Security event closed-loop processing method for network security management
A technology for security events and processing methods, which is applied in data exchange networks, electrical components, digital transmission systems, etc., and can solve the problems of inconsistent security event log types, low processing efficiency, and cumbersome administrator operations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0060] combine figure 1 As shown, a method for closed-loop processing of security events for network security management, including:
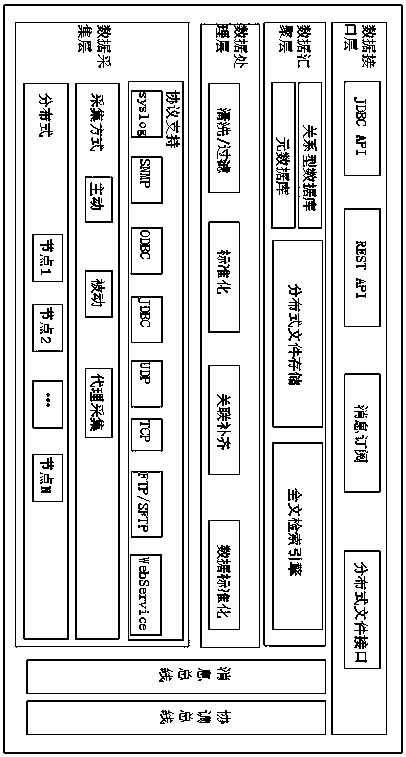
[0061] Step S100: the event collector collects security events and early warning logs from security devices and systems, performs data cleaning / filtering, merging and normalization processing, and stores them in the database;
[0062] Step S200: The system schedules the scanner to scan the protected assets, discovers asset vulnerabilities and obtains asset information, reads the security events and early warning logs from the database, performs correlation analysis between security events and asset vulnerabilities, and analyzes the security events risk rating;
[0063] Step S300: Sending out an alarm for the safety event whose risk is classified as high risk in step S200;
[0064] Step S400: Record and process the alarm;
[0065] Step S500: collect asset vulnerabilities in security devices and systems again, and confirm that the early warnin...
Embodiment 2
[0069] On the basis of Example 1, combined with figure 1 As shown, the step S100 specifically includes:
[0070] Step S110: defining the collection scope, collection capability, data processing and data storage of security events;
[0071] Step S120: the event collector collects security events and early warning logs;
[0072] Step S130: backing up the security event and early warning log;
[0073] Step S140: Perform data standardization processing on the security event and early warning log;
[0074] Step S150: Store the standardized security events and early warning logs in the distributed file system and the distributed retrieval system.
[0075] working principle:
[0076] Centralization of data collection: clear the objects of security data collection, list the data sources for analysis, and store them in a centralized manner; data standardization: the collected raw data is cleaned and filtered, standardized, associated and completed, and data labeled to form standard...
Embodiment 3
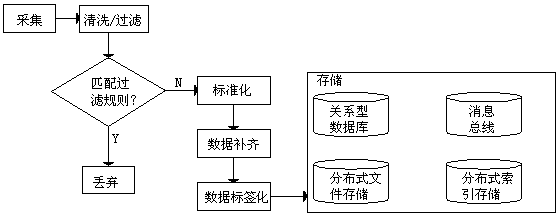
[0081] On the basis of embodiment 2, in conjunction with the attached figure 1 As shown in the figure, the step S140 specifically includes:
[0082] Step S141: data cleaning / filtering, comparing the collected data with the matching rules, and directly discarding the logs matching the filtering rules;
[0083] Step S142: Data standardization, according to the standard library rules of each type of data, realize the standardization of fields;
[0084] Step S143: Add asset information after the standardized data, and complete the association completion;
[0085] Step S144: Add tagging information to the data after association completion to complete data tagging.
[0086] working principle:
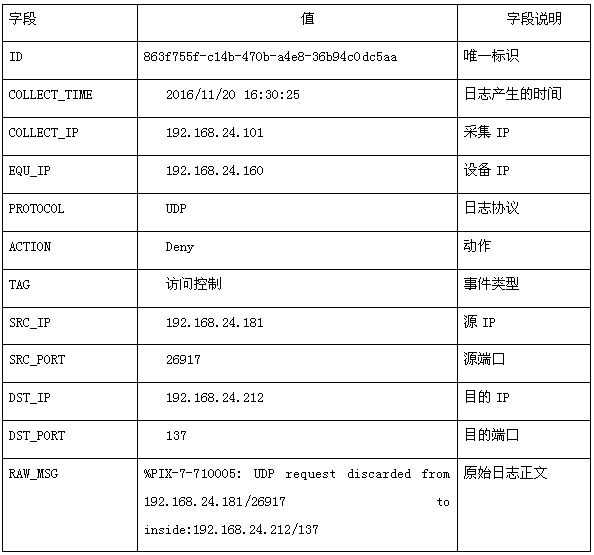
[0087] The data filtered out in data cleaning / filtering includes: data that does not belong to the data source; duplicate data; noise data; data with incomplete or irrational data; data below the minimum level of business requirements. Take the firewall log as an example: %PIX-7-710005: U...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com