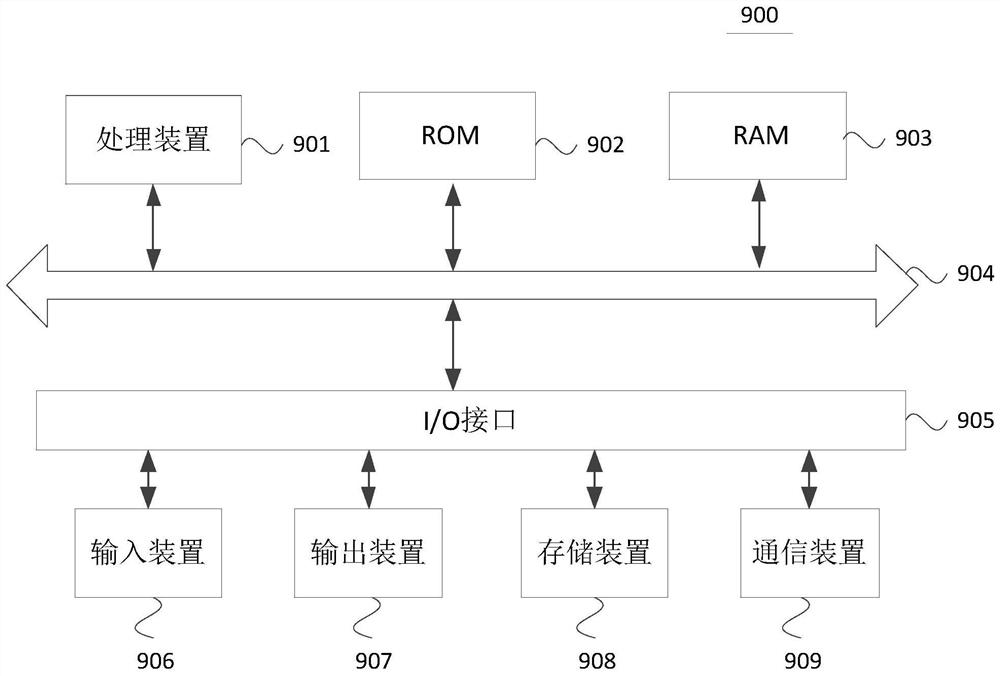
[0083] Refer below image 3 , which shows a structural diagram of an electronic device 900 suitable for implementing the embodiments of the present disclosure. The electronic device in the embodiments of the present disclosure has a network asset management function. image 3 The illustrated electronic device is only an example, and should not impose any limitation on the functions and scope of use of the embodiments of the present disclosure.
[0084] Such as image 3 As shown, the electronic device 900 may include a processing device (such as a central processing unit, a graphics processing unit, etc.) 901, which may be loaded into a random access memory (RAM) according to a program stored in a read-only memory (ROM) 902 or loaded from a storage device 908. ) 903 to perform various appropriate actions and processing. In the RAM 903, various programs and data necessary for the operation of the electronic device 900 are also stored. The processing device 901 , ROM 902 , an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com