Attack stage prediction method based on LSTM and attacker information
A prediction method, an attacker's technology, applied in prediction, neural learning methods, character and pattern recognition, etc., can solve problems such as dependence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
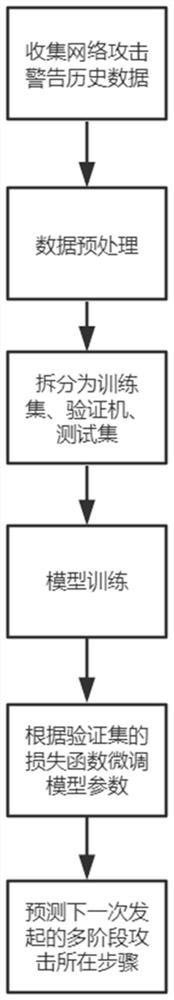
[0035] Such as figure 1 As shown, the specific implementation of this paper is as follows:
[0036] Warning-related data collection: collect network attack warnings fed back by the intrusion detection system of the target asset, and obtain the warning data of the network attack on the target asset for one year, where the input feature vector of the LSTM model is an n×32 matrix, and the n rows of the matrix are respectively It is the relevant data about the network attacks suffered by the target asset in the past n times, and each row is composed of 32 dimensions. Because it is necessary to predict the stage of the next network attack, y is the step number of the next warning in the multi-stage attack chain during training. All dimensions of X in the training set can be divided into three parts.
[0037] The first part consists of the target asset warning data; the second part is the network traffic data at the time of the attack; the third part is the data of the attacker's ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com