Baseline checking and reinforcing method and system aiming at NTLM protocol attack
A protocol and baseline technology, applied in the field of baseline inspection and hardening, which can solve the problems of low security of NTLMv1
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0035]It should be noted that the structures, proportions, sizes, etc. shown in this specification are only used to cooperate with the content disclosed in the specification for the understanding and reading of those familiar with this technology, and are not used to limit the conditions for the implementation of the present invention , any modification of structure, change of proportional relationship or adjustment of size shall still fall within the scope covered by the technical content disclosed in the present invention without affecting the effect and purpose of the present invention. .
[0036] At the same time, terms such as "upper", "lower", "left", "right", "middle" and "one" quoted in this specification are only for the convenience of description and are not used to limit this specification. The practicable scope of the invention and the change or adjustment of its relative relationship shall also be regarded as the practicable scope of the present invention without ...
Embodiment 1
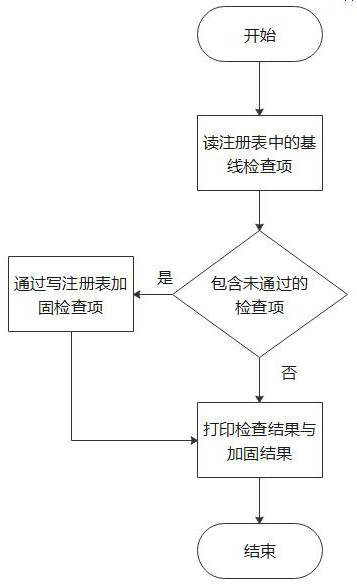
[0038] Such as figure 1 As shown, the method and system for baseline inspection and reinforcement of NTLM protocol attacks, the method includes:
[0039] Call the entries related to NTLM protocol security in the registry;
[0040] Based on the security-related items, determine whether each security baseline against NTLM protocol attacks is compliant;
[0041] Choose non-compliant security baselines;
[0042] Perform security hardening on non-compliant security baselines.
[0043] Among them: In the Windows system, the system realizes the configuration of the system security policy through the registry. NTLM is an authentication protocol commonly used in Windows systems, but there are various attack methods against NTLM, especially the relay attacks on NTLM protocol. This method is applied to the Windows operating system to resist and mitigate the attacks of the NTLM protocol.
[0044] First, by analyzing the characteristics of the NTLM protocol attack and the weak parts o...
Embodiment 2
[0058] This embodiment two is applied to the method and system for baseline inspection and reinforcement against NTLM protocol attacks described in embodiment one. The meaning and specific configuration of the baseline inspection items involved in this method are as follows:
[0059] The key DisableLoopbackCheck of the registry key HKLM\SYSTEM\CurrentControlSet\Control\Lsa is used to indicate whether the system uses LSASS cache Challenge to prevent reflection attacks.
[0060] Whether the SMB service is enabled with signature settings, the registry key:
[0061] The EnableSecuritySignature and RequireSecuritySignature keys in HKLM\System\CurrentControlSet\Services\LanmanServer\Parameters can effectively prevent the NTLM protocol relay attack in the SMB protocol.
[0062] Whether the LDAP server is signed, the registry key:
[0063] The ldapserver integrity in HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\NTDS\Parametershive controls the LDAP signature policy. For the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com