Private cloud virtual machine automatic security management method and device, terminal, and storage medium
A security management and virtual machine technology, applied in the fields of private cloud virtual machine automatic security management methods, terminals, storage media, and devices, can solve the problem that security operation and maintenance personnel have limited operation authority, security operation and maintenance personnel cannot assess and reduce security risks, It is impossible to assess and reduce virtual machine security risks, so as to reduce management pressure and comprehensively assess and reduce security risks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
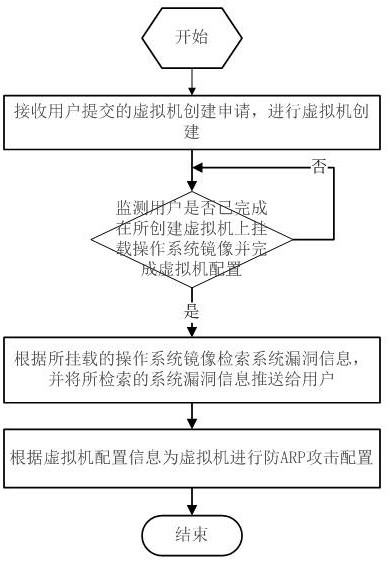
[0053] Private clouds are generally used within enterprises to provide R&D and internal application operation, and their security has attracted more and more attention. At present, the security management of private cloud in the industry generally provides centralized management through the security management module, which usually requires security operation and maintenance personnel to actively perform relevant scanning and configuration operations. On the one hand, in a scenario where there are many virtual machines and complex services, security operation and maintenance personnel cannot timely and on-demand perform relevant security risk assessment and reduction; on the other hand, security operation and maintenance personnel generally have limited operation authority and cannot obtain information about virtual machines It is impossible to conduct a more comprehensive security risk assessment and mitigation for virtual machines without relevant information.
[0054] There...
Embodiment 2
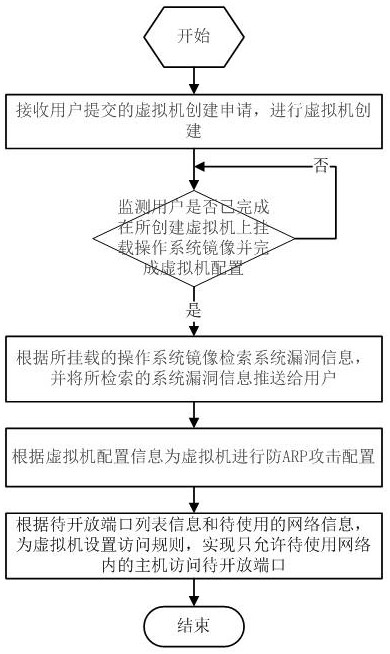
[0062] The security management of the virtual machine is convenient. In some scenarios, the user also needs to ensure the security of access rules, that is, configure the port information that the host can allow access to. Therefore, in the method for automatic security management of a private cloud virtual machine provided in Embodiment 2, when submitting a virtual machine creation application, relevant information is included in the application, and the cloud platform creates the virtual machine at the same time. Compared with the existing technology, security operation and maintenance personnel cannot obtain relevant information, that is, they cannot perform configuration, and when there are a large number of virtual machines, the configuration cannot be completed in time.
[0063] Such as figure 2 Shown is a schematic flowchart of a method for automatic security management of a private cloud virtual machine provided in the second embodiment, including the following steps....
Embodiment 3
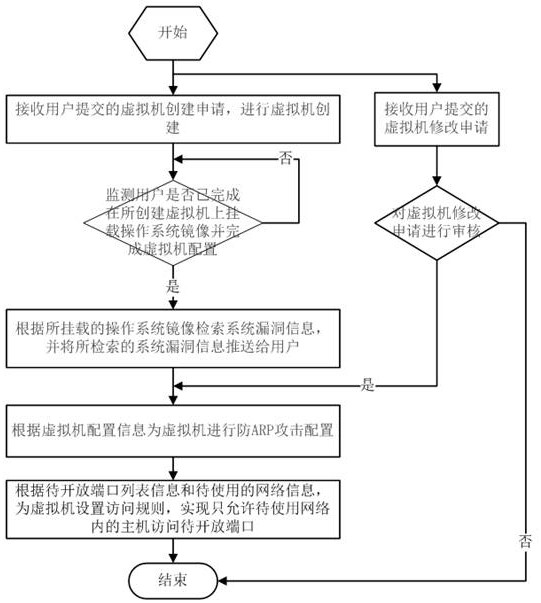
[0087] Considering that the user needs to change the virtual machine during the running process of the virtual machine, in order to ensure the security of the virtual machine, this embodiment also configures security information when the virtual machine is changed.
[0088] Such as image 3 Shown is a schematic flowchart of a method for automatic security management of a private cloud virtual machine provided in the third embodiment, including the following steps.
[0089] S1. Receive a virtual machine creation application submitted by a user, and create the virtual machine.
[0090] Wherein, the virtual machine creation application submitted by the user includes information about a list of ports to be opened and information about a network to be used.
[0091] S2, monitoring whether the user has completed mounting the operating system image on the created virtual machine and completing the configuration of the virtual machine, if completed, perform the following steps, other...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com