Mimicry intrusion-based vulnerability detection method and system and storage medium thereof
A vulnerability detection and vulnerability technology, applied in the field of electronic communication, can solve problems affecting the normal operation of applications or systems, false positives of vulnerabilities, etc., and achieve the effect of reducing test request information, improving accuracy, and contributing to normal operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
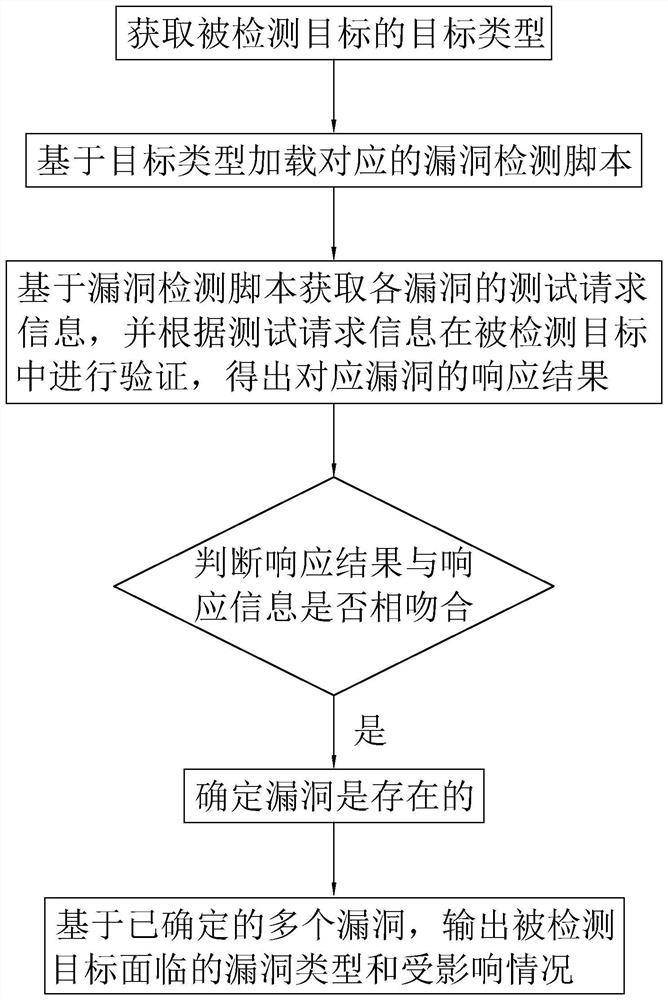
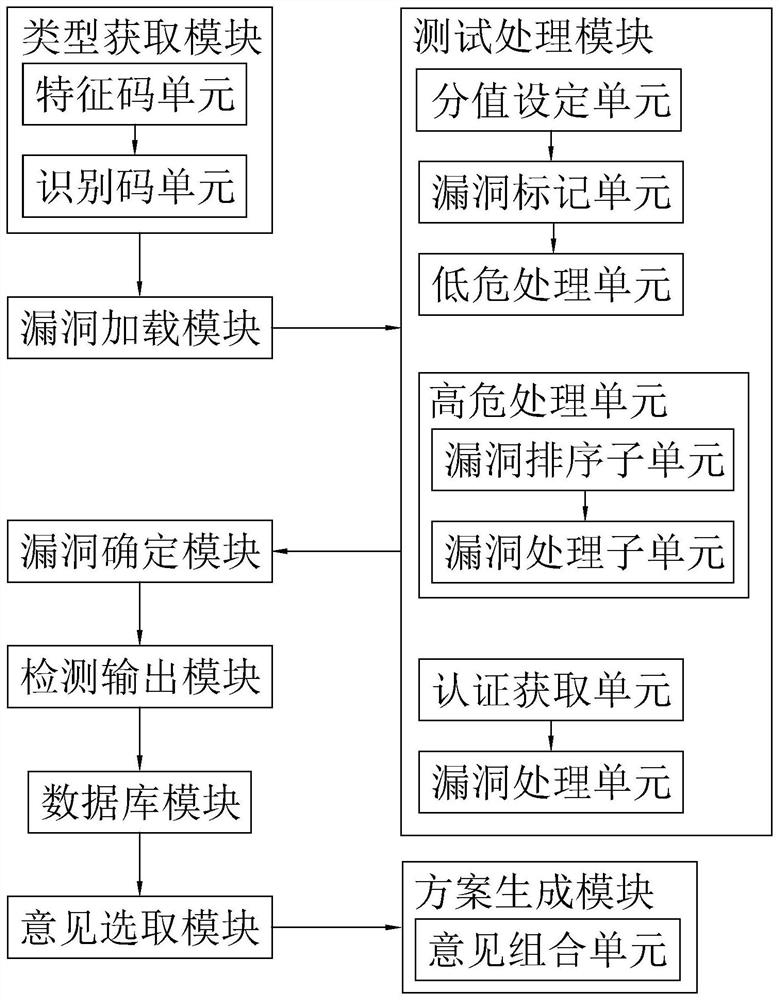
[0057] In order to make the purpose, technical solutions and advantages of this application clearer, the following in conjunction with the attached Figure 1-2 And embodiment, this application is described in further detail. It should be understood that the specific embodiments described here are only used to explain the present application, not to limit the present application.
[0058] The embodiment of this application discloses a vulnerability detection method based on mimic intrusion, refer to figure 1 , including the following steps:
[0059] S1. Obtain the target type of the detected target.
[0060] Before the step of obtaining the target type of the detected target, it also includes:
[0061] S11. Obtain the feature code of the detected target.
[0062] It should be noted that the detected target may be an application program or a webpage system. Generally, the application program will contain some feature codes more or less in the html, js, css and other files. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com