Lightweight identity authentication key negotiation method for resource-constrained terminal
A technology of identity authentication and key agreement, applied in the field of information security, can solve problems such as key leakage, smart card loss, and weak resource-limited terminals, etc., achieve small system parameters and storage space, fast computing speed, and avoid malicious attacks Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
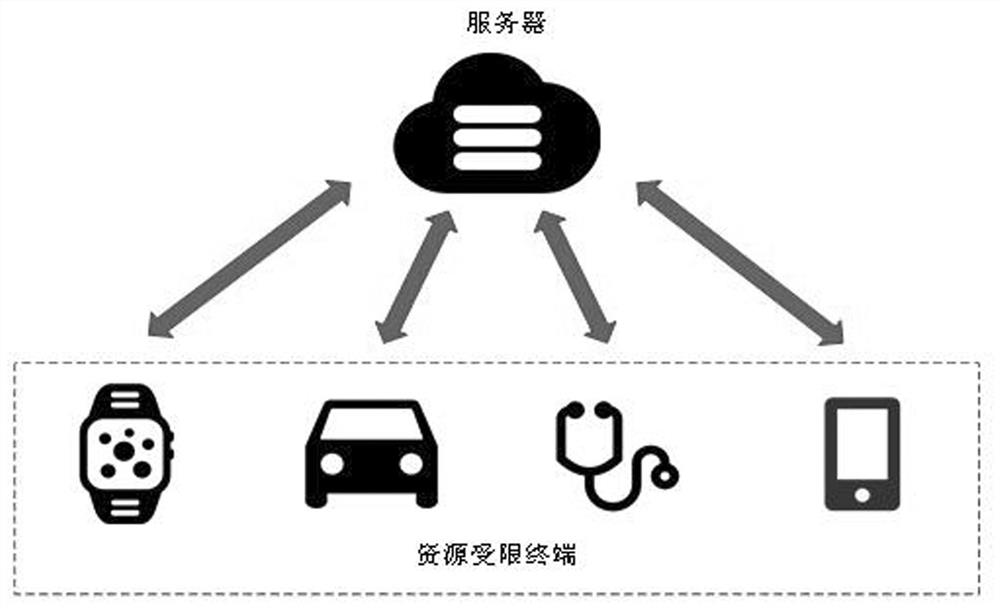
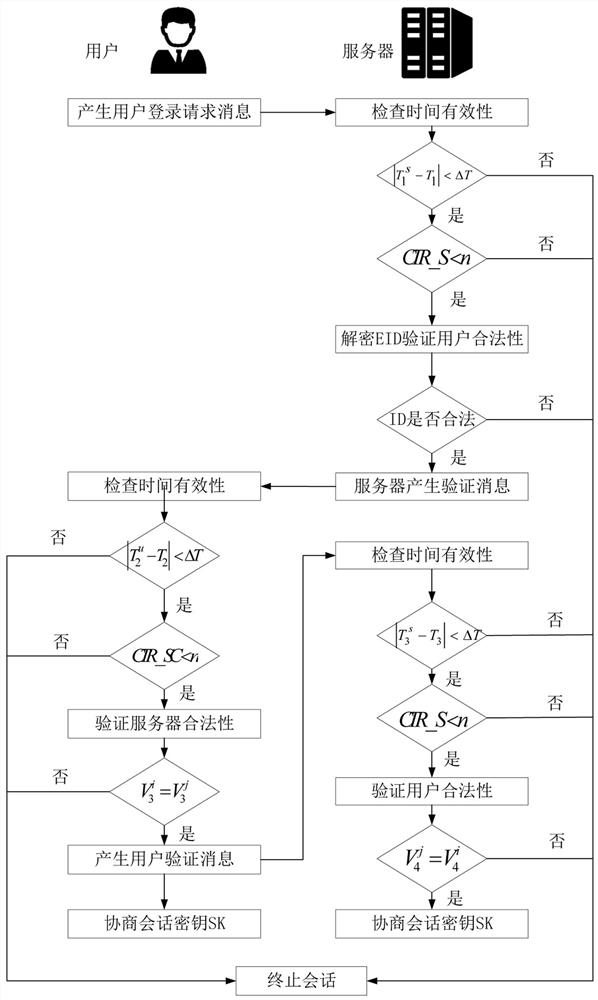
[0033] The invention relates to a lightweight identity authentication key negotiation method for resource-limited terminals. This method has four phases: registration phase, login and authentication phase, password modification phase, smart card revocation phase (such as figure 1 shown). In the scheme, set server S j The counter CTR_S of the user and the counter CTR_SC of the user are used to track the consecutive failed attempts of login and authentication. The initial value is set to 0, and the maximum failure threshold is set to n. When CTR_S>n or CTR_SC>n, the communication process is terminated immediately. The symbols and explanations used in the present invention are shown in the following table:
[0034]
[0035]
[0036] The four stages of this method are described in detail as follows:
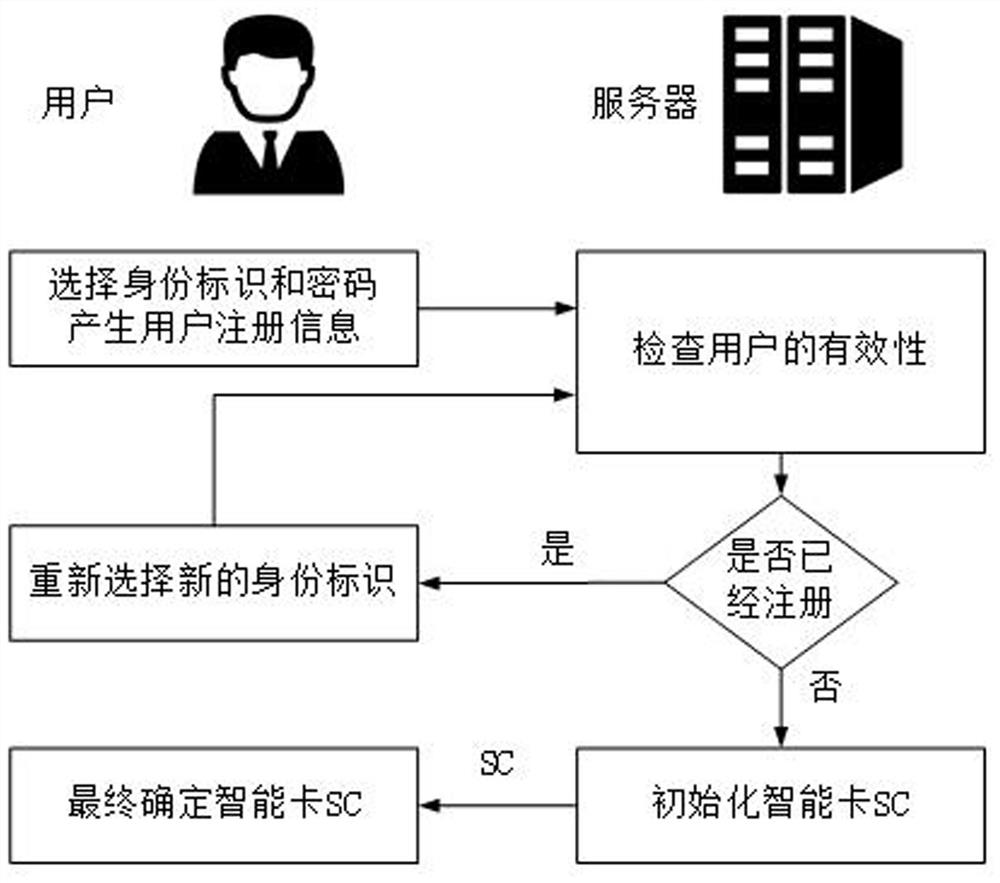
[0037] Phase A: Registration phase (eg figure 2 shown)
[0038] In the registration stage, smart cards are mainly issued to users, so that legal users have legal identit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com