Log collection method, system and device
A collection method and log technology, applied in the field of cloud computing, can solve problems such as waste of computer resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
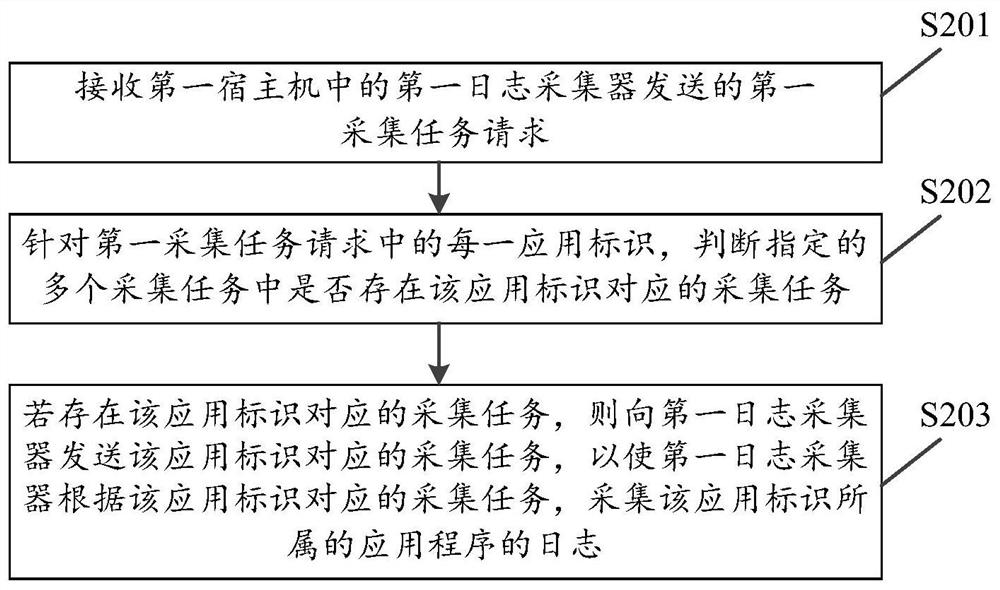
[0067] Embodiment one, see figure 2 , figure 2 It is a flow chart of a log collection method provided by an embodiment of the present invention, and the method may include the following steps:
[0068] S201: Receive a first collection task request sent by a first log collector in a first host computer.
[0069] The first collection task request includes application identifiers of deployed application programs in containers in the first host machine.
[0070] S202: For each application identifier in the first collection task request, determine whether there is a collection task corresponding to the application identifier among the specified collection tasks.
[0071] S203: If there is a collection task corresponding to the application identifier, send the collection task corresponding to the application identifier to the first log collector, so that the first log collector collects the collection task corresponding to the application identifier according to the collection t...
Embodiment 2
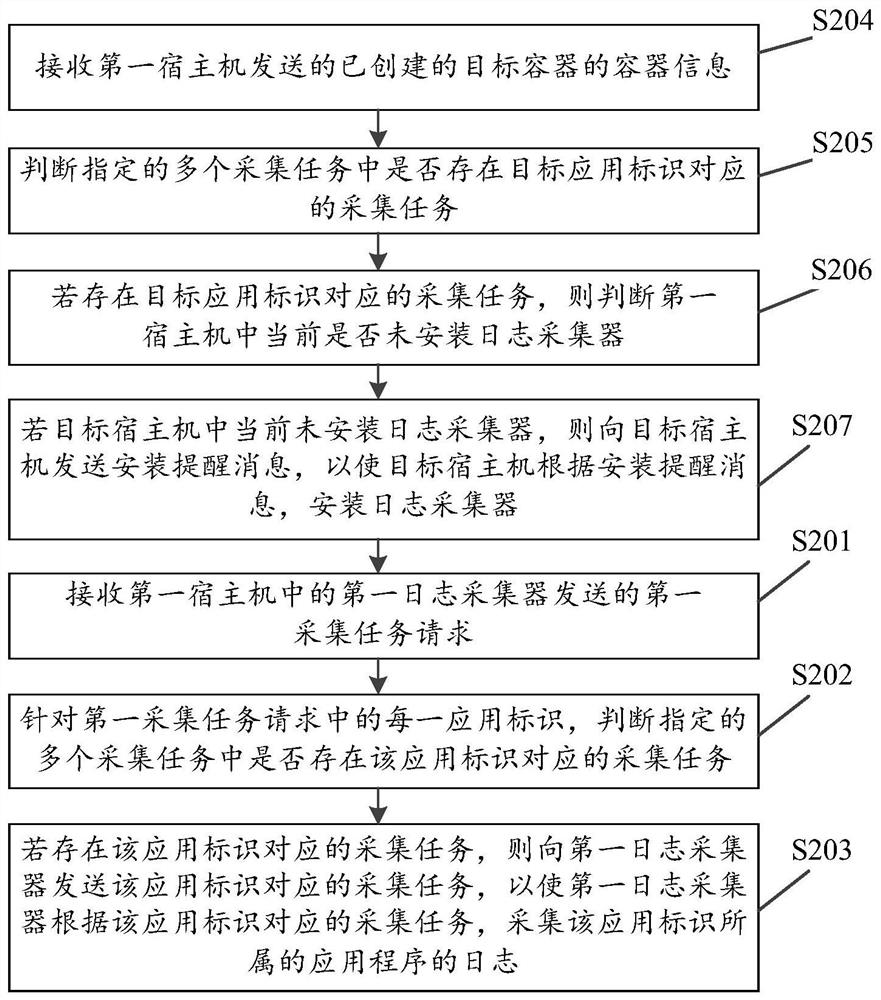
[0078] Embodiment two, see image 3 ,exist figure 2 On the basis of, before step S201, the method may also include:
[0079] S204: Receive container information of the created target container sent by the first host computer.
[0080] S205: Determine whether there is a collection task corresponding to the target application identifier among the specified multiple collection tasks.
[0081] S206: If there is a collection task corresponding to the target application identifier, determine whether the log collector is currently not installed in the first host machine.
[0082] S207: If the log collector is not currently installed in the first host, send an installation reminder message to the first host, so that the first host installs the log collector according to the installation reminder message.
[0083] Wherein, the container information includes the target application identifier of the target application deployed in the target container.
[0084] In an implementation m...
Embodiment 3
[0088] Embodiment 3, judging whether the log collector is currently not installed in the first host machine, including:
[0089] Step 1: Determine whether the collection task request sent by the log collector in the first host computer is received within the preset historical time period.
[0090] Step 2: If the collection task request sent by the log collector in the first host computer is not received, it is determined that no log collector is currently installed in the first host computer.
[0091] In an implementation manner, the log collector can send a collection task request to the control server according to a preset period, and the preset period can be set by a technician according to business requirements. For example, the preset period can be 10 seconds, or the preset period can be 10 seconds, or The period may be 30 seconds, which is not limited here. The preset historical time period may be a preset period before the current moment.
[0092] In an implementation m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com