Digital key authorization method
A digital key and authorized technology, applied in the field of digital key authorization, can solve problems such as information transmission security transmission, asset risk, user account asset threat, etc., so as to achieve good user experience, avoid the problem of key return, and solve risks and troubles Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
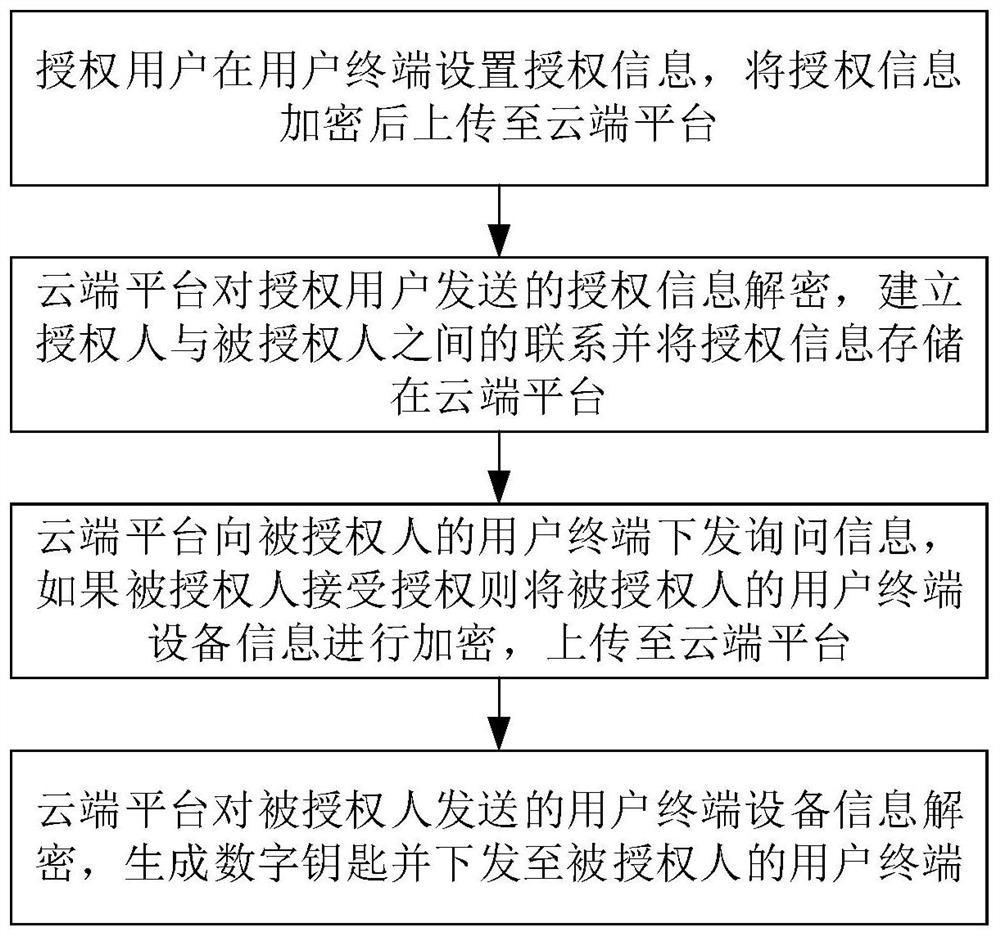
[0028] A digital key authorization method such as figure 1 shown, including the following steps:
[0029] S1. The authorized user sets the authorization information on the user terminal, encrypts the authorization information and uploads it to the cloud platform. The authorization information includes the vehicle information and the identity information of the authorized person;
[0030] Authorization information also includes one or more of authority information, date of use, and number of times of use. Authority information is the user's authority to use the vehicle, such as ignition, trunk opening, and cockpit configuration. The date when the user has the right to use the vehicle, such as June 1, 2021 to June 17, 2021, and the number of uses is the number of legal uses of the vehicle by the user, for example, the number of uses is 10 times.
[0031] In a specific real-time method, the authorized user sets the vehicle information (device number SXXXX), the identity informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com